Gestión de exposición: cómo anticiparse al riesgo cibernético
La función de la gestión de exposición en la creación de programas de ciberseguridad
La gestión de exposición proporciona una visión amplia a lo largo de la superficie de ataque moderna para que pueda comprender mejor el riesgo cibernético de su organización y tomar decisiones de negocios más fundamentadas. Al comprender cómo es su superficie de ataque y dónde tiene el mayor riesgo, sus equipos de TI y seguridad podrán abordar con mayor eficacia las vulnerabilidades y otras exposiciones desde un punto de vista técnico y de negocios.
En esta base de conocimientos, examine en mayor detalle qué es la gestión de exposición y cuál la función de la gestión de vulnerabilidades basada en el riesgo, y explore de qué manera protege a su organización de los ataques cibernéticos.
Más información acerca de lo siguiente:
Los siete beneficios de una plataforma de gestión de exposición
Una plataforma completa de gestión de exposición puede ofrecerle la visibilidad que necesita para reducir el riesgo cibernético sin herramientas dispares que aíslen en silos los datos de seguridad críticos.
Más informaciónObtenga visibilidad, prevenga ataques y comunique el riesgo
De qué manera el contexto predictivo de las amenazas y las métricas objetivas ayudan a prevenir ataques cibernéticos
Más informaciónPreguntas frecuentes sobre la gestión de exposición
¿Tiene preguntas sobre la gestión de exposición? Vea estas preguntas frecuentes.
Más información¿Cómo desarrollar un programa de gestión de exposición?
Con cinco pasos, tendrá todo listo para crear un programa de gestión de exposición.
Más informaciónÚnase a la comunidad de gestión de exposición
Únase a otros profesionales interesados en obtener más información sobre la gestión de exposición.
Más informaciónBeneficios de la gestión de exposición
Explore algunas de las muchas ventajas de una estrategia de gestión de exposición.
Más informaciónElección de una solución de gestión de exposición
Estos son algunos de los aspectos que debe buscar en una solución de gestión de exposición.
Más informaciónAnticípese a los ataques y reduzca el riesgo de manera proactiva
Tenable One es la única plataforma de gestión de exposición que necesitará para obtener una vista única y unificada de su superficie de ataque moderna. Con Tenable One, podrá anticiparse a las consecuencias de los ataques cibernéticos, y abordar y gestionar de manera proactiva el riesgo cibernético de todos sus activos, en cualquier lugar.
Información sobre la gestión de exposición
Estudio sobre la exposición cibernética de Tenable: cómo defenderse contra el ransomware
Los agentes maliciosos cuentan con la probabilidad de que su organización no haya corregido las vulnerabilidades de software comunes y conocidas. Desean usar esas exposiciones para infiltrarse en sus sistemas, frecuentemente con la intención maliciosa de infectar sus activos con ransomware.
Muchas infecciones de ransomware se originan en estas vulnerabilidades y en un lugar que los equipos de seguridad suelen pasar por alto: su Active Directory (AD).
Si los atacantes pueden explotar con éxito una sola deficiencia de seguridad en Active Directory, podrán escalar privilegios fácilmente. Si su organización también tiene una higiene cibernética deficiente, hay muchas posibilidades de que los atacantes obtengan fácilmente un punto de incursión en su superficie de ataque y propaguen el ransomware.
Así que, ¿qué puede hacer? Explore este estudio de Tenable para obtener más información sobre los siguientes temas:
- Vectores de ataque y exploits más afectados.
- Cómo priorizar la corrección para centrarse en las vulnerabilidades que plantean la mayor amenaza para su organización.
- De qué manera Tenable One puede ayudarle a identificar las vulnerabilidades y otras exposiciones de Active Directory (AD).
Informe de Gartner: How to grow vulnerability management into exposure management
Priorizar una lista interminable de vulnerabilidades critical o high (críticas o altas) nunca derivará en una solución procesable para su problema de exposición cibernética, especialmente si todavía usa herramientas tradicionales de puntuación de vulnerabilidades y prácticas de gestión de vulnerabilidades tradicionales.
La realidad es que los abordajes actuales para la gestión de superficie de ataque no están a la altura de los vastos y complejos entornos actuales, que requieren virar hacia una gestión de vulnerabilidades basada en el riesgo.
Este abordaje de gestión de la exposición a amenazas continua va más allá de la mera evaluación del riesgo cibernético. Los programas maduros de gestión de vulnerabilidades también deben comprender las amenazas cibernéticas en el contexto de negocios. Esto es fundamental para la gestión de exposición, y sus estrategias de priorización y corrección.
En este informe de gestión de vulnerabilidades de Gartner, se detalla cómo puede hacer evolucionar su programa de gestión de vulnerabilidades hacia la gestión de exposición. Siga leyendo para saber cómo lograr los siguientes objetivos:
- Definir el alcance y la cadencia de las evaluaciones de vulnerabilidad.
- Mejorar la detección de activos para incluir los activos digitales y en la nube.
- Usar estrategias de priorización y validación para centrarse en las exposiciones que los agentes maliciosos explotan activamente.
- Cómo incorporar sus procesos de gestión de riesgo a los flujos de trabajo existentes y trabajar de forma más colaborativa entre los equipos.
De qué manera los desafíos de las personas, los procesos y la tecnología perjudican a los equipos de ciberseguridad
Tenable encargó un estudio a Forrester para obtener la opinión de más de 800 profesionales de TI y ciberseguridad sobre cómo los desafíos relacionados con las personas, los procesos y la tecnología dificultan las estrategias de reducción de riesgos.
En dicho informe se destaca la importancia de por qué las organizaciones deben pasar de la seguridad reactiva a la preventiva.
Algunos de los hallazgos clave son los siguientes:
- La organización promedio se defendió de manera preventiva contra menos del 60 % de los ataques cibernéticos en los últimos dos años.
- Más de la mitad de los responsables de TI y seguridad afirma que la infraestructura en la nube es la mayor exposición de su organización.
- Seis de cada diez profesionales de ciberseguridad y TI dice que sus equipos de seguridad están demasiado ocupados luchando contra incidentes críticos como para adoptar un abordaje preventivo hacia la reducción de la exposición.
Lea este informe para obtener más información sobre los siguientes temas:
- Las herramientas de ciberseguridad más utilizadas.
- Necesidad de más recursos de ciberseguridad.
- Complejidades de la seguridad en la nube pública, privada e híbrida, y multinube.
Cinco pasos para priorizar la exposición real para el negocio
A los atacantes no les importan sus silos de negocios. De hecho, esperan que haya desconexiones entre sus equipos de TI y de seguridad. La seguridad aislada en silos es una evolución natural de la rápida adopción tecnológica, especialmente a medida que sus equipos integran más la OT, la IoT y los activos en la nube en sus flujos de trabajo.
Junto a este crecimiento, la industria está repleta de herramientas de gestión de vulnerabilidades dispares, cada una diseñada para abordar solo una parte específica de toda su superficie de ataque. Pocas funcionan como una solución de seguridad completa, todo en uno. Debido a esto, usted se queda con datos dispares, visibilidad incompleta y puntos ciegos que los atacantes esperan descubrir antes que usted.
Los agentes maliciosos buscarán sus deficiencias de seguridad y las usarán para moverse lateralmente a lo largo de su red, con frecuencia sin ser detectados.
Lea este libro electrónico para obtener más información sobre cómo unificar la seguridad a lo largo de su superficie de ataque, incluyendo los siguientes puntos:
- Lecciones aprendidas de vulneraciones anteriores.
- Obstáculos comunes en la gestión de exposición.
- Cinco formas de optimizar sus estrategias de priorización de vulnerabilidades para evitar vulneraciones.
Comunidad de Tenable Connect: su mejor recurso para la gestión de exposición
Únase a Tenable Connect para conectarse con otras personas que tengan intereses similares de aprender más sobre la gestión de exposición o cómo madurar los programas existentes de gestión de vulnerabilidades basada en el riesgo a una estrategia de gestión de exposición más efectiva.
Le damos la bienvenida a la guía de implementación de Tenable One
Tenable One es una plataforma de gestión de exposición que ayuda a las organizaciones a obtener visibilidad a lo largo de la superficie de ataque moderna, enfocar los esfuerzos para prevenir posibles ataques y comunicar con precisión el riesgo de exposición a fin de lograr un rendimiento óptimo del negocio.
Leer másConsejos rápidos para una respuesta eficaz a la exposición
En el vertiginoso escenario digital actual, es esencial gestionar las vulnerabilidades, pero no solo alcanza con identificar las deficiencias. Para que la gestión de vulnerabilidades sea eficaz, se deben priorizar y abordar los riesgos de forma que se impulsen mejoras de la seguridad y se eviten exposiciones importantes.
Leer másSeguridad en la nube híbrida con Tenable One
Tenable Cloud Security no es solo seguridad en la nube. Forma parte del amplio ecosistema de gestión de exposición de Tenable, y eso puede marcar una gran diferencia. Dado que los riesgos no están aislados en silos y los adversarios no atacan por categoría, es fundamental poder usar soluciones de un proveedor para diferentes tipos de infraestructura (local, en la nube, OT, etc.) a fin de detectar posibles rutas de ataque.
Ver ahoraPreguntas frecuentes sobre la gestión de exposición
¿Recién comienza con la gestión de la exposición de amenazas? ¿Tiene preguntas, pero no sabe por dónde empezar? Vea estas preguntas frecuentes sobre la gestión de exposición cibernética.
¿Qué es la gestión de exposición?
¿Qué hace la gestión de exposición?
¿Cómo puede la gestión de exposición hacer madurar mi programa de ciberseguridad?
¿Por qué necesito la gestión de exposición?
¿Cuáles son las funciones clave de un programa de gestión de exposición?
¿Cómo puedo empezar con la gestión de exposición?
- Conozca la seguridad de todos sus activos e identifique las brechas.
- Observe toda su superficie de ataque desde la perspectiva de un atacante.
- Priorice la corrección en función del riesgo real para la organización (no de puntuaciones CVSS arbitrarias).
- Mida sus procesos de corrección con la mejora constante.
- Comunique eficazmente el riesgo y tome medidas para reforzar su superficie de ataque.
¿Qué ventajas ofrece la gestión de exposición?
- Visibilidad completa hacia su superficie de ataque.
- Pase de la seguridad reactiva a poder anticiparse a las consecuencias de un ataque cibernético.
- Datos de seguridad contextualizados para priorizar la corrección.
- Una comunicación más eficaz a lo largo de toda la organización, hasta los altos ejecutivos y la junta directiva.
¿Qué pasos puedo dar para anticiparme a los riesgos cibernéticos?
¿Cómo ayuda la gestión de exposición a tomar mejores decisiones de negocios?
¿Cómo puedo reducir la exposición cibernética de manera proactiva?
¿Qué debería tener en cuenta de una plataforma de gestión de exposición?
- Facilite la visualización de todos sus activos, en todas partes y en una sola plataforma.
- Le ayude a darles sentido a los datos de seguridad y proporciona inteligencia de amenazas, con soporte de la IA y el aprendizaje automático, para que pueda anticiparse a las amenazas y priorizar la corrección.
- Le ayude a comunicar eficazmente el riesgo cibernético para poder tomar mejores decisiones de negocios y seguridad.
¿Qué puedo aprender de la gestión de exposición?
- ¿Qué tan seguros estamos?
- ¿Qué debemos priorizar?
- ¿Cómo reducimos la exposición con el tiempo?
- ¿Qué resultado obtenemos si nos comparamos con nuestros competidores?
¿Puede la gestión de exposición interrumpir las rutas de ataque?
¿Por qué el inventario de activos es importante para la gestión de exposición?
¿Cómo desarrollar un programa de gestión de exposición?
Si bien adoptar un abordaje basado en el riesgo puede ayudar a sus organizaciones a madurar el programa de gestión de vulnerabilidades, la verdadera pregunta hoy en día es si esto es suficiente.
La respuesta es que probablemente no lo sea.
En cambio, un programa de gestión de exposición puede ayudarle a lograr que su programa de ciberseguridad pase de ser reactivo y estar atascado en la respuesta ante incidentes a ser proactivo y ofrecer a su equipo información completa de toda su superficie de ataque. Esto le ayudará a mantenerse al tanto del escenario de las amenazas en constante cambio y su significado para la necesidades únicas de su organización.
Ponga en práctica estas cinco recomendaciones para comprender mejor todas sus exposiciones y poder reducir de manera proactiva el riesgo cibernético:
-
Evalúe sus activos actuales, locales y en la nube (TI, OT, IoT, aplicaciones web, etc.).
Pregunte lo siguiente: ¿Funcionan conjuntamente nuestras tecnologías y nos ofrecen información completa de todos nuestras exposiciones? ¿O siguen estando aisladas en silos?
-
Comprenda la visibilidad de su superficie de ataque.
Pregunte lo siguiente: ¿Qué podemos ver? ¿Qué necesitamos ver?
-
Priorice sus esfuerzos.
Pregunte lo siguiente: ¿Qué debemos hacer primero? ¿Cómo pueden nuestras estrategias de corrección ser más predictivas? ¿Estamos usando la inteligencia de amenazas? ¿Podemos analizar todas las rutas de ataque de nuestros activos más críticos?
-
Mida sus procesos de corrección.
Pregunte lo siguiente: ¿Hasta qué punto estamos reparando las exposiciones que descubrimos ahora? ¿Qué podemos hacer para mejorar la eficacia? ¿Cómo son nuestros esfuerzos en comparación con los de nuestros colegas del sector?
-
Comunique y tome medidas.
Pregunte lo siguiente: "¿qué tan seguros estamos?". ¿Podemos comunicar eficazmente nuestra postura de seguridad a ejecutivos, partes interesadas clave y demás personas? ¿Cómo usamos los datos para tomar decisiones de negocios más eficaces?
¿Qué plataforma de gestión de exposición es la adecuada para su organización?
Encontrar una solución de ciberseguridad fiable y eficaz lleva mucho tiempo y provoca frustración. Y, a menudo, incluso después de evaluar e implementar meticulosamente una solución, conseguir que todo el mundo la use y aproveche todas sus ventajas puede ser aún más difícil.
Esto se debe a que estas soluciones han sido tradicionalmente difíciles de usar o proporcionan tantos datos que sus equipos no saben qué hacer con ellos.
Seleccionar una solución de gestión de exposición y lograr que su equipo la incorpore no tiene por qué ser un dolor de cabeza. Aquí le presentamos tres características clave que debe buscar para simplificar el proceso:
-
La solución facilita la visualización de todos sus activos, en todas partes y en una sola plataforma.
Sí, tanto a nivel local como en la nube. La solución debe ser algo más que una forma de hacer un inventario de sus activos. Una solución eficaz de gestión de exposición también debe identificar las vulnerabilidades relacionadas con los activos, los errores de configuración y otros problemas de seguridad, y permitir un monitoreo continuo para que siempre sepa lo que tiene y dónde pueden surgir exposiciones.
Busque una solución que le ofrezca una vista unificada de toda su superficie de ataque moderna para poder eliminar los puntos ciegos y saber qué debe hacer para gestionar eficazmente el riesgo cibernético.
-
La solución le ayuda a comprender los datos, anticiparse a las amenazas y priorizar la corrección.
Busque un sistema de gestión de exposición que le ayude a usar la inteligencia de amenazas y otros datos pertinentes para anticiparse a las consecuencias de un ataque cibernético, ya que este afecta directamente a su organización.
Busque una solución en la que se identifiquen las relaciones a lo largo de su superficie de ataque entre activos, exposiciones, privilegios y amenazas, y que pueda ayudarle a priorizar la gestión y corrección de riesgos. Su solución también debe poder identificar continuamente las rutas de ataque que plantean el mayor riesgo de explotación, incluso a medida que su superficie de ataque cambia y se expande rápidamente. Estas funciones facilitarán a sus equipos la reducción proactiva del riesgo con el mínimo esfuerzo para prevenir ataques.
-
La solución debería ayudarle a comunicar eficazmente el riesgo cibernético para que pueda tomar decisiones de negocios y seguridad más fundamentadas.
Busque una solución de gestión de exposición con una visión centralizada y alineada con la empresa de sus exposiciones, junto con KPI claros para medir el progreso a lo largo del tiempo.
La solución también debe ofrecer información que vaya más allá de una visión general y le permita profundizar en detalles concretos a nivel de activo, departamento o unidad operativa. Además, busque una solución con funciones de evaluación comparativa para que pueda conocer el rendimiento de su programa en relación con el de sus colegas del sector.
Ventajas de la gestión de exposición.
La gestión de exposición consiste en alejarse de la seguridad reactiva y encaminarse hacia una estrategia más proactiva que disminuya sus exposiciones. Al adoptar una plataforma de gestión de exposición, su organización estará mejor preparada para anticiparse a posibles ataques y, al mismo tiempo, reducir el riesgo de manera proactiva.
Estas son algunas ventajas de la estrategia de gestión de exposición:
Obtenga una visibilidad completa
Con una vista unificada de su superficie de ataque, puede identificar rápidamente todos sus activos, en todas partes, detectar los problemas de seguridad relacionados, y reducir el tiempo y el esfuerzo que necesita para disminuir el riesgo.
Anticipe las consecuencias de un ataque cibernético
Una plataforma de gestión de exposición puede ayudarle a comprender mejor las relaciones entre sus activos, exposiciones, privilegios y amenazas a lo largo de toda su superficie de ataque, tanto a nivel local como en la nube.
Priorice acciones
Al identificar sus vulnerabilidades explotables, rutas de ataque y de vulneración, y centrarse continuamente en ellas, puede mejorar sus capacidades de priorización de riesgos para obtener mejor información de la corrección, de modo que pueda reducir las amenazas cibernéticas y prevenir ataques con mayor eficacia.
Comunique con mayor eficacia
Un programa de gestión de exposición le proporciona una visión de sus exposiciones alineada con el negocio para que pueda comunicarse más eficazmente con las principales partes interesadas de un modo que coincida con las metas y los objetivos de su negocios.
Vea a Tenable One en acción
Tenable One combina la gestión de vulnerabilidades basada en el riesgo, el escaneo de aplicaciones web, la seguridad en la nube y la seguridad de identidades en una única plataforma de gestión de exposición. Le ofrece una vista unificada de toda su superficie de ataque para que pueda abordar y gestionar de manera proactiva el riesgo de todos sus activos.
Bytes del blog de gestión de exposición
Gestión de exposición: reducción del riesgo en la superficie de ataque moderna
Muchos equipos de seguridad están estancados siendo reactivos y eso suele deberse a que sus programas están aislados en silos y tienen tantas herramientas que generan tantos datos que no saben qué hacer con ellos o en qué enfocarse primero.
En este blog, se explora cómo la gestión de exposición puede darle la visibilidad que necesita para anticiparse más eficazmente a las amenazas, priorizar la corrección y reducir el riesgo. Siga leyendo para saber cómo puede usar una plataforma de gestión de exposición para unificar los datos de cada una de sus herramientas de evaluación y controles, de modo que pueda ver claramente dónde tiene dependencias. El resultado es la capacidad de comprender más eficazmente la verdadera naturaleza de dónde puede estar expuesto a un ataque y su impacto potencial.

Gestión de exposición: siete ventajas de un abordaje de plataforma
Tradicionalmente, la mayoría de los profesionales de la seguridad han usado diversas herramientas dispares, cada una diseñada específicamente para un solo aspecto de la superficie de ataque. Por ejemplo, una herramienta para la TI y otra para la OT. Una herramienta para la nube. Pero ¿es este el abordaje más eficaz? Estas herramientas suelen aislar los datos en plataformas propias, lo que hace imposible obtener una visión completa de todos los activos y vulnerabilidades a lo largo de su amplio entorno.
En este blog, se analiza la pregunta: ¿qué es más eficaz? ¿Esas herramientas o una solución consolidada? Mediante el análisis minucioso de las ventajas y desventajas de cada una de ellas, conozca siete razones por las que debería considerar una plataforma completa de gestión de exposición para sustituir a estas soluciones puntuales.

De qué manera la gestión de exposición puede hacer que las pruebas de penetración sean más eficaces
¿Cómo puede aprovechar más las pruebas de penetración y aumentar su eficacia? En este blog, se examina más detenidamente cómo una estrategia de gestión de exposición puede mejorar sus pruebas de penetración para fortalecer su postura de ciberseguridad. Por ejemplo, con una plataforma de gestión de exposición, puede realizar escaneos rutinarios de vulnerabilidades, en lugar de esperar a los resultados de las pruebas de penetración.
Lea este blog para obtener más información sobre las ventajas de la gestión de exposición y cómo puede detectar todos sus activos y vulnerabilidades relacionadas, y enfocar sus pruebas de penetración en la identificación de puntos ciegos para poder reforzar sus defensas antes de que los agentes maliciosos se aprovechen de sus exposiciones.

¿Cómo proteger sus activos de TI, OT e IoT con una plataforma de gestión de exposición?
Las brechas de visibilidad son habituales a lo largo de entornos convergentes de TI/OT. Esto se debe a que las herramientas de seguridad de TI tradicionales pueden omitir las vulnerabilidades de OT, mientras que las herramientas de seguridad de los activos de OT pueden no tener en cuenta los activos de TI dependientes.
En este blog, se exploran las ramificaciones de las brechas de visibilidad en su entorno de OT, como en el caso de las identidades, que aumentan su riesgo de negocios y cibernético. Esto lo expone a un mayor riesgo de posibles tiempos de inactividad e interrupciones, que podrían provocar pérdidas de ingresos, condiciones de trabajo inseguras o, en el peor de los casos, incluso la pérdida de vidas humanas. Lea este blog para obtener más información sobre el valor integral de usar una plataforma de gestión de exposición en su superficie de ataque de TI/OT convergente.

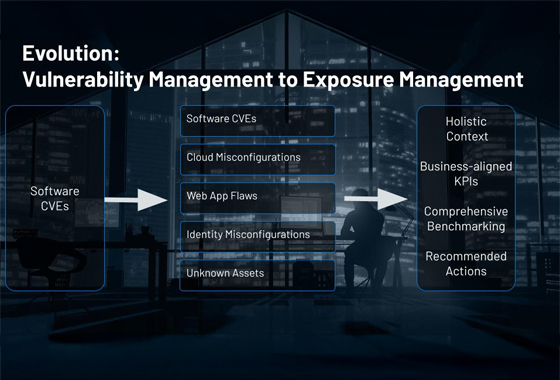
El contexto es fundamental: desde la gestión de vulnerabilidades hasta la gestión de exposición
Un programa de gestión de vulnerabilidades es clave para las estrategias proactivas de ciberseguridad; sin embargo, la mayoría de las organizaciones se encuentra sepultada bajo una gran cantidad de datos sobre vulnerabilidades que tienen poco contexto sobre el riesgo real para el negocio. Sin este contexto, no podrá priorizar eficazmente las exposiciones de alto riesgo a lo largo de su superficie de ataque.
En este blog, se explora el valor más amplio de una estrategia de gestión de exposición para superar retos comunes como la sobrecarga de vulnerabilidades y la lentitud de la respuesta de corrección. Lea este blog para obtener más información sobre cómo pasar de la mentalidad de gestión de vulnerabilidades a la de gestión de exposición, incluyendo cómo comprender el contexto de los activos, la función de las identidades y el contexto de las amenazas.

Correlacione y cierre las rutas de ataque viables antes de que comiencen las vulneraciones
Las rutas de ataque híbridas pueden cruzar fácilmente los dominios de seguridad. Si usa soluciones de seguridad puntuales, es posible que esté pasando por alto estas rutas de ataque. Los agentes maliciosos esperan que así sea. Están ansiosos por aprovecharse de sus descuidos para poder moverse lateralmente sin ser detectados a través de sus redes.
En este blog, se examinan en mayor detalle las lecciones aprendidas de los atacantes del mundo real y cómo las herramientas puntuales limitan la visibilidad que necesita para exponer y cerrar las brechas de seguridad a lo largo de su superficie de ataque. Lea este blog para obtener más información sobre ataques recientes de gran repercusión y sobre cómo una estrategia de gestión de exposición puede ayudar a sus equipos de seguridad a lograr mejores resultados en materia de seguridad.
Gestión de exposición bajo demanda
El punto de vista de un adversario de su superficie de ataque
Al pensar como un atacante, sus equipos de seguridad estarán mejor preparados para proteger de manera proactiva su superficie de ataque.
En este seminario web bajo demanda, se explora por qué la detección completa de la superficie de ataque es un desafío para la mayoría de los equipos de seguridad. Véalo ahora para obtener más información sobre los siguientes temas:
- Cómo se ve su empresa desde la perspectiva de un atacante.
- Lecciones aprendidas de tres ataques cibernéticos, incluyendo tácticas y vectores de ataque.
- Cómo puede mejorar sus estrategias de priorización y corrección con una mayor colaboración entre equipos.
De qué manera los desafíos de las personas, los procesos y la tecnología perjudican a su equipo de ciberseguridad
Las normas de seguridad de la industria y los gobiernos son cada vez mayores y más complejas, lo cual dificulta que los profesionales de la ciberseguridad vayan al paso de la evolución de los requisitos de cumplimiento.
En este seminario web bajo demanda, se exploran las maneras en que sus equipos de seguridad pueden optimizar las prácticas de gestión de exposición. Véalo ahora para obtener más información sobre los siguientes temas:
- Principales silos operativos y tecnológicos que obstaculizan la seguridad proactiva.
- Pasos que dan las organizaciones maduras para mejorar sus estrategias y cultura de seguridad preventiva.
- Recomendaciones que puede aplicar rápidamente, independientemente de la madurez actual de su programa.
El escenario de las amenazas de ciberseguridad: ¿dónde se encuentra ahora?
La superficie de ataque moderna evoluciona constantemente, lo que dificulta la reducción de complejidades para proteger a su empresa de posibles filtraciones cibernéticas.
En este seminario web bajo demanda, se analizan las maneras en las que puede anticiparse a los atacantes a partir de la comprensión de su postura de seguridad actual. Vea este seminario web para obtener más información sobre los siguientes temas:
- Desafíos de la visibilidad de la superficie de ataque.
- Cómo proteger su organización de las amenazas cibernéticas.
- Ventajas de la gestión de exposición.
- Cómo evitar dificultades al atravesar la evolución de las estrategias de seguridad.
Cuando se habla de vulnerabilidades, "critical" (críticas) no siempre implica precisamente eso.
Cuantos más activos tenga a lo largo de su superficie de ataque, mayor será la posibilidad de que pase por alto vulnerabilidades. Si no conoce todos los activos que tiene y sus vulnerabilidades asociadas, disminuye rápidamente la eficacia de sus procesos de gestión de parches.
En este seminario web bajo demanda, se analiza cómo reducir la fricción entre sus equipos de InfoSec y de TI para mejorar su postura de ciberseguridad. Vea este seminario web para obtener más información sobre los siguientes temas:
- Qué hace que una vulnerabilidad crítica sea realmente crítica.
- De qué manera los sistemas habituales de puntuación de vulnerabilidades pueden impedir la colocación eficaz de parches.
- Por qué debe cerrar la brecha de comunicación entre sus equipos de seguridad, TI y cumplimiento normativo.
- Cómo optimizar la colocación de parches para mejorar la corrección.
Identifique y aborde el riesgo cibernético de manera proactiva
Muchos equipos de ciberseguridad tienen dificultades para prevenir ataques cibernéticos. Esto se debe a que suelen abrumarse con datos de vulnerabilidades sin contexto y no tienen la visión que necesitan de su superficie de ataque.
Esto significa que frecuentemente no saben qué es lo primero que requiere su atención o cómo reparar los problemas de seguridad que pueden tener el mayor impacto en su organización.
Los equipos de seguridad modernos más eficaces tendrán que evolucionar de un abordaje de gestión de vulnerabilidades reactivo a una estrategia de gestión de exposición proactiva. Esto empieza por acabar con los silos que impiden que los equipos de seguridad obtengan la información completa sobre la superficie de ataque que necesitan para anticiparse a los ataques cibernéticos.
Conozca su superficie de ataque
La ciberseguridad eficaz y proactiva depende de la visibilidad de la superficie de ataque. Una plataforma de gestión de exposición puede ofrecerle una vista unificada de todos sus activos a lo largo de toda su superficie de ataque, para que pueda identificar las vulnerabilidades relacionadas, los errores de configuración y otros problemas de seguridad. Esta información es importante para comprender dónde tiene exposiciones para que pueda priorizar y planificar qué hacer al respecto.
Comprenda su exposición
Es fundamental que conozca su exposición para poder tomar decisiones factibles sobre cómo abordarla. La gestión de exposición puede ayudar a medir su postura de seguridad actual y evaluar el rendimiento de sus equipos a la hora de descubrir fallos críticos y qué tan rápido pueden corregir los problemas que reducen la mayor cantidad de riesgo para su organización. Al cuantificar su exposición, debería poder responder a preguntas como: "¿Hasta qué punto estamos seguros?" y "¿Dónde nos encontramos con respecto a nuestros esfuerzos de prevención y mitigación?".
Visualice las rutas de ataque
Una puntuación basada en el riesgo con criticidad de activos y gravedad de amenazas reduce el ruido de fondo en un factor de 23:1 y prioriza la corrección con base en el riesgo de exposición real para su negocio.
Compare riesgos
La gestión de exposición le ofrece una visión de negocios del riesgo cibernético. Por ejemplo, puede desarrollar KPI que midan el rendimiento interno de su programa a lo largo del tiempo, así como hacer una evaluación comparativa de la madurez del programa con la de sus colegas del sector. Esto le permitirá alinear su programa de seguridad y los objetivos de negocios de su organización, y mejorar la comunicación con sus ejecutivos y principales partes interesadas.
Vea a Tenable One en acción
Obtenga visibilidad completa hacia su superficie de ataque moderna. Enfoque sus esfuerzos en prevenir ataques potenciales. Tome decisiones de negocios y seguridad impulsadas por los datos.
- Tenable One








