Gestión de postura de seguridad de datos (DSPM)
Proteja los datos confidenciales de la nube con una CNAPP unificada
Proteja sus datos en la nube contra accesos no autorizados y otras exposiciones con la gestión de postura de seguridad de datos (DSPM) integrada en una plataforma unificada de protección de aplicaciones nativas en la nube (CNAPP). Al integrar DSPM en su estrategia unificada de seguridad en la nube, obtiene contexto de datos procesable que prioriza mejor los riesgos y reduce la exposición de su organización a las filtraciones de datos de los clientes y la puesta en riesgo de los recursos de IA y la propiedad intelectual.
Solicitar una demostración Tomar un tour auto-guiadoIdentifique y proteja los datos confidenciales en la nube
Conozca dónde residen sus datos y si son confidenciales
Encuentre datos en entornos multinube y clasifíquelos.
Exponga el riesgo con precisión personalizada
Priorice las exposiciones de datos que generan rutas de ataque y ponen en riesgo a su negocio.
Cierre el riesgo para los datos en la nube con corrección contextualizada
Emprenda acciones con respecto al riesgo para los datos con correcciones guiadas y automatizadas.
Priorice y aborde los riesgos
de los datos en entornos multinube
Tenable Cloud Security, con capacidades DSPM integradas, monitorea continuamente su entorno multinube para detectar y clasificar tipos de datos, asignar niveles de confidencialidad y priorizar los hallazgos de datos en el contexto de toda la superficie de ataque en la nube.
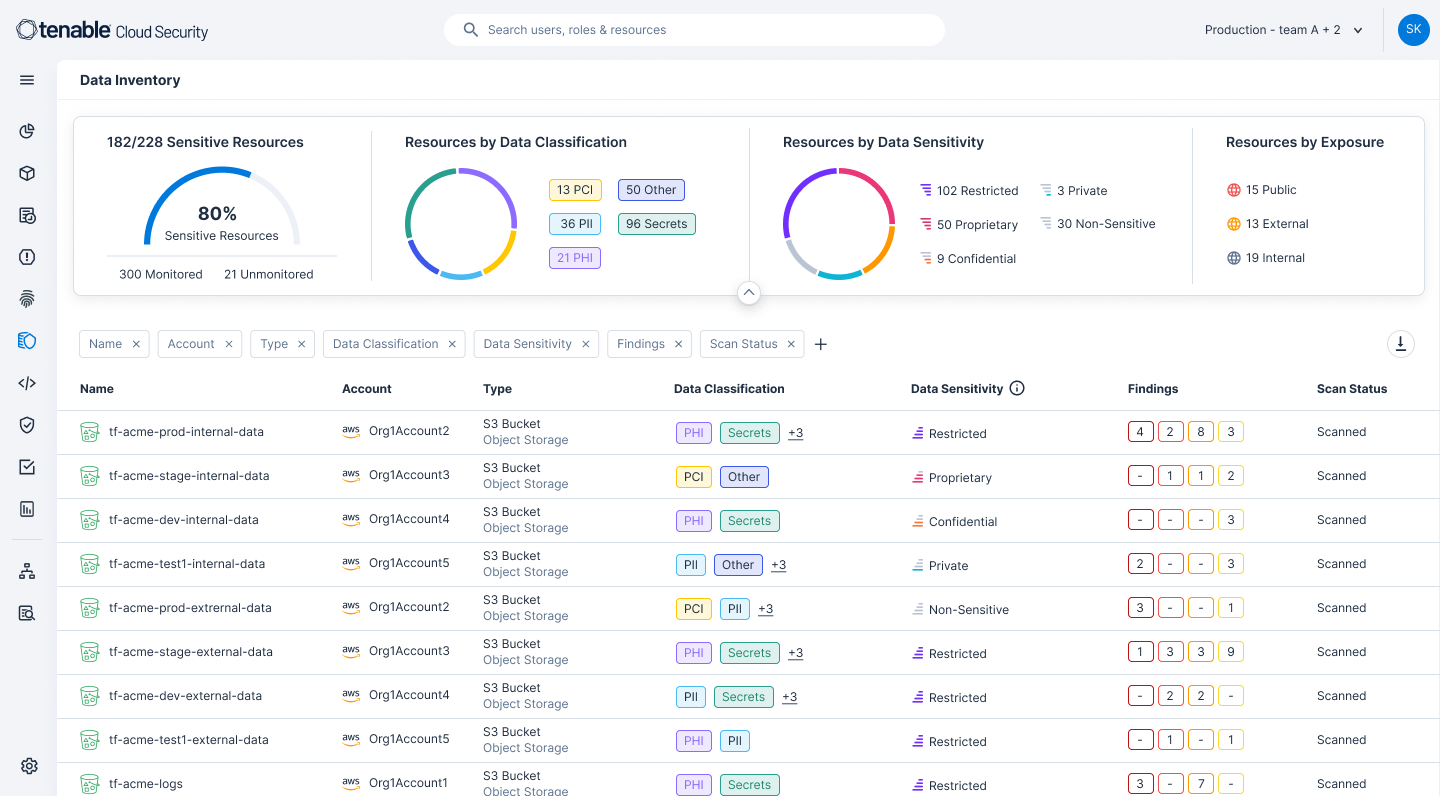
Detecte y clasifique datos confidenciales
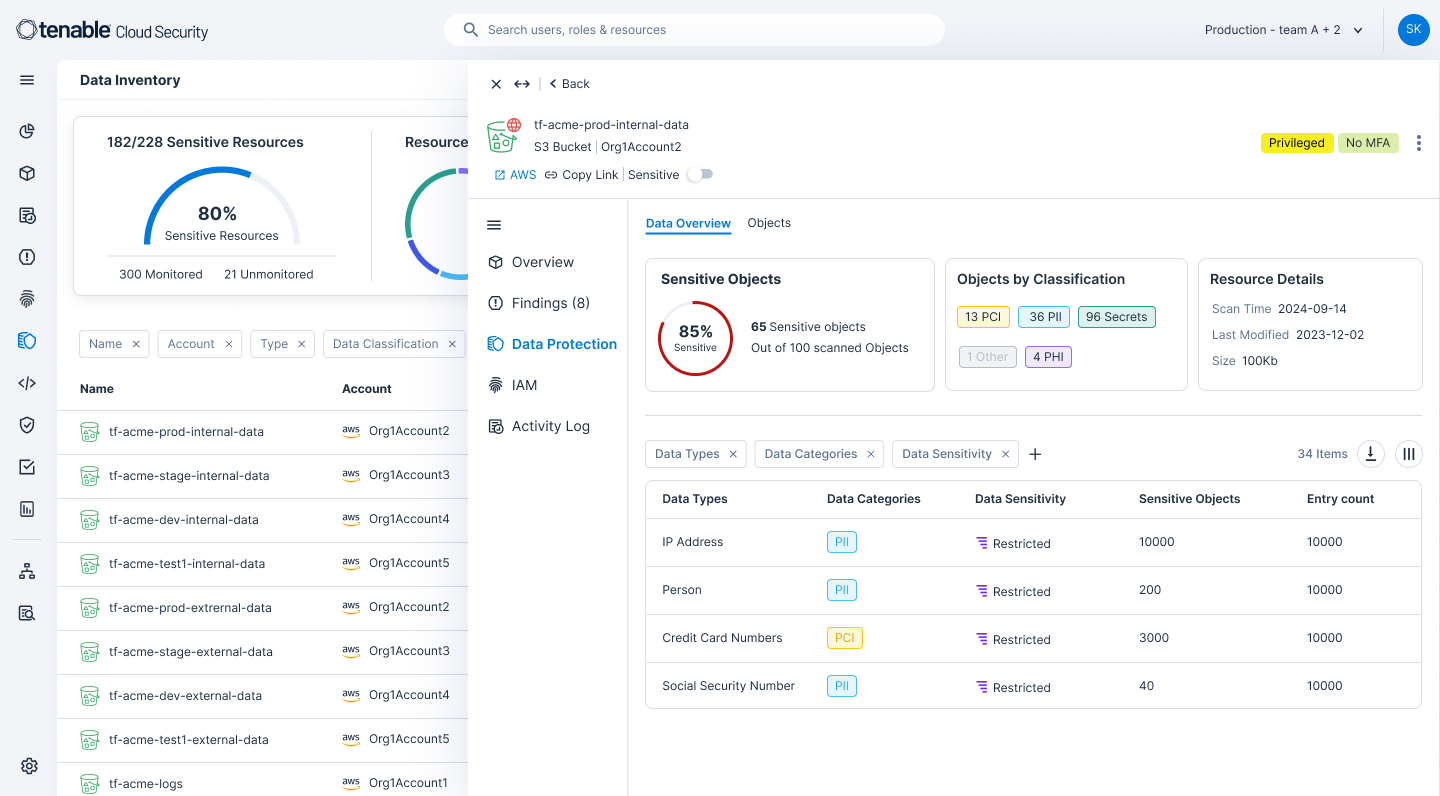
Obtenga visibilidad completa de dónde residen los datos en su entorno en la nube. Desde servicios y cargas de trabajo de IA hasta buckets de S3, Tenable Cloud Security identifica los recursos de datos mediante escaneos de API sin agentes, clasifica los hallazgos de datos por niveles de gravedad y, a continuación, agrupa los datos en categorías como secretos de empresa o PHI. Este abordaje de tres capas comprende el contexto de la cuenta y reduce el ruido de las alertas para que usted pueda priorizar las exposiciones que importan más para el cumplimiento general y la postura de seguridad de su organización.
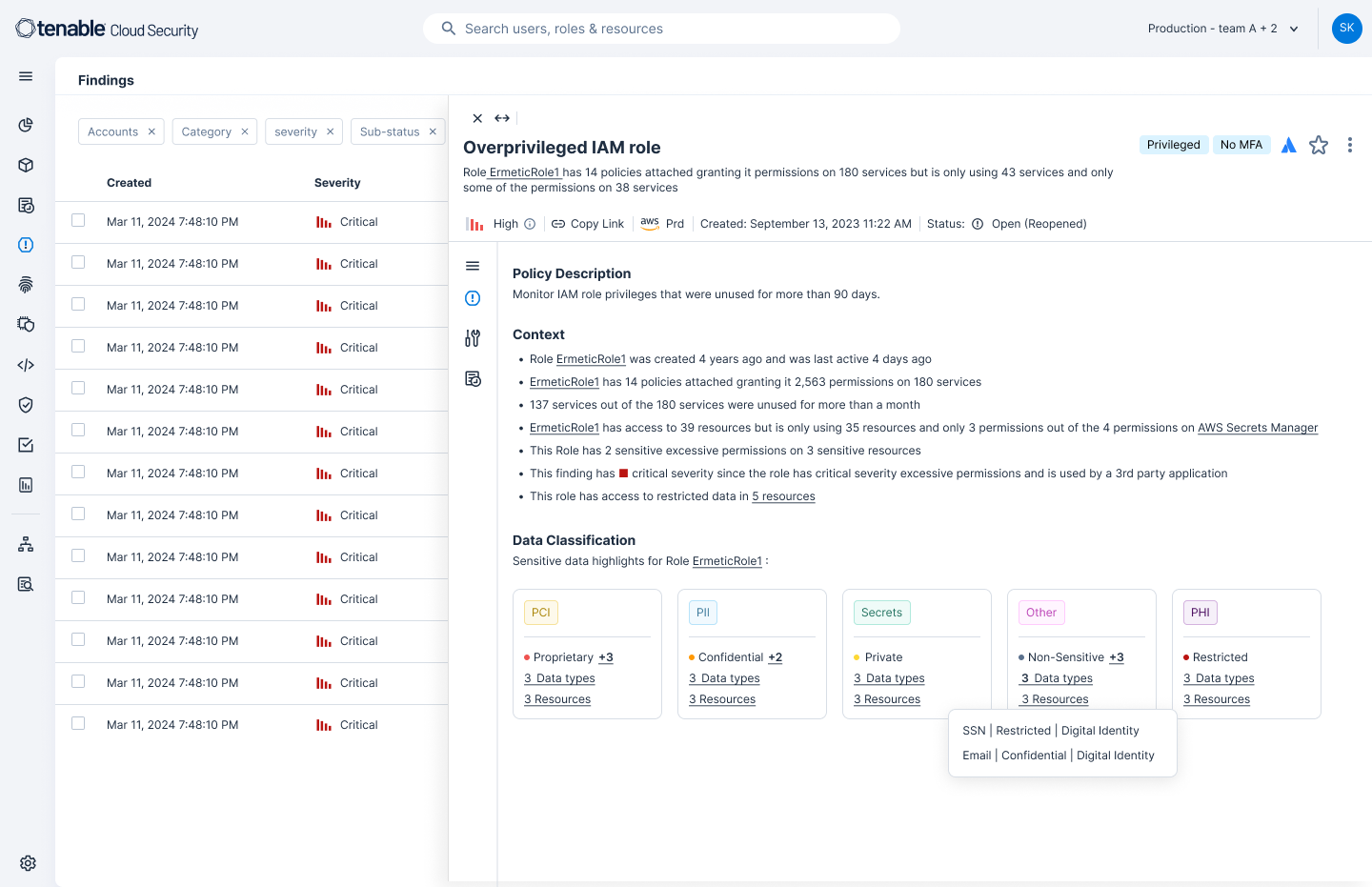
Haga cumplir el acceso de privilegios mínimos a los datos
Detecte actividad sospechosa relacionada con los datos antes de que se convierta en una vulneración e investigue anomalías con información detallada sobre identidades y el accesos. Tenable Cloud Security enriquece los hallazgos de identidad con el contexto de clasificación de datos para que pueda ver dónde una identidad humana o de máquina puede acceder a recursos de datos confidenciales y revocar permisos según sea necesario. Vea el contexto de seguridad de datos en el tablero de control de gestión de identidades y accesos (IAM) para realizar un análisis profundo del acceso a datos confidenciales y emprender medidas para bloquear las rutas de ataque que un atacante podría explotar.
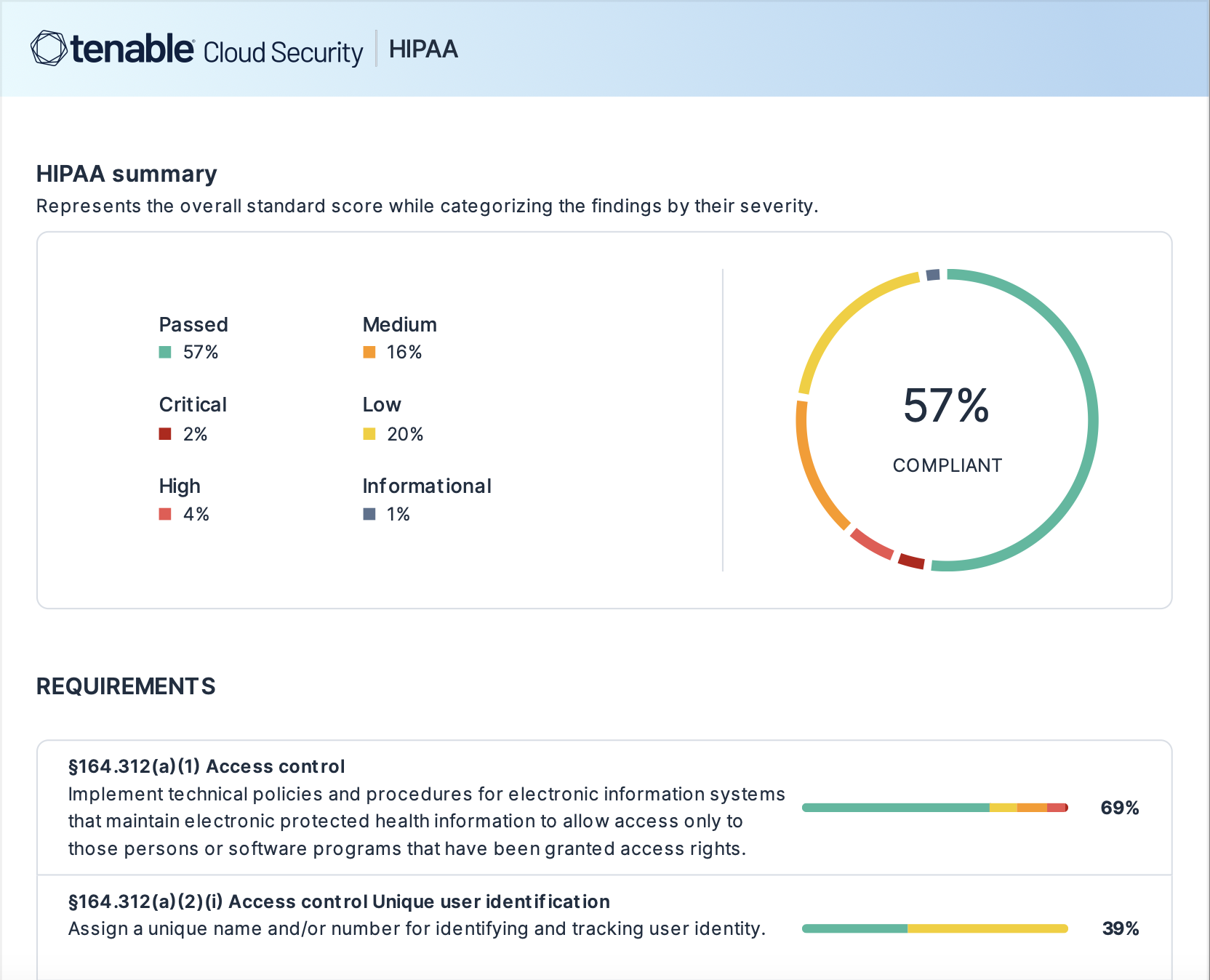
Priorice la corrección con base en sus objetivos de seguridad y cumplimiento
Aproveche las políticas integradas y personalizables para evaluar configuraciones de datos y obtener alertas sobre exposiciones críticas específicas para su negocio. Personalice los hallazgos de seguridad con etiquetas de datos personalizadas o impórtelos desde sus entornos en la nube. Emprenda acción sobre estos riesgos priorizados con correcciones paso a paso y contexto a profundidad que proporciona detalles de lo que hay atrás de configuraciones o privilegios riesgosos. Genere informes con un solo clic para comunicar los requisitos de cumplimiento específicos de la industria para PII, PHI y PCI.
Obtenga más información sobre Tenable Cloud Security
El uso de la automatización [de Tenable Cloud Security] nos permitió eliminar procesos manuales exhaustivos y realizar en minutos lo que le habría llevado a dos o tres profesionales de seguridad meses.
- Tenable Cloud Security