Mastering the Art of Kubernetes Security

With Kubernetes’ explosive adoption by the development community comes an urgent need to secure clusters and ensure their compliance effectively.
Kubernetes (K8s), having won the popularity contest, is having its heyday as today’s standard for running modern, containerized applications in the cloud. As their K8s usage grows, dev and devops practitioners are seeking to adopt Kubernetes security practices. The environment and technology are yet evolving, leaving organizations to figure out much of the security piece on their own. Said one security leader, “I need to know the ‘why’ so I can think through how to do this [security] in a different environment.”
If you’re using Kubernetes as a managed service you may think shared responsibility has you covered — or that enlisting your cloud provider’s Kubernetes security tools will meet the need. Or you may think your existing investments in cloud security posture management (CSPM) and cloud workload protection (CWP) extend security and compliance to your Kubernetes deployments. Alas, your Kubernetes environment is highly dynamic and complex, a skyborne data center – securing it requires dedicated tools that know it well.
Kubernetes environments are under attack for a triad of reasons: their rapid growth in use, existing tools falling short and everyone trying to figure Kubernetes security out. Cloud-native solutions exist that are designed to safeguard against the threats and vulnerabilities unique to Kubernetes environments and ensure K8s workload compliance. This blog post looks into considerations and best practices for securing your provider-managed Kubernetes environment.
What is required to secure my Kubernetes environment?
First, let’s clarify what a Kubernetes environment is and does. At a high level, think of a Kubernetes environment as a cloud within a cloud, managing a dynamic and expanding estate of containerized workloads.
What is a Kubernetes environment?
A Kubernetes environment is a platform for orchestrating workloads (applications) across interconnected computers or servers. It contains the tools and resources needed to deploy, manage and scale these applications. Its value is in facilitating cloud operations through easy distribution and management of applications and by ensuring they work together seamlessly across machines and adapt to changes.
A Kubernetes environment contains multiple components:
- Control plane - made up of several components including the API server and scheduler
- Nodes - the “compute brain” of a Kubernetes cluster
- Pods - the smallest Kubenetes unit, containing one or more (a cluster of) containers scheduled to run together
- Networking - communication between pods and services
- Persistent storage - preservation of data even if a pod or container is restarted
- Service discovery and load balancing - reliable access to pods and distribution of incoming network traffic across pods, respectively
- Configurations and secrets management - handling of configuration data and securing of sensitive information
- Monitoring and logging integration - resource use visibility, anomaly detection, audit
All these components create a self-sufficient, highly complex and dynamic ephemeral world that is nevertheless vulnerable to being targeted and penetrated.
What is involved in securing a Kubernetes environment?
While it provides powerful capabilities for deploying and managing containerized workloads at scale, Kubernetes technology creates complex security challenges you may not have encountered in other cloud environments. These challenges affect every one of the Kubernetes environment components described above and include cluster configuration and vulnerability management, network security, role-based access control (RBAC), secrets management and runtime security.
Therefore securing an K8s environment requires scanning, monitoring and analyzing its components so you can:
- See across and into all K8s clusters
- Detect any K8s workload misconfigurations
- Detect any container image vulnerabilities
- Analyze RBAC well enough to be able to see excessive or risky permissions and misuse
- Prioritize critical risks for optimal productivity
- Monitor and audit K8s related compliance including CIS and other standards
- Remediate
Can – or should – you achieve this level of Kubernetes security with your own two hands? What tools do you already have that can help?
Are CSPM, CWP or cloud-provider Kubernetes security tools enough?
It’s natural to hope the tools in your arsenal are sufficient for Kubernetes security. Cloud CSPM and CWP are useful and essential cloud protection capabilities that many organizations deploy first. Unfortunately, individually or when used together, these solutions provide only baseline Kubernetes security.
CSPM and Kubernetes security
CSPM solutions offer visibility, and misconfiguration and compliance management for cloud deployments, at the cloud service level. They monitor configuration data across cloud applications, identifying and fixing misconfigurations that could lead to threats, risks, vulnerabilities and account hygiene violations, and mapping findings to benchmarks and standards. Lately some CSPM tools have started adding — or reporting to add — Kubernetes security capabilities. However the K8s architecture and layered approach to workloads is different from that of other cloud services, limiting a CSPM solution’s ability to see inside and secure Kubernetes clusters. CSPM solutions can provide high level insights for Kubernetes environments but should be used together with Kubernetes-specific security tools and practices.
CWP and Kubernetes security
CWPs scan cloud containers, so can see the containers that run within Kubernetes, but essentially cannot see the Kubernetes components managing those containers. For example, a CWP solution will scan cloud containers but in most cases not see inside a K8s cluster and its orchestration components, and the workloads running within. This inability to detect misconfigurations and other potential risks in Kubernetes clusters creates a security gap. Like in the case of CSPM, it has been recommended that enterprises add Kubernetes-specific security capabilities on top of their CWP solution to ensure holistic protection of their cloud environment.
Cloud-provider Kubernetes security tools
While GCP, AWS, Azure and other cloud providers offer Kubernetes managed services, remember that the Kubernetes platform is open source — no one cloud provider has mastery over it. So what about cloud provider security tools for Kubernetes? Tread with caution.
Every cloud provider offering Kubernetes capabilities (in other words, all cloud providers) provides native tools for securing the Kubernetes clusters you build on their platform. These tools vary in maturity level and primarily support just that provider’s cloud. Still, cloud provider K8s security tools have benefits:
- Seamless management. Cloud provider Kubernetes security features typically integrate seamlessly with the cloud platform, so using their security tools can streamline your experience if you are using other security tools by the same provider
- More shared responsibility on their end. Cloud providers typically handle the underlying infrastructure and security controls, so using their K8s security tools may reduce work managing and maintaining security configurations
- Ongoing updates. Cloud providers continually enhance their Kubernetes offerings with new security features and updates, so using their native tools may give you fast use of the new capabilities, possibly at no extra cost
On the downside, cloud provider K8s security tools fall short on fullstack risk analysis of clusters, third-party integrations and customization – and for the most part aren’t multi-cloud. So their ability to detect, prioritize and remediate security weaknesses deep within containers and their orchestration is limited.

A CIS Kubernetes benchmark exists for each major cloud provider, helping clarify but raising the bar on deploying Kubernetes environments securely
3 Kubernetes security best practices
Like a good marriage, securing your Kubernetes environment needs to be an ongoing effort aimed at incremental improvement. Overall, the effort involves securing your configurable cluster components and the applications that run in the cluster. To do so, your routine Kubernetes security chores — right up there with listening skills, date night and remembering anniversaries — will involve continuous monitoring, controlling roles and access with RBAC, securing network configuration and regular logging and audits.
We focus here on a few best practices we consider the path to a successful strategy and mindset, and mastering the art of K8s security:
#1 Go deep. Make sure your K8s security tools are querying the heck out of your K8s environment: cloud provider APIs (including, for example, clusters and node pools), the Kubernetes API for each cluster (if allowed), the virtual machines (VM) and, importantly, context added from other resources (for example a container images repository or network analysis). This information will yield deep visibility into your Kubernetes RBAC and network configuration. Also, be sure to put identity protection front and center. Leading analysts speak to the importance of applying identity-centric security to containers, VMs, apps and “services running as users” to reduce the risk of unmanaged machine identities. Effective RBAC and identity management are essential for controlling access to Kubernetes resources. Adopting the principle of least privilege minimizes the attack surface and reduces the risk of unauthorized access. Establish well-defined roles, implement strong authentication mechanisms and enforce strong password policies. Review and revoke unnecessary privileges to ensure the integrity and confidentiality of your Kubernetes clusters. Applying the principle of least privilege to your RBAC identities and the Kubernetes container application itself is a foundational step in your zero trust journey. Remember that in traditional environments RBAC was also no picnic -- you had no guarantee that an assigned role and access were being applied as intended or wasn’t compromised. Let applying security best practice to RBAC in your K8s clusters be a corrective experience in which you know exactly the resources that identities can and should have access to.
#2 Prioritize. Context. Context. Context. A siloed view into Kubernetes security will take you down a noisy rabbit hole of false positives – and there’s only so much time in a day. Open the aperture - let in the full context of cloud configuration, permissions and workload vulnerabilities to produce an accurate assessment and prioritization of what needs to be fixed first – not just screaming risks or vulnerabilities but those that are both screaming and evaluated as having greatest potential impact in the context of other risks. Existing KSPM tools often provide simple analysis, which results in more false positives and noise for developers, not to mention complex risks, such as toxic scenarios, that go undetected.
#3 Remediate. I’m cheating here, because remediation and prioritization are essentially the same entity: remediation being the “yang” of the risk-prioritization “yin.” Spotting and prioritizing the problem is a bit of a “Hans and Gretel drop the breadcrumbs as you go” scenario – in identifying the problem you have also outlined the path to its mitigation. Still, remediation as a best practice deserves its own spotlight not only for the importance of fixing errors but because doing so involves engagement and a kind of teaming from security to development. The same security leader mentioned above who is trying to figure out Kubernetes security also stressed the criticality of a communication process with development and DevOps. Effective and efficient remediation requires spelling out corrective actions in meaningful instructions for the folks doing the rebuild and redeploy -- depending on your organization, that can be the development, devops or other teams. This is an excellent place to mention infrastructure as code (IaC) security, which is a cathartic way to remediate because you’re not just fixing a problem in production or staging, you’re going back to source and preventing the misstep from happening anew. (Yes, KSPM and IaC security can and should be bedfellows - we’ll dedicate a future blog to the topic.) For now, suffice it to say that being able to apply findings to code, especially in a highly abstracted Kubernetes environment that encourages an “as code” mindset for every element (e.g. compliance as code, policy as code), makes a strong case for a holistic cloud security platform that includes IaC scanning.
# Bonus best practice: Processes and people. Since security takes a village remember to extend your K8s security planning to include your processes and people:
- Processes. You’ll want to perform regular security audits and compliance checks to maintain the integrity and regulatory adherence of Kubernetes deployments. Conducting comprehensive audits of Kubernetes configurations, cluster policies, and access controls helps identify potential weaknesses and areas for improvement. As part of ensuring compliance with industry regulations like GDPR or HIPAA make a point of regularly reviewing and updating security policies and procedures.
- People. Educating and training developers, devops and other stakeholders toward a culture of security awareness is an essential part of securing a modern cloud environment. Get everyone on board with the relevant knowledge, skills and buy-in to address evolving security threats.
How a KSPM solution works
The devil is in the details. While CSPM and CWP scan at the cloud configuration or workload level, KSPM digs in and scans and analyzes at the Kubernetes cluster level. Kubernetes is an open-source platform for managing and orchestrating containerized applications, and addresses the unique security of Kubernetes environments.
KSPM solutions connect with the Kubernetes clusters managed by a cloud provider and monitor the clusters’ configuration data. Specifically, KSPM solutions query the Kubernetes API for each cluster, and use agentless and/or agent based scanning and analysis of node configurations and containers.
Typically, KSPM capabilities are packaged with other security solutions – a trend that supports common goals to consolidate security tools. Ideally, they will be part of a holistic cloud security platform that couples Kubernetes findings with intelligence from CWP, IaC scans, CSPM and CIEM capabilities. The benefit is two-way, correlating risk factors for more effective identification and prioritization of Kubernetes risk and factoring Kubernetes environment insights into the cloud environment’s overall security.
Advanced KSPM solutions equip organizations with:
- Full resources inventory and visibility. Provide a detailed inventory of Kubernetes resources within clusters and across multi-cloud environments
- Configuration assessment. Detect misconfigurations and vulnerabilities, and access detailed remediation instructions
- Vulnerability management. Prioritize workload vulnerabilities in the context of overall risk including cloud configuration, identity, permissions and network exposure
- Enforce least privilege at the role level. Enforce least privilege for users and services using the internal Kubernetes rRBAC mechanism. (On securing IAM mechanisms in Kubernetes, you may want to read about cloud provider capabilities for federating cloud identities for secure access to resources. Federating identities is actually a straightforward process and improves security management of access permissions for K8s clusters.)
- Compliance mapping to K8s policies. Continually assess Kubernetes clusters against standards and benchmarks including CIS Kubernetes (AWS, Azure and GCP) and NSA.
- Threat detection. Apply continuous behavioral analysis to quickly identify anomalies, and investigate and speed up incident response to cloud threats
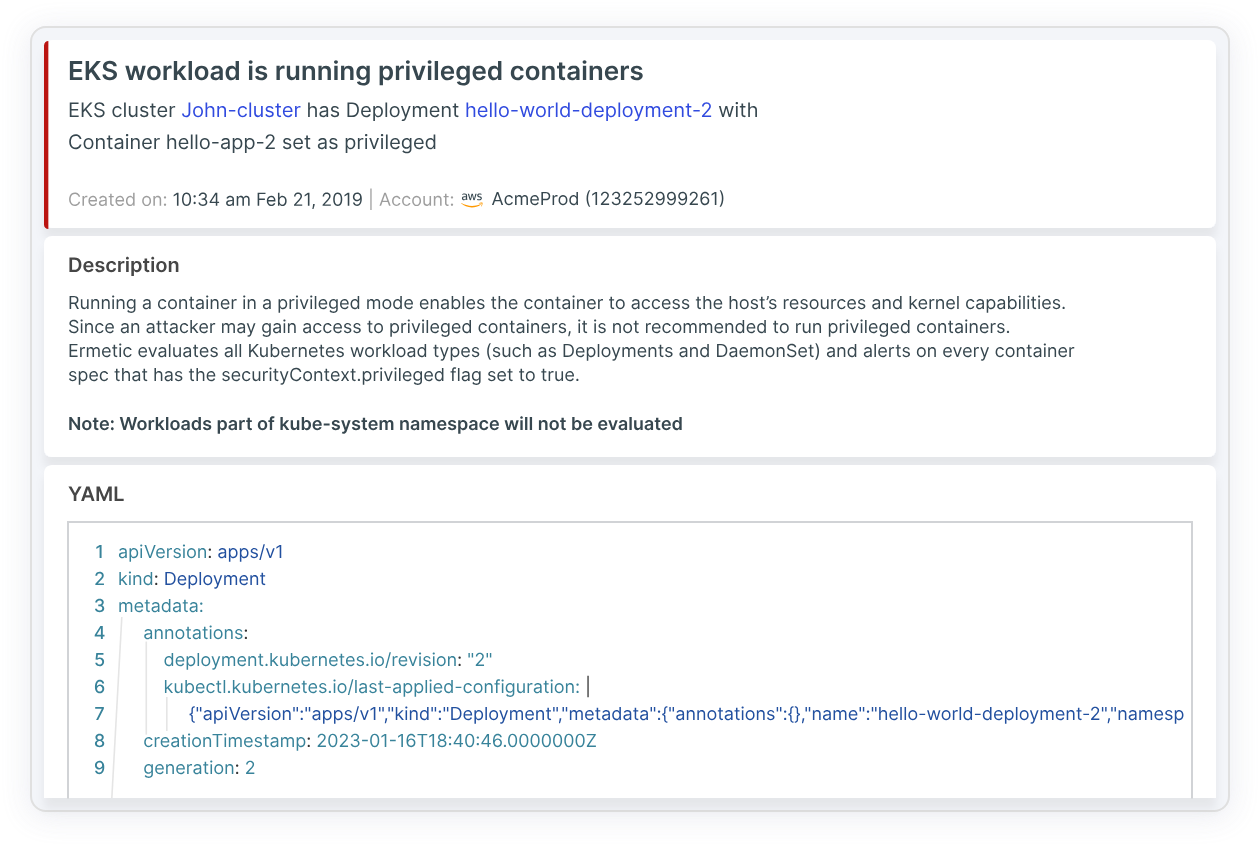
A KSPM solution performs fullstack risk analysis on all Kubernetes workloads and alerts to vulnerabilities
Importantly, securing Kubernetes environments requires communication with the development or devops team because they are the ones to build the re-deploy. KSPM solutions integrate with engineering workflows for seamless sharing of alerts, findings and mitigation recommendations with the relevant parties. KSPM solutions also often offer customization options and fine grained control over security policies and configurations, for adapting security measures to align with your organization’s specific requirements and compliance standards.
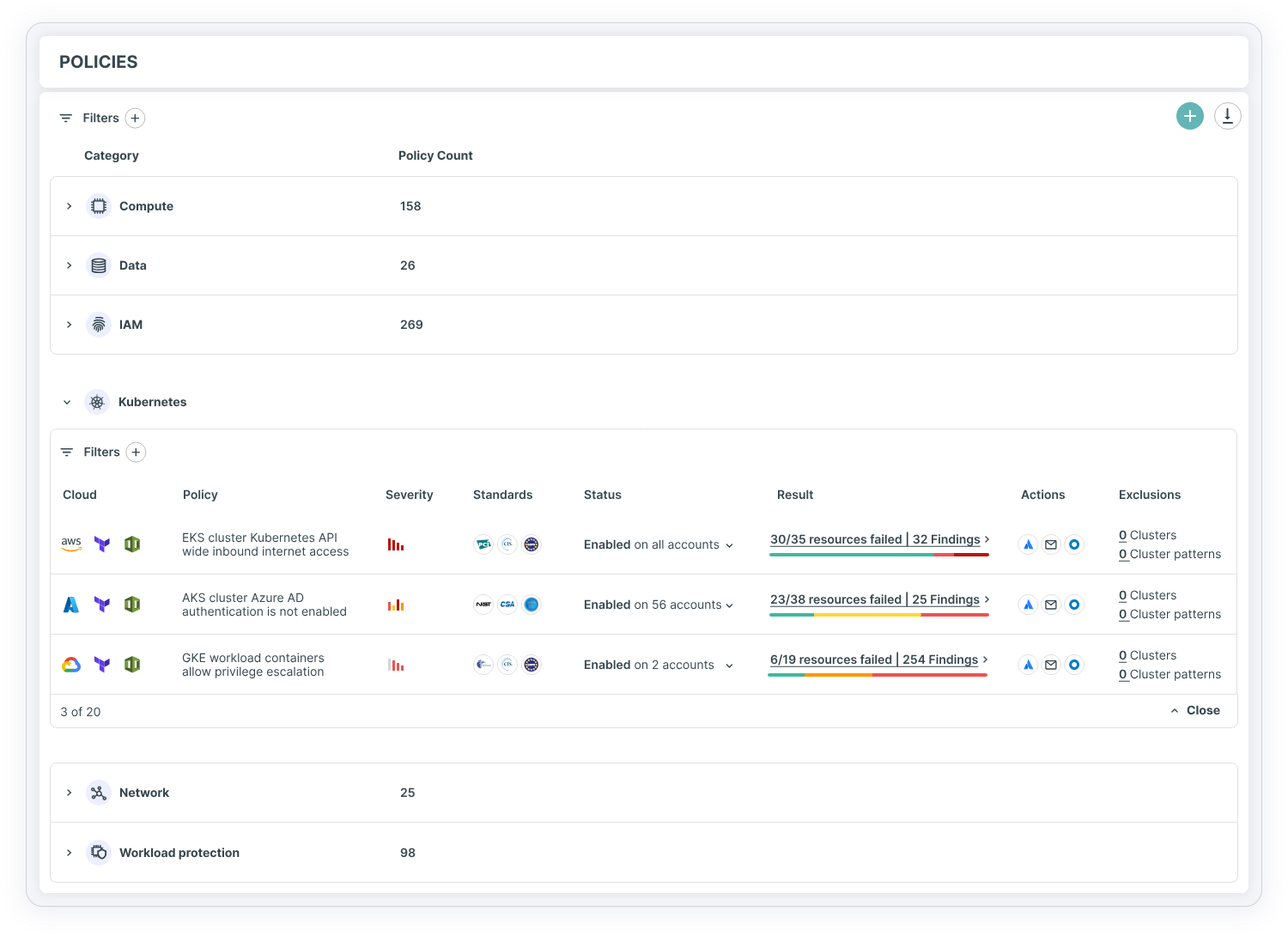
A KSPM solution assesses Kubernetes-specific policies for attack vectors including API exposure, privilege escalation and privileged access across multicloud platforms
How a KSPM solution can benefit you
In the cloud, change is a constant. We’ve learned that risk hidden in cloud complexity can only realistically be tackled by deep insight into cloud infrastructure, policies and components, across layers and providers. K8s environments require that same respect regarding risk. Working with a KSPM brings light and control:
- Complete visibility into a detailed inventory of all resources inside your Kubernetes clusters
- Continuous posture assessment that detects misconfigurations in cloud and K8s resources
- Automatic prioritization in the full context of cloud configuration, permissions, and workload vulnerabilities, and remediation accelerated by guided how-tos and workflow integrations
- Contextualized container image scanning that helps prioritize which vulnerabilities to fix first
- K8s internal RBAC control including access risk remediation and least privilege
- Compliance with standards and benchmarks including CIS for Kubernetes
Just as CIEM closes IAM security gaps, and CSPM closes configuration management gaps and CWP closes workload security gaps, organizations need focused solutions for Kubernetes security for granularity and capabilities that close their K8s environment security gaps.
Takeaway: Effective Kubernetes security for containerized environments
Implementing robust Kubernetes security practices is essential for organizations seeking to secure their containerized environments effectively. You’ll want to ensure you are carrying out continuous monitoring, RBAC, secure network configuration, logging, regular audits and ongoing education. The best practices to zoom in on are using an automated solution that is at the same time laser-focused on Kubernetes and its unique security issues, and also part of a greater, holistic cloud native application platform that pulls in the fullstack cloud context needed to go deep to identify, prioritize and remediate risk. By embracing KSPM within a CNAPP as part of your overall cloud security strategy you can master the art of building a continuously secure foundation for your container-based applications across multi-cloud, ensure their compliance and promote efficiency in mitigating K8s cluster vulnerabilities and flaws – including in infrastructure as code. Learn what CNAPP is.
- Cloud


