Level Up Your Cloud Security Strategy

Learn how to better your cloud security program with these ten security resolutions.
It’s no secret that the cloud – and anything related to it –has a communication problem. From CSPs to CSPMs to EC2s, there’s a litany of acronyms and jargon to contend with, especially in the realm of cloud security. Each acronym and concept represents an important part of the cloud security ecosystem. However, it’s often a headache to decipher, remember, and then stay up to date as terms naturally evolve to meet the changing needs of complex cloud infrastructure.
Jargon, acronyms, solutions, oh my!
There’s numerous reasons why acronyms dominate cloud vernacular. Like in any industry, cloud jargon and specific terms evolve based on need. However, I believe the underlying cause is that the cloud is challenging and that simple fact informs how we talk about it.
Even amidst the jargon, actionable and concise security best practices are out there. In this blog, we hope to offer ten humorous, but actionable security resolutions that put acronyms in context and that you can implement with Tenable Cloud Security. These resolutions are designed to help you level up your security strategy without making you crack open a cloud security encyclopedia.
Ten resolutions to level up your cloud security strategy with Tenable Cloud Security
Resolution #1: Commit to a better cloud
As with most things, the hardest part of cloud security is getting started. Many organizations struggle to figure out basic cloud needs, such as how to allocate resources and upskill security teams. According to the 2022 Osterman State of the Cloud Survey commissioned by Ermetic (now part of Tenable), 80% of companies reported they lack a dedicated security team responsible for protecting cloud resources. Staffing security roles for the cloud is just the first n a series of important steps companies must take to secure their clouds.
There are a variety of resources for security teams to jumpstart their cloud education and gain new skills. The Certificate of Cloud Security Knowledge (CCSK) from the Cloud Security Alliance, and the Certified Cloud Security Professional (CCSP) from ISC2 are two tried and tested options. Additionally, cloud service providers (CSPs) like Amazon Web Services’ (AWS) Solution Architect certification, also provide comprehensive training. There are many certifications and learning plans to choose from, but ensuring your teams understand hybrid and multi-cloud fundamentals is essential to a secure and compliant infrastructure.
Resolution #2: Be less vulnerable
Seemingly small vulnerabilities can open the door to costly attacks. In 2023, the global average data breach cost was $4.45 million, according to the IBM Cost of a Data Breach Report 2023. Ouch! Cloud workload protection (CWP) capabilities can help secure your multi-cloud environment and prevent breaches. CWP does this by providing prioritization and consistent governance across running cloud resources, so you can find the common security risks that make your organization vulnerable.
At Tenable, workload protection is central to our cloud security solution. To support customer needs in unique cloud environments, Tenable offers both an agentless and agent-based solution. Tenable Cloud Security provides agentless workload protection that scales access to multi-cloud environments and correlates vulnerabilities across OS packages, applications and libraries. It also provides insight into toxic combinations – security risks that when combined and left unremediated create a viable attack path for bad actors to leverage.
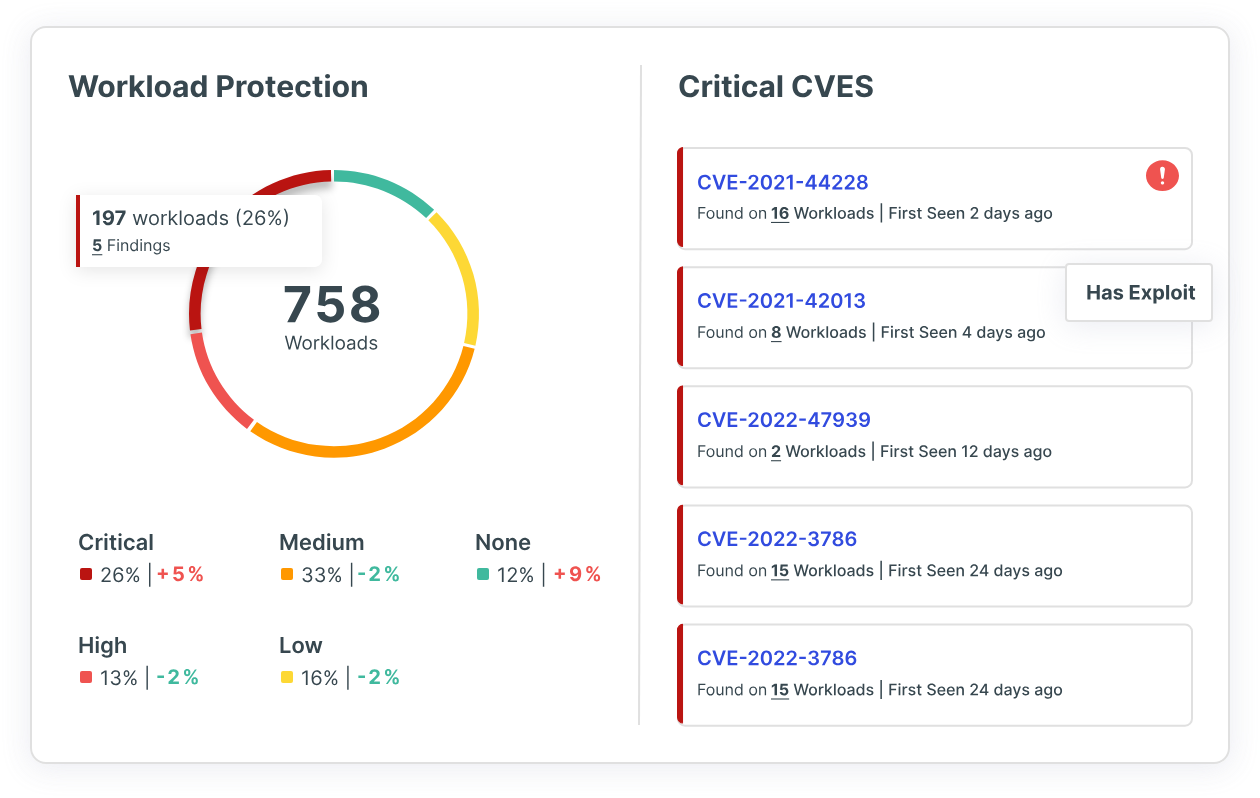
Resolution #3: Manage audit anxiety
If just reading the word ‘audit’ makes your stomach turn to knots, you’re not alone. Organizations on average spend 15 hours per month creating security reports for business leaders, according to the study “Old Habits Die Hard: How People Process and Technology Challenges Are Hurting Cybersecurity Teams,” based on a commissioned survey of 825 cybersecurity and IT leaders conducted in 2023 by Forrester Consulting on behalf of Tenable. That number doesn’t include the time and effort spent ensuring compliance across all teams and remediating out-of-compliance deployments or investigating incidents.
To manage audits with confidence you need visibility into what’s running, and what’s being accessed across all clouds and how that posture maps to industry compliance standards. With a frequently updated ‘security state of the union’ you can start to automate remediation and prioritize action based on risk-level and compliance adherence.
Cloud security posture management (CSPM) capabilities, such as the ones included as part of Tenable Cloud Security, automatically report on the state of compliance and provide automated remediation. CSPM also gives teams detailed one-click industry standard reports that illustrate adherence to external stakeholders. These intuitive dashboards allow users to gain and maintain cloud compliance without having to break a sweat. Imagine getting all those hours of reporting back while gaining a more accurate picture of your security posture!
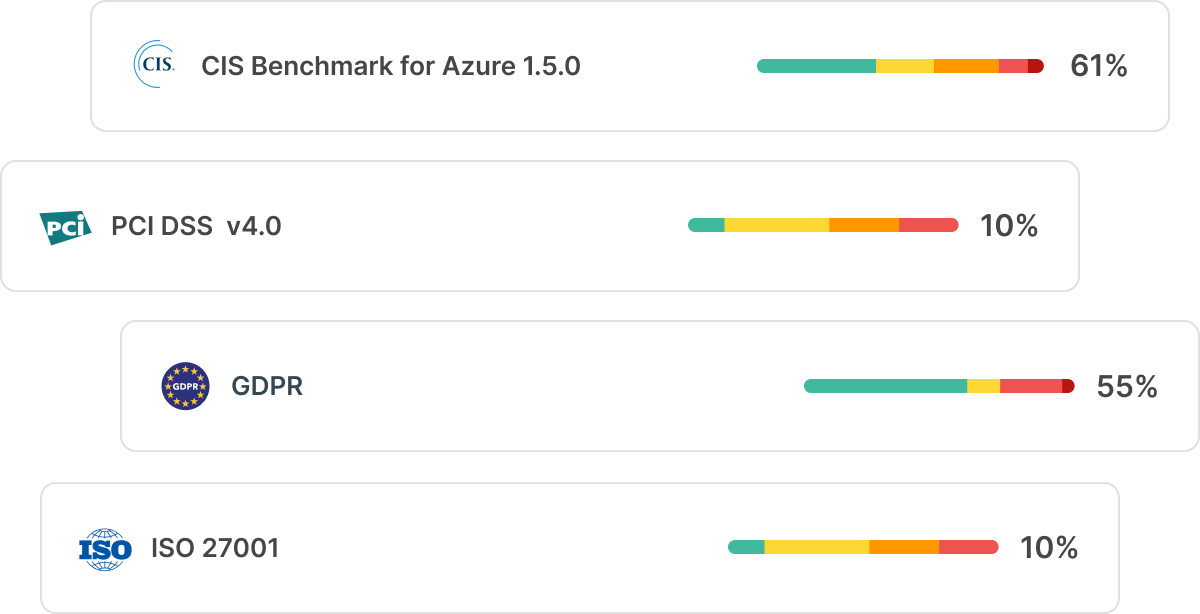
Resolution #4: Take a CIEMple approach to cloud access
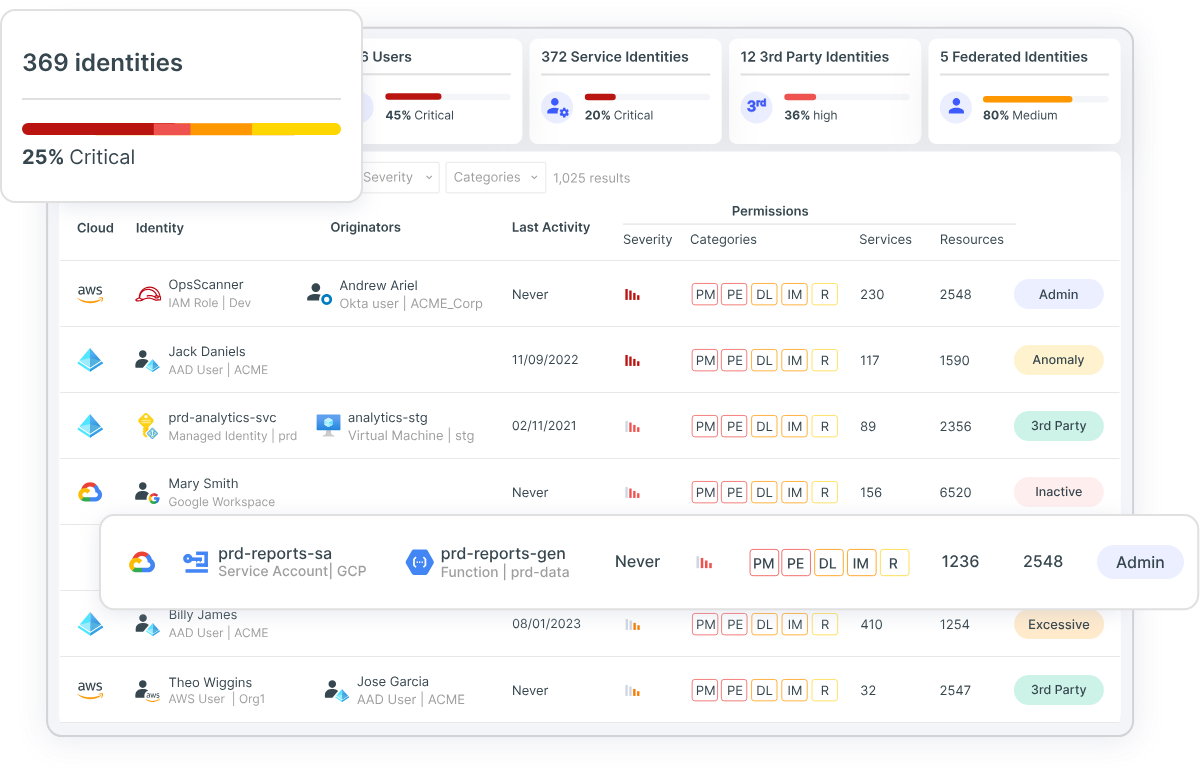
An effective cloud infrastructure and entitlement management (CIEM) tool helps make identity security simple or “CIEMple”. However, without CIEM, permissions and entitlements often turn into a convoluted and intertwined mess. Trying to isolate anomalous behavior related to a specific resource or identity can be like finding a needle in a haystack. 52% of organizations lack full visibility into the resources an identity can access and into the permission level granted, according to the Osterman Research State of the Cloud 2022 report. A full inventory and visualization of all cloud identities, entitlements, configuration and resources is needed to achieve least privilege at scale.
In addition to visualization of identities and access, organizations must be able to answer two simple questions:
- Who has access to what cloud resources?
- What can they do with that access?
Tenable Cloud Security allows you to confidently answer those questions using world-class CIEM capabilities. By providing a behavior baseline and full-stack visibility, Tenable Cloud Security offers step-by-step, automated remediation to fix the identity risks that matter most, including excessive permissions, network exposure and suspicious behavior.
Resolution #5: Be everywhere with policy as code
Security staff shouldn’t have to clone themselves to secure their environments from build to deployment and into runtime. Policy as code (PaC) takes the policies that are most important to your organization and makes them scalable and automatically enforced across the application development lifecycle. Defining security policies at a high-level and codifying them into PaC ensures that policies are consistent in high-velocity cloud environments. PaC is becoming increasingly more important as research suggests that security teams are being squeezed. According to a report by ISC2, 67% of the cybersecurity professionals surveyed reported a shortage of cybersecurity staff.
PaC helps organizations maintain a proactive approach to security and compliance throughout the development lifecycle. Tools like Terrascan, Tenable’s open source, static-code analyzer, and Tenable Cloud Security can help organizations implement PaC across the development lifecycle in a tailored way. With Tenable Cloud Security you can create custom policies or utilize out-of-the-box policies aligning to categories such as compute, secrets, Kubernetes, logging, workload protection and more.
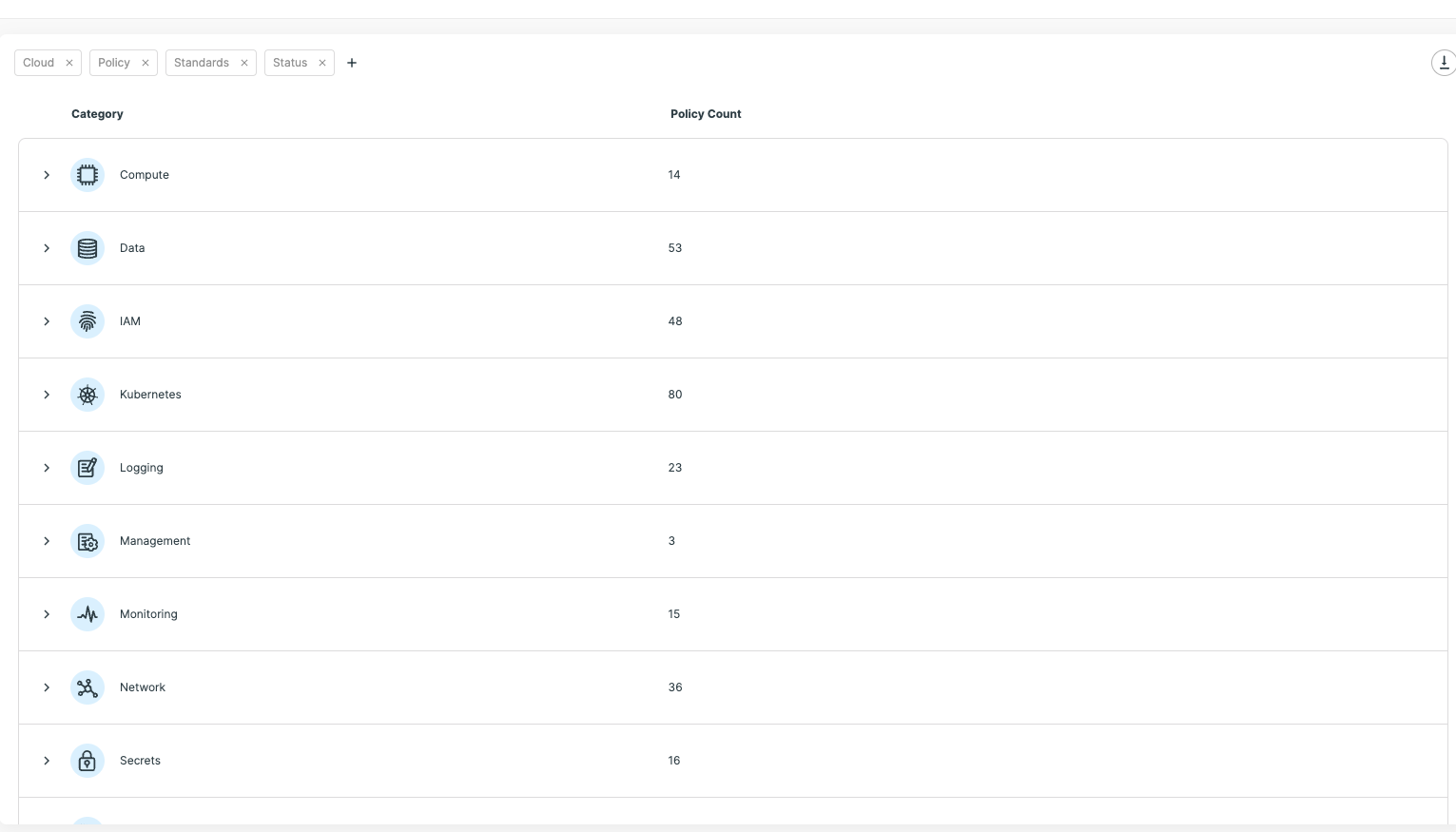
Resolution #6: Lower your MTTR
Mean time to remediation (MTTR) is probably the most talked about security metric. While speed to remediate is important, recent data suggests that it’s only half the battle. Ananalysis of about 1,000 companies found just 13% of vulnerabilities observed were remediated, according to the Mend Open Source Risk Report.
These staggering numbers prove the value of automated remediation and prioritized risk. If only a small percentage of vulnerabilities are being remediated, then you should ensure that remediation is done to the vulnerabilities that pose the greatest risk to your environment. Using PaC to define security policies that can be leveraged for automated remediation frees up security teams to focus on remediating more complex vulnerabilities.
Tenable Cloud Security mitigates risk using auto-generated and customizable policies that integrate across ticketing, continuous integration and continuous deployment (CI/CD) pipelines, IaC and other workflows. Tenable Cloud Security lowers MTTR and reduces work for security and DevOps teams alike by:
- expediting remediation through full-stack analysis
- tracking vulnerabilities until resolution
- providing targeted and easy to understand remediation advice to users
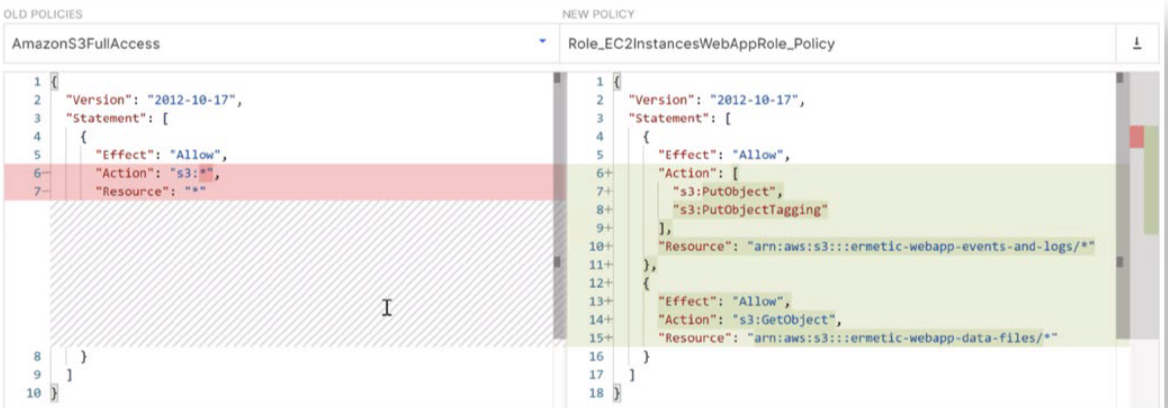
For example, if a developer spins up an over-privileged AWS EC2 instance, Tenable Cloud Security can automatically produce a right-sized policy that developers can easily implement into their CI/CD pipelines.
Resolution #7: Love thy developers
Rome wasn’t built in a day and neither are secure cloud environments. Behind every cloud deployment is an army of developers. Cloud deployments are also ground-zero for security governance. According to the Osterman Research State of Cloud 2022 Survey, almost 40% of organizations have more than 500 developers or DevOps engineers, which results in more privileged users and more potential for misconfigurations and vulnerabilities. For security teams to work preventatively, they need to implement governance into developer workflows while providing a positive user experience for developers.
For example, each developer needs a baseline set of permissions to do their job. However, new and ad-hoc tasks can arise that may necessitate elevated access to a variety of cloud resources or services. Enforcing the principle of least privilege without an integrated workflow for temporary elevated access is not ‘loving thy developer’ — it’s slowing them down with manual, paper-pushing processes. A self-service, just-in-time access portal that integrates with existing ChatOps tools like email, Slack and Jira relieves this pain and creates a better user experience while enforcing the principle of least privilege. The Tenable Cloud Security Just-in-Time Access Portal makes it easy for developers to request access for a specific amount of time or pull request, and automatically revokes their permissions when they’re no longer needed.
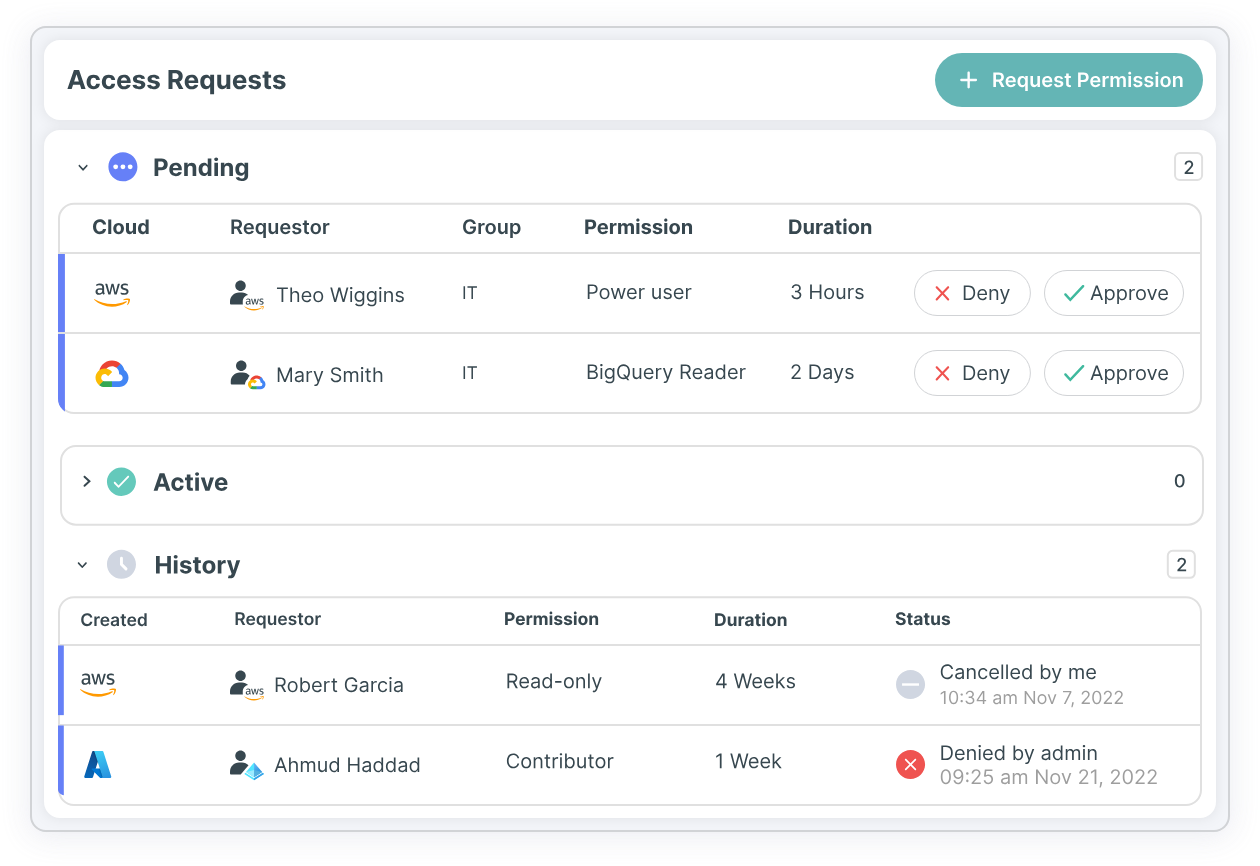
Resolution #8: Say no to default configurations
Kubernetes clusters can often feel like a black hole to security teams. Without the right tools, there’s no efficient way to assess risk and remediate vulnerabilities within Kubernetes clusters. This lack of visibility results in security incidents. According to the Red Hat State of Kubernetes Report 37% of organizations polled experienced revenue or customer loss due to a container/Kubernetes security incident. Due to the volume of components, their ephemeral nature and default configurations, Kubernetes can become a security challenge.
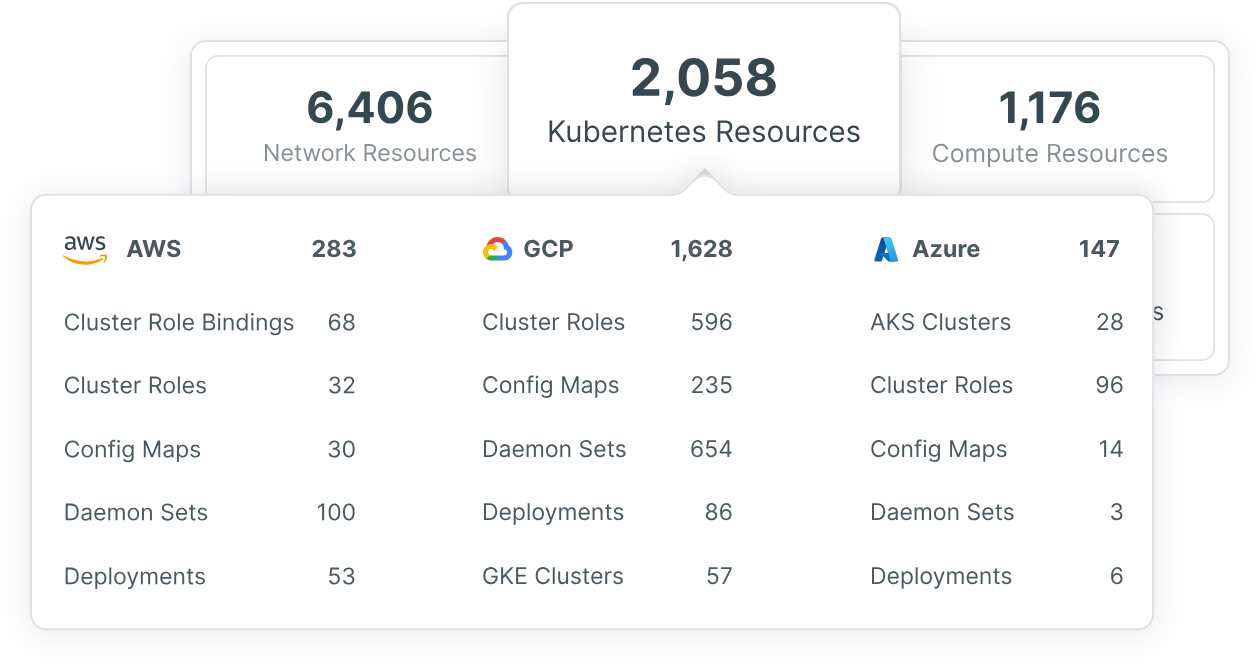
You can gain visibility into Kubernetes configurations and resources, including nodes, namespaces, deployments, servers and service accounts with an integrated Kubernetes security posture management (KSPM) tool like the one included in Tenable Cloud Security. With typical Kubernetes configurations built for speed and not necessarily for security, advanced risk analysis and configuration management is needed to surface identity and access management risks.
Tenable Cloud Security goes a step further in Kubernetes security to provide advanced risk analysis of all the users and services and generates fine-grained, least-privileged policies for remediation.
Resolution #9: Tap into your inner logs
Incident response and anomaly detection in the cloud can be challenging due to multiple factors, such as:
- gaps in data collection
- limited insight into cloud resources and their associated identities
- insufficient architecture detail
- lack of visibility into privileges
This is a pervasive issue that is exacerbated by multi-cloud environments. According to a report by Strata Identity, 76% of organizations do not have complete visibility into the access policies and applications across multiple cloud platforms. Needless to say, such challenges illustrate that security teams are lacking the tools they need to respond to incidents and anomalous activity.
What’s needed is enriched cloud-provider log data that provides resource-specific identity insights with continuous risk analysis. Tenable Cloud Security enables swift anomaly detection and response by enriching cloud provider log data with security insights – such as unusual data access, unexpected permissions modifications and privilege escalation – and with changes in logging for network configuration settings.
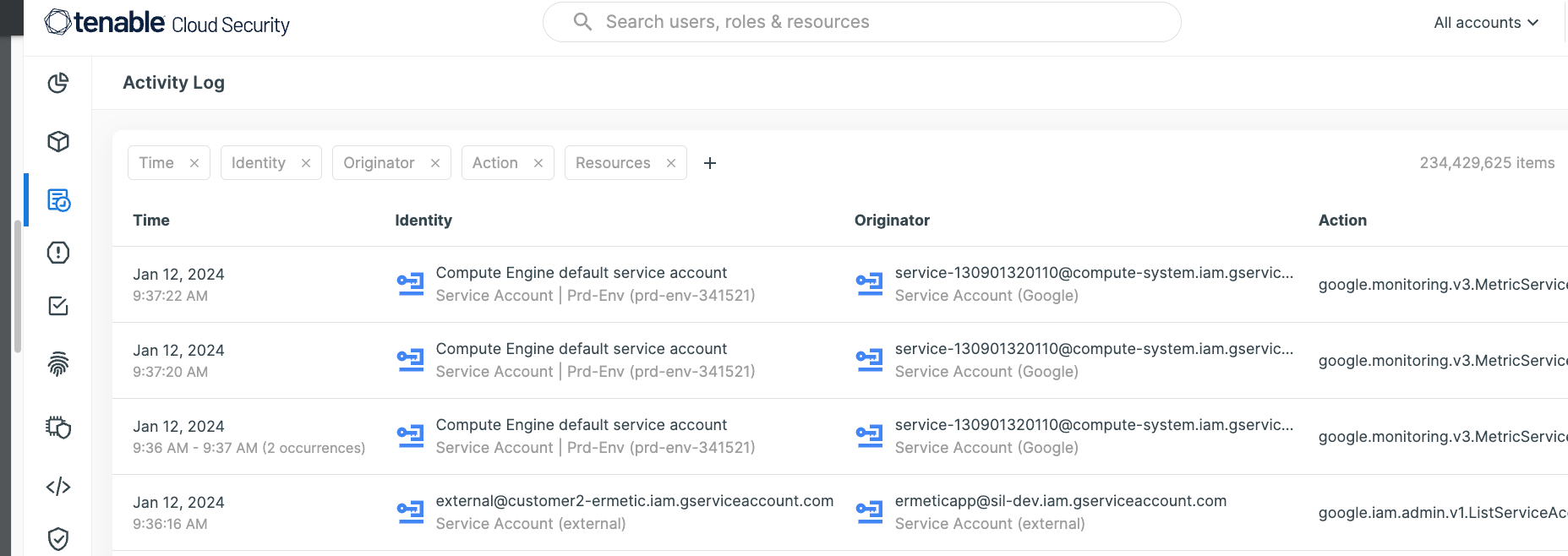
Resolution #10:Less is more. It’s time to CNAPP your security
A holistic security tool that covers all of these security resolutions in a single user experience is a cloud native application protection platform (CNAPP). Although there are so many security tools on the market, integration is key to create a strategy that will scale with your unique cloud environment.
Tenable Cloud Security provides unparalleled user experience and offers an intuitive platform that enables security teams to build successful cloud security programs that accelerate cloud adoption and reduce work.
For more information on the Tenable Cloud Security CNAPP and how you can integrate your security tools for improved efficiency, cost savings and reporting, register for the webinar “When, Why, and How Your Security Team Needs to Harness the Power of Cloud Native Application Security Platforms (CNAPPs)”. We also invite you to view this infographic and join the new Tenable Cloud Cover Community on LinkedIn and to visit https://www.tenable.com/products/tenable-cloud-security.
- Cloud


