ContiLeaks: Chats Reveal Over 30 Vulnerabilities Used by Conti Ransomware – How Tenable Can Help

Private messages between Conti members uncover invaluable information about how the infamous ransomware group hijacks victims’ systems.
Leaked internal chats between Conti ransomware group members offer a unique glimpse into its inner workings and provide valuable insights, including details on over 30 vulnerabilities used by the group and its affiliates, as well as specifics about its processes after infiltrating a network, like how it targets Active Directory.
In this blog post, we’ll offer background into Conti – one of the more prolific ransomware groups in operation today – dig into the leaked information, and offer concrete advice on how to protect your organization against Conti’s attacks.
Background
The ContiLeaks began on February 27 – the work of an alleged member of the Conti ransomware group. This individual leaked a series of internal chats between members of the group to the general public. This isn’t the first time confidential information about the group has been leaked. In August 2021, an affiliate of Conti published a playbook of training materials given to affiliates, which provided our first insight into the ransomware group’s operation.
These leaks have allowed researchers to analyze more of the tactics, techniques, and procedures developing indicators of compromise associated with the group. Researchers at Breach Quest published an article on March 9 analyzing the ContiLeaks, which included a list of vulnerabilities the group appears to have been using to target organizations.
What is Conti?
First discovered in 2020 by researchers at Carbon Black, Conti is a ransomware group that operates a ransomware-as-a-service model to deploy the Conti ransomware.
Ransomware-as-a-Service (RaaS) is offered by ransomware groups and gives affiliates — cybercriminals looking to partner with RaaS groups — access to ransomware that is ready to be deployed, as well as a playbook to help guide their attacks. RaaS groups take a small cut of paid ransoms, providing the bulk of the profits to affiliates.
Conti has risen to prominence over the last two years, earning a reported $180 million in profits from its attacks, according to Chainalysis. It’s also gained notoriety for attacks against the healthcare sector, including at least 16 U.S. health and emergency networks. Most notable was Conti’s attack on the Ireland Health Service Executive (HSE) in May 2021 in which the group demanded a $20 million ransom, which the HSE refused to pay.
Conti’s focus on the healthcare sector isn’t surprising. In our 2021 Threat Landscape Retrospective report, we found that 24.7% of healthcare data breaches were the result of ransomware attacks, and ransomware itself was responsible for 38% of all breaches publicly disclosed last year.
Which vulnerabilities are Conti and its affiliates using?
Ransomware groups like Conti use a variety of tactics to breach the networks of prospective targets. These include phishing, malware and brute force attacks against Remote Desktop Protocol.
Conti has also been linked to EXOTIC LILY, an initial access broker (IAB) group. IABs are focused on obtaining malicious access to organizations for the purpose of selling that access to ransomware groups and affiliates. However, exploiting pre-and-post authentication vulnerabilities also play an important role in ransomware attacks.
As part of the leaked affiliate playbook, we’ve seen reports that Conti and its affiliates have been using the PrintNightmare and Zerologon vulnerabilities against targets. However, the ContiLeaks revealed an additional 29 vulnerabilities used by the group.
Additionally, there are reports that Conti and its affiliates have targeted vulnerabilities in the Fortinet FortiOS found in Fortinet’s SSL VPN devices to gain initial access to target environments.
The following is a breakdown of the types of vulnerabilities used by Conti and its affiliates:
Initial access vulnerabilities
| CVE | Description | CVSS Score | VPR |
|---|---|---|---|
| CVE-2018-13379 | Fortinet FortiOS Path Traversal/Arbitrary File Read Vulnerability | 9.8 | 9.8 |
| CVE-2018-13374 | Fortinet FortiOS Improper Access Control Vulnerability | 8.8 | 8.4 |
| CVE-2020-0796 | Windows SMBv3 Client/Server Remote Code Execution Vulnerability (“SMBGhost”) | 10 | 10.0 |
| CVE-2020-0609 | Windows Remote Desktop Gateway (RD Gateway) Remote Code Execution Vulnerability | 9.8 | 8.4 |
| CVE-2020-0688 | Microsoft Exchange Validation Key Remote Code Execution Vulnerability | 8.8 | 9.9 |
| CVE-2021-21972 | VMware vSphere Client Remote Code Execution Vulnerability | 9.8 | 9.5 |
| CVE-2021-21985 | VMware vSphere Client Remote Code Execution Vulnerability | 9.8 | 9.4 |
| CVE-2021-22005 | VMware vCenter Server Remote Code Execution Vulnerability | 9.8 | 9.6 |
| CVE-2021-26855 | Microsoft Exchange Server Remote Code Execution Vulnerability ("ProxyLogon") | 9.8 | 9.9 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was published on March 24 and reflects VPR at that time.
Elevation of privilege vulnerabilities
| CVE | Description | CVSS Score | VPR |
|---|---|---|---|
| CVE-2015-2546 | Win32k Memory Corruption Elevation of Privilege Vulnerability | 6.9 | 9.6 |
| CVE-2016-3309 | Windows Win32k Elevation of Privilege Vulnerability | 7.8 | 9.7 |
| CVE-2017-0101 | Windows Elevation of Privilege Vulnerability | 7.8 | 9.7 |
| CVE-2018-8120 | Windows Win32k Elevation of Privilege Vulnerability | 7 | 9.8 |
| CVE-2019-0543 | Microsoft Windows Elevation of Privilege Vulnerability | 7.8 | 9.0 |
| CVE-2019-0841 | Windows Elevation of Privilege Vulnerability | 7.8 | 9.8 |
| CVE-2019-1064 | Windows Elevation of Privilege Vulnerability | 7.8 | 9.2 |
| CVE-2019-1069 | Windows Task Scheduler Elevation of Privilege Vulnerability | 7.8 | 9.0 |
| CVE-2019-1129 | Windows Elevation of Privilege Vulnerability | 7.8 | 8.9 |
| CVE-2019-1130 | Windows Elevation of Privilege Vulnerability | 7.8 | 6.7 |
| CVE-2019-1215 | Windows Elevation of Privilege Vulnerability | 7.8 | 9.5 |
| CVE-2019-1253 | Windows Elevation of Privilege Vulnerability | 7.8 | 9.7 |
| CVE-2019-1315 | Windows Error Reporting Manager Elevation of Privilege Vulnerability | 7.8 | 9.0 |
| CVE-2019-1322 | Microsoft Windows Elevation of Privilege Vulnerability | 7.8 | 9.0 |
| CVE-2019-1385 | Windows AppX Deployment Extensions Elevation of Privilege Vulnerability | 7.8 | 5.9 |
| CVE-2019-1388 | Windows Certificate Dialog Elevation of Privilege Vulnerability | 7.8 | 8.4 |
| CVE-2019-1405 | Windows UPnP Service Elevation of Privilege Vulnerability | 7.8 | 9.7 |
| CVE-2019-1458 | Win32k Elevation of Privilege Vulnerability | 7.8 | 9.7 |
| CVE-2020-0638 | Update Notification Manager Elevation of Privilege Vulnerability | 7.8 | 5.9 |
| CVE-2020-0787 | Windows Background Intelligent Transfer Service Elevation of Privilege Vulnerability | 7.8 | 9.7 |
| CVE-2020-1472 | Windows Netlogon Elevation of Privilege Vulnerability ("Zerologon") | 10 | 10.0 |
| CVE-2021-1675 | Windows Print Spooler Remote Code Execution Vulnerability | 8.8 | 9.8 |
| CVE-2021-1732 | Windows Win32k Elevation of Privilege Vulnerability | 7.8 | 9.8 |
| CVE-2021-34527 | Windows Print Spooler Remote Code Execution Vulnerability ("PrintNightmare") | 8.8 | 9.8 |
We’re also aware that Conti and its affiliates have used CVE-2021-44228, also known as Log4Shell, as part of attacks beginning in late 2021.
Leveraging elevation of privilege vulnerabilities
When looking at the impact of the various vulnerabilities disclosed specifically within the ContiLeaks communications, an interesting pattern emerges: nearly three quarters of the vulnerabilities on the list are elevation of privilege flaws, which signifies that the group is largely using vulnerabilities that support post-exploitation activities.
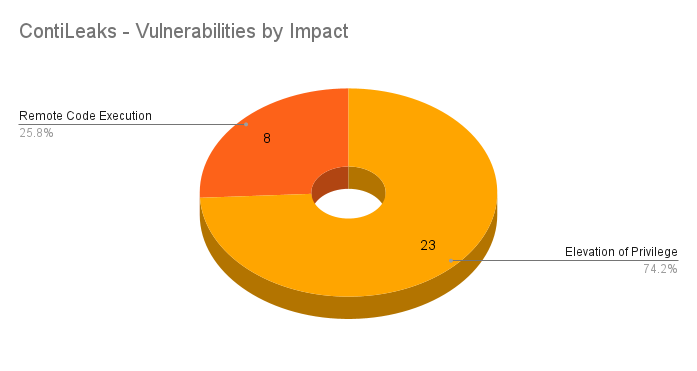
Given that the group and its affiliates can find different entry points into an organization outside of vulnerabilities, but need to elevate privileges in order to wreak havoc, it is not surprising that most of their vulnerability toolkit is focused on elevation of privileges.
Conti and Active Directory
Through the ContiLeaks, we learned that Conti follows a set of processes once inside a network. To target Active Directory (AD), the group will seek out domain administrator privileges, as is common amongst ransomware. For ransomware groups, AD is a valuable tool to help achieve their intended goal of encrypting systems across an organization’s network.
Conti and its affiliates will try to leverage Zerologon to obtain domain admin privileges, or they will seek out “potentially interesting people” within an organization’s AD according to BreachQuest.
The group and its affiliates target AD through a variety of means including:
Solution
The majority of vulnerabilities used by the Conti ransomware group and its affiliates have been patched over the last few years. The oldest flaw on this list was patched six years ago in 2015.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities can be found here.
To enable our customers to identify all of the known vulnerabilities leveraged by the Conti ransomware group and its affiliates, we will be releasing scan templates soon, while dashboards for Tenable.io, Tenable.sc and Nessus Professional are available now.

ContiLeaks Scan Template
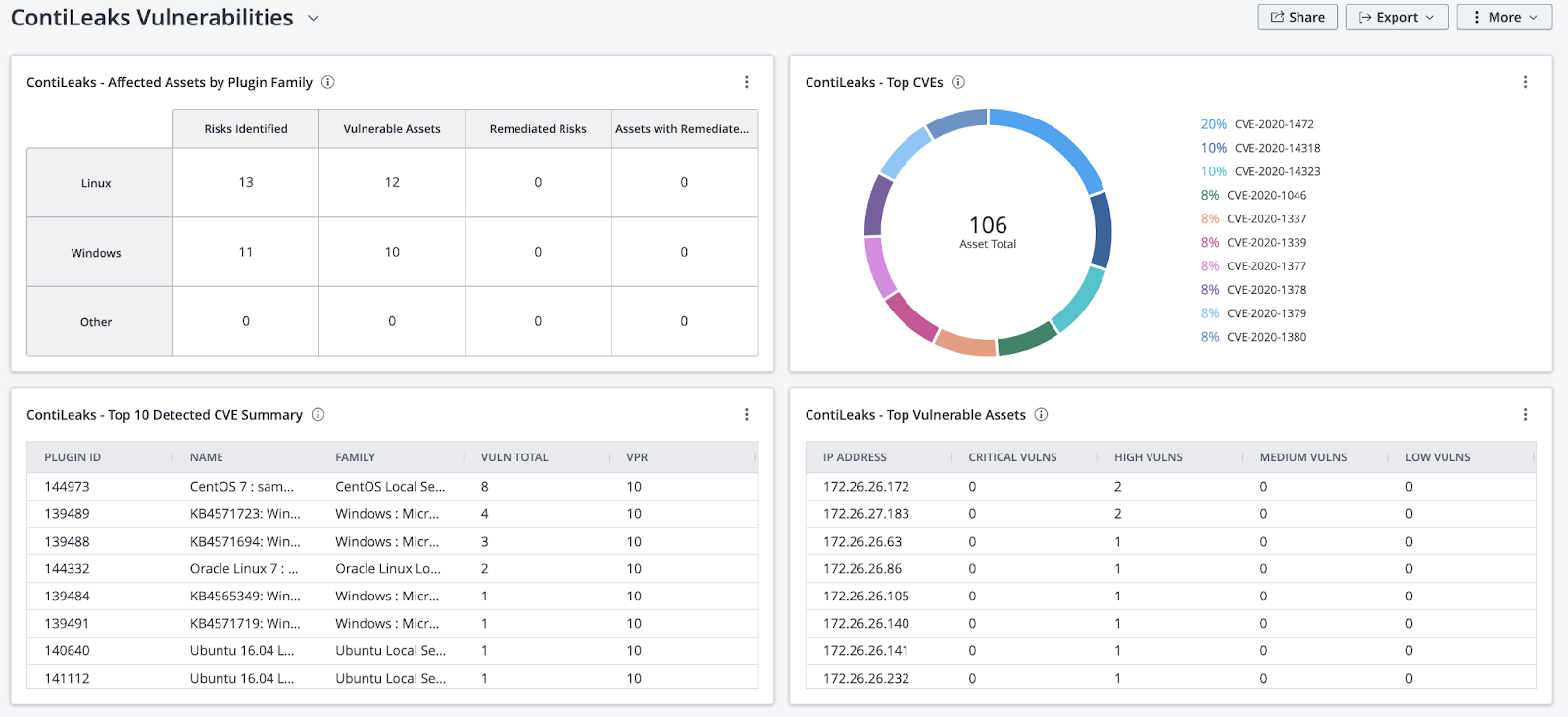
ContiLeaks Dashboard for Tenable.io
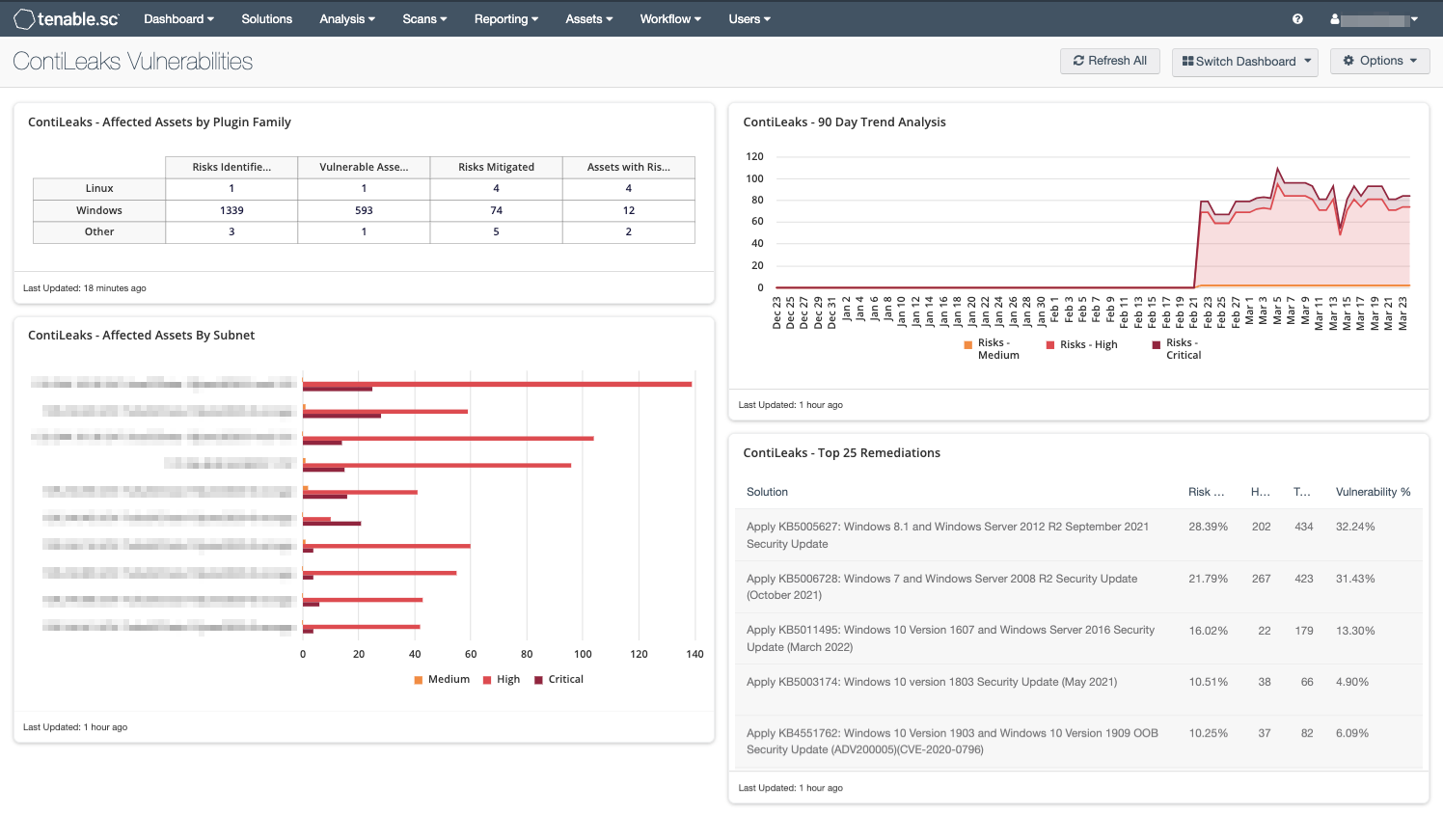
ContiLeaks Dashboard for Tenable.sc
ContiLeaks Report from Tenable.sc
For more information on the dashboards and reports, please refer to the following articles:
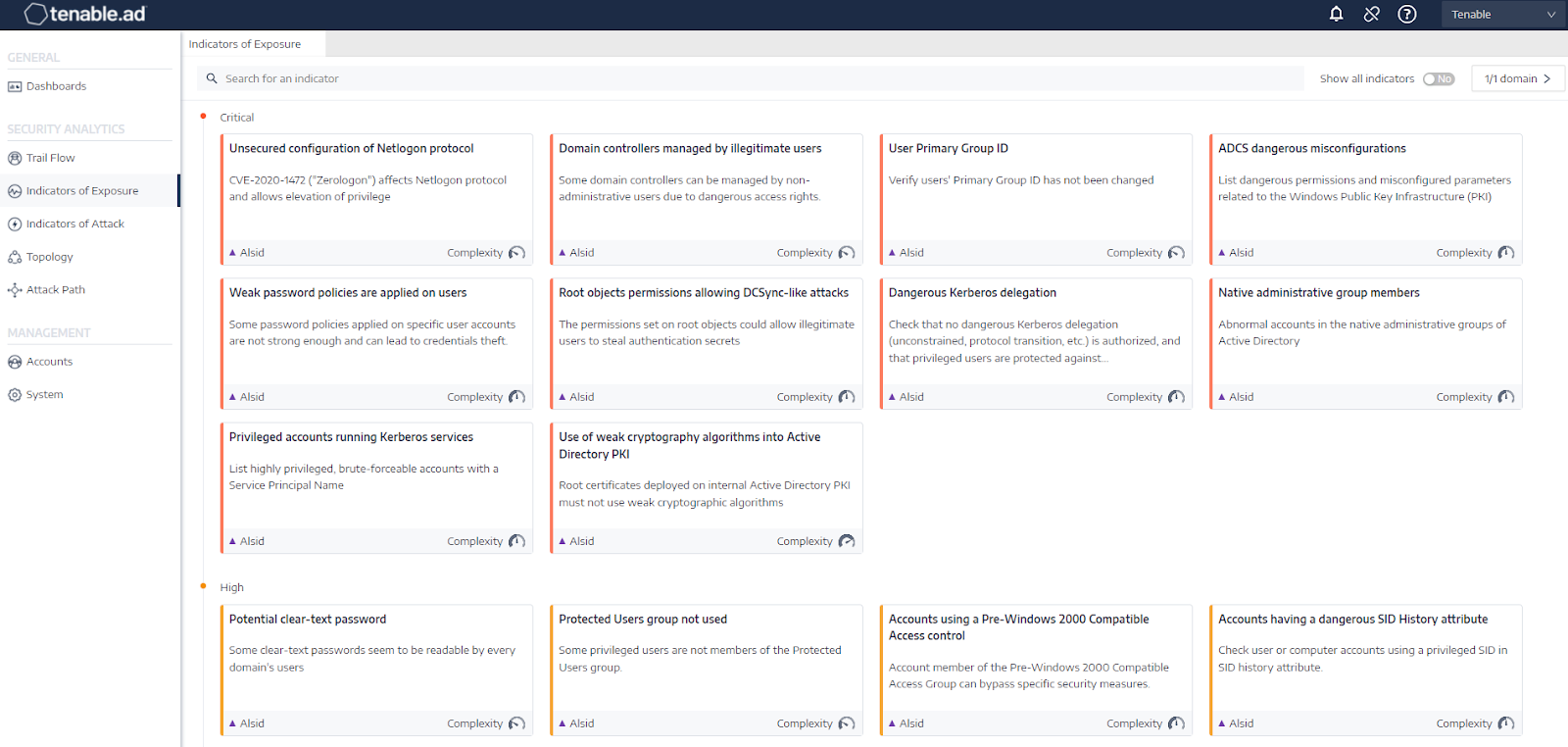
Indicators of Exposure view in Tenable.ad
For Tenable.ad customers, we have detection and prevention solutions in the form of Indicators of Exposure (IoE) and Indicators of Attack (IoA). IoEs are a preemptive way to find and address gaps within your AD infrastructure to eliminate attack paths for ransomware groups and other cybercriminals, while IoAs detect attacks in real time.
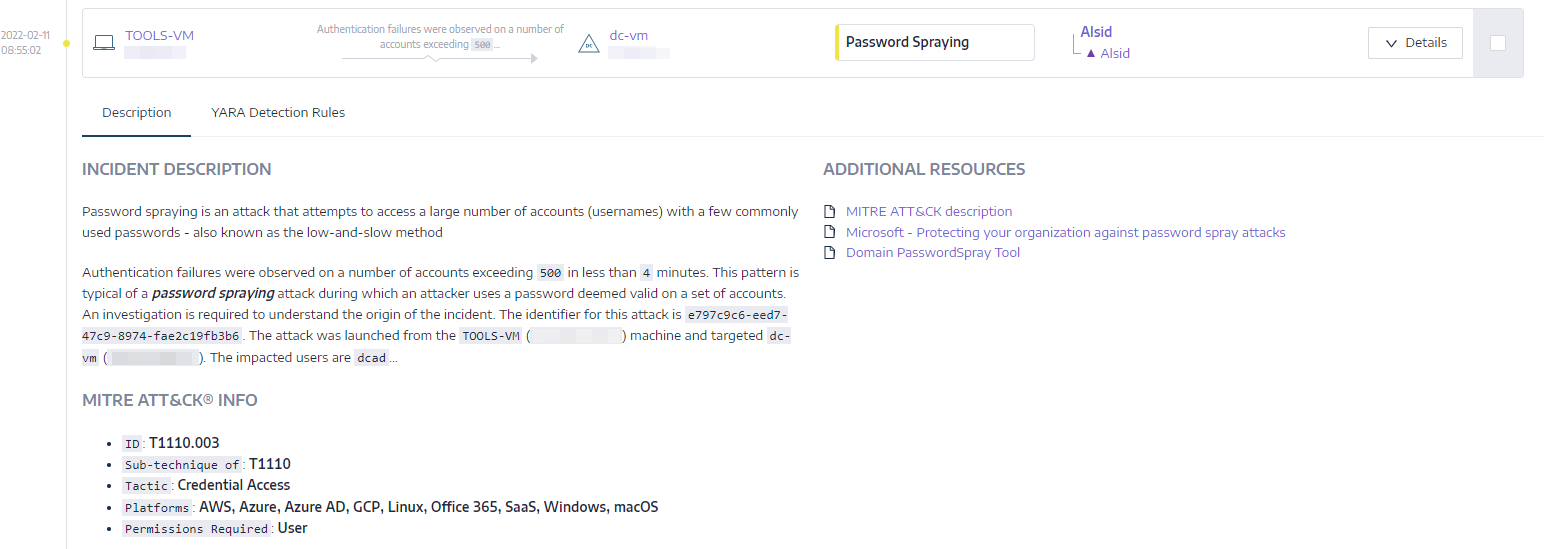
Example IOA alert for password spraying
The following is a list of IoEs and IoAs derived from the findings within the ContiLeaks:
| Tactics | MITRE ATT&CK | Solutions | Type |
|---|---|---|---|
| Discovery (e.g. BloodHound) | T1087.001, T1087.002, T1106, T1069.001, T1069.002 | Enumeration of local administratorsMassive computers reconnaissance | IoA |
| Privilege Escalation (Golden Ticket) | T1558.001 | GoldenTicket | IoA |
| Privilege Escalation (Zerologon) | T1068 | Unsecured configuration of Netlogon protocol | IoE |
| Credential Access (Bruteforce, Password Spraying) | T1110.001, T1110.002, T1110.003, T1110.004 | Password GuessingPassword Spraying | IoA |
| Credential Access (Collection and decryption of GPP Passwords) | T1552.006 | Reversible passwords in GPO | IoE |
| Credential Access (ntds.dit) | T1003.003 | NTDS Extraction | IoA |
| Credential Access (Encrypted Passwords) | T1003.003 | Reversible passwords | IoE |
| Credential Access (Kerberoasting) | T1558.003 | Kerberoasting | IoA |
| Credential Access (Mimikatz) | T1003.001 | OS Credential Dumping: LSASS Memory | IoA |
Get more information
- Conti ransomware gang chats leaked by pro-Ukraine member
- The Conti Leaks | Insight into a Ransomware Unicorn
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
