CVE-2021-34527: Microsoft Releases Out-of-Band Patch for PrintNightmare Vulnerability in Windows Print Spooler

Microsoft issues an out-of-band patch for critical ‘PrintNightmare’ vulnerability following reports of in-the-wild exploitation and publication of multiple proof-of-concept exploit scripts
Update July 9, 2021: The Solution section has been updated to clarify the vulnerable configurations as well as a mitigation to ensure exploitation is not feasible post-patch
Background
On July 6, Microsoft updated its advisory to announce the availability of out-of-band (OOB) patches for a critical vulnerability in its Windows Print Spooler that researchers are calling PrintNightmare. This remote code execution (RCE) vulnerability affects all versions of Microsoft Windows.
| CVE | Description | CVSSv3 | VPR* |
|---|---|---|---|
| CVE-2021-34527 | Windows Print Spooler Remote Code Execution Vulnerability | 8.8 | 9.6 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was published on July 7 and reflects VPR at that time.
Microsoft originally released its advisory for CVE-2021-34527 on July 1. This advisory was released in response to public reports about a proof-of-concept (PoC) exploit for CVE-2021-1675, a similar vulnerability in the Windows Print Spooler. To help clear up confusion about the vulnerability, Microsoft updated its advisory for CVE-2021-1675 to clarify that it is “similar but distinct from CVE-2021-34527.”
Analysis
CVE-2021-34527 is an RCE vulnerability in the Windows Print Spooler Service, which is available across desktop and server versions of Windows operating systems. The service is used to manage printers and print servers. The vulnerability exists because the service does not handle privileged file operations properly.
An authenticated, remote or local attacker, could exploit this flaw in order to gain arbitrary code execution with SYSTEM privileges.
Research community actively developing PoC exploits for PrintNightmare
Since July 1, researchers have been diligently developing PoCs for PrintNightmare. At the time this blog post was published, there were at least 34 public PoC exploit scripts for PrintNightmare on GitHub.
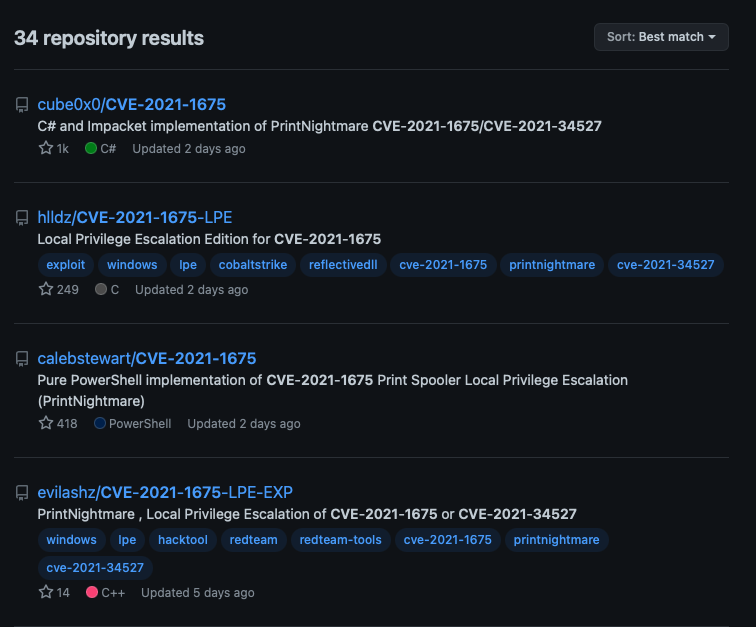
These PoCs include scripts that can achieve local privilege escalation (LPE) on a targeted system, as well as remote code execution.
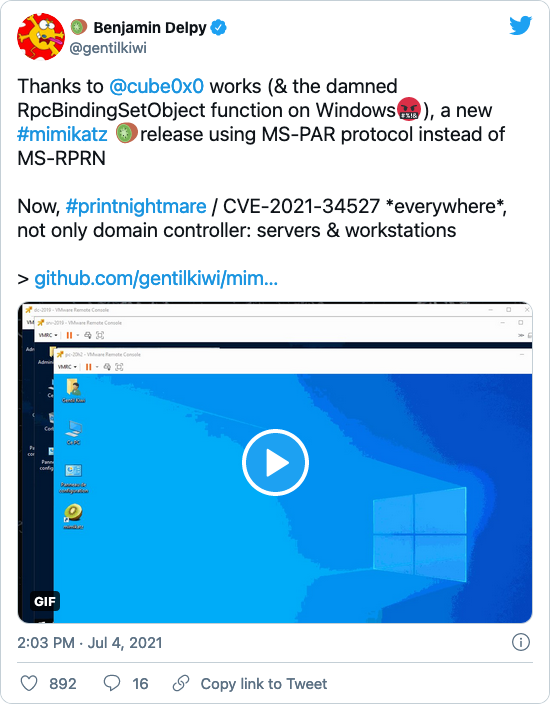
Previous PoCs relied on the Microsoft Print System Remote Protocol (MS-RPRN) to exploit PrintNightmare. However, on July 3, a researcher going by the nickname cube0x0, developed a PoC called SharpPrintNightmare, which uses the Microsoft Print System Asynchronous Remote Protocol (MS-PAR) instead, which confirmed that PrintNightmare could be successfully exploited against servers and desktop systems as well as domain controllers.
Disabling spooler on just your DC's is not enough #PrintNightmare pic.twitter.com/IJJ2S2Ejxs
— Cube0x0 (@cube0x0) July 3, 2021
Benjamin Delpy, developer of the comprehensive post-exploitation tool Mimikatz, updated the software to add support for the PrintNightmare exploit using cube0x0’s method.
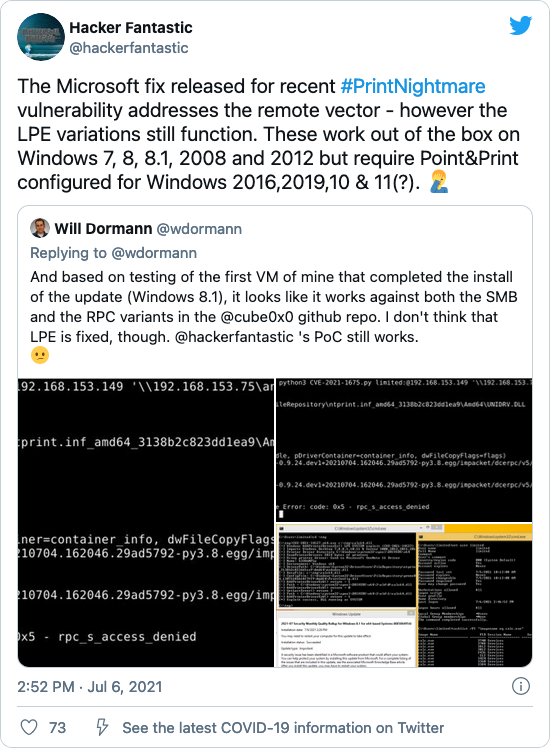
Researchers say Microsoft’s patch is incomplete
At the time this blog post was published, several researchers including Kevin Beaumont, Will Dormann and Hacker Fantastic, have pointed out that the fix for PrintNightmare is incomplete, as the LPE still works successfully post-patch, both “out of the box” as well as under certain configurations.
Additionally, there are reports that both RCE and LPE is still feasible post-patch, so long as the Point and Print configuration is enabled.
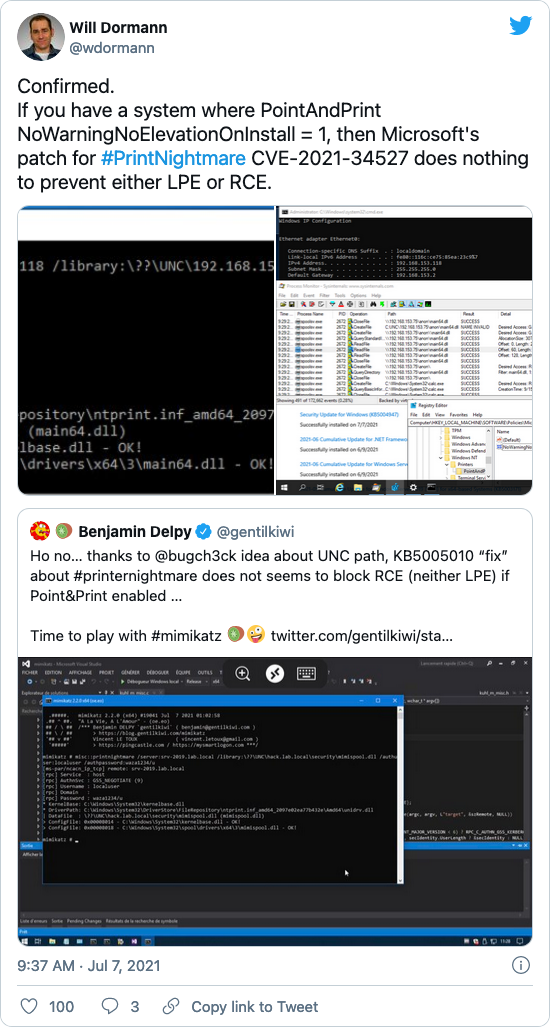
Tenable has not independently confirmed these findings.
Proof of concept
As mentioned above, there are a number of PoC exploit scripts for PrintNightmare available on GitHub.
Solution
As of July 7, Microsoft released patches for a number of different Windows releases. The following table can be used to reference each patch and its associated knowledge base entry.
| Affected Version | Knowledge Base Article | Patch |
|---|---|---|
| Windows 7 for 32-bit systems Service Pack 1 Windows 7 for x64-based Systems Service Pack 1 Windows Server 2008 R2 for x64-based Systems Service Pack 1 Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation) |
5004953 | Monthly Rollup |
|
Windows 7 for 32-bit systems Service Pack 1 |
5004951 | Security Only |
| Windows 8.1 for 32-bit systems Windows 8.1 for x64-based systems Windows Server 2012 R2 Windows Server 2012 R2 (Server Core installation) |
5004954 | Monthly Rollup |
| Windows 8.1 for 32-bit systems Windows 8.1 for x64-based systems Windows Server 2012 R2 Windows Server 2012 R2 (Server Core installation) |
5004958 | Security Only |
| Windows Server 2008 for 32-bit Systems Service Pack 2 Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) Windows Server 2008 for x64-based Systems Service Pack 2 Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) |
5004955 | Monthly Rollup |
| Windows Server 2008 for 32-bit Systems Service Pack 2 Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation) Windows Server 2008 for x64-based Systems Service Pack 2 Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation) |
5004959 | Security Only |
| Windows 10 for 32-bit Systems Windows 10 for x64-based Systems | 5004950 | Security Update |
| Windows 10 Version 21H1 for x64-based Systems Windows 10 Version 21H1 for ARM64-based Systems Windows 10 Version 21H1 for 32-bit Systems Windows 10 Version 2004 for 32-bit Systems Windows 10 Version 2004 for ARM64-based Systems Windows 10 Version 2004 for x64-based Systems Windows Server, version 2004 (Server Core installation) Windows 10 Version 20H2 for 32-bit Systems Windows 10 Version 20H2 for x64-based Systems Windows 10 Version 20H2 for ARM64-based Systems Windows Server, version 20H2 (Server Core Installation) |
5004945 | Security Update |
| Windows 10 Version 1909 for 32-bit Systems Windows 10 Version 1909 for x64-based Systems Windows 10 Version 1909 for ARM64-based Systems |
5004946 | Security Update |
| Windows 10 Version 1809 for 32-bit Systems Windows 10 Version 1809 for x64-based Systems Windows 10 Version 1809 for ARM64-based Systems Windows Server 2019 Windows Server 2019 (Server Core installation) |
5004947 | Security Update |
| Windows 10 Version 1607 for 32-bit Systems Windows 10 Version 1607 for x64-based Systems Windows Server 2016 Windows Server 2016 (Server Core installation) |
5004948 | Security Update |
| Windows RT 8.1 | 5004954 | Unavailable |
Microsoft updated its advisory on July 7 to address the Point and Print aspect of this vulnerability. Specifically, they mention that while Point and Print is “not directly related to this vulnerability” its usage “weakens the local security posture” allowing for exploitation even if patches have been applied.
After applying the OOB patch, customers are advised to check the Windows registry for the presence of the following keys:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
NoWarningNoElevationOnInstall = 0 (DWORD) or not defined (default setting)
UpdatePromptSettings = 0 (DWORD) or not defined (default setting)
Additionally, customers are advised to check their Group Policy to ensure that the Point and Print Restrictions Group Policy has NOT been configured.
If either the registry settings above are present or the group policy setting has been configured, then exploitation of PrintNightmare is still possible.
To mitigate Point and Print, Microsoft recommends modifying the registry keys by setting both NoWarningNoElevationOnInstall and UpdatePromptSettings as follows:
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
NoWarningNoElevationOnInstall = 0 (DWORD)
UpdatePromptSettings = 0 (DWORD)
Additionally, Microsoft Security Response Center released a blog post to announce that the cumulative patch released for CVE-2021-34527 also includes a new feature that provides users with the ability to allow non-administrative users to only install signed printer drivers which are trusted by “the installed root certificates in the system’s Trusted Root Certification Authorities”. More information on these enhanced security controls can be found in Microsoft KB5005010.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability will appear here as they’re released. Customers can also utilize plugin ID 151440 to identify systems which have the print spooler service (spoolsv.exe) enabled. A compliance audit file is also available here to check for the existence of the workaround suggestions from Microsoft as well as if the patch settings are in place for NoWarningNoElevationOnInstall and UpdatePromptSettings.
Get more information
- Microsoft Advisory for CVE-2021-34527
- Microsoft Security Response Center Blog Post for CVE-2021-34527
- Tenable Blog Post for CVE-2021-1675
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


