Haga cumplir los privilegios mínimos en la nube y dimensione correctamente los permisos a escala
Reduzca los privilegios excesivos, los habilitadores silenciosos de la pérdida de datos y el movimiento lateral, y permita la aplicación continua de los privilegios mínimos con Tenable Cloud Security. Analice los patrones de acceso, marque los roles con exceso de privilegios y automatice el acceso justo a tiempo sin frenar a los desarrolladores.
Asegúrese de que la seguridad siga el ciclo de vida de las identidades
Cambie del acceso persistente a los permisos justo a tiempo.
Gestione el gobierno de identidades con Tenable Cloud Security
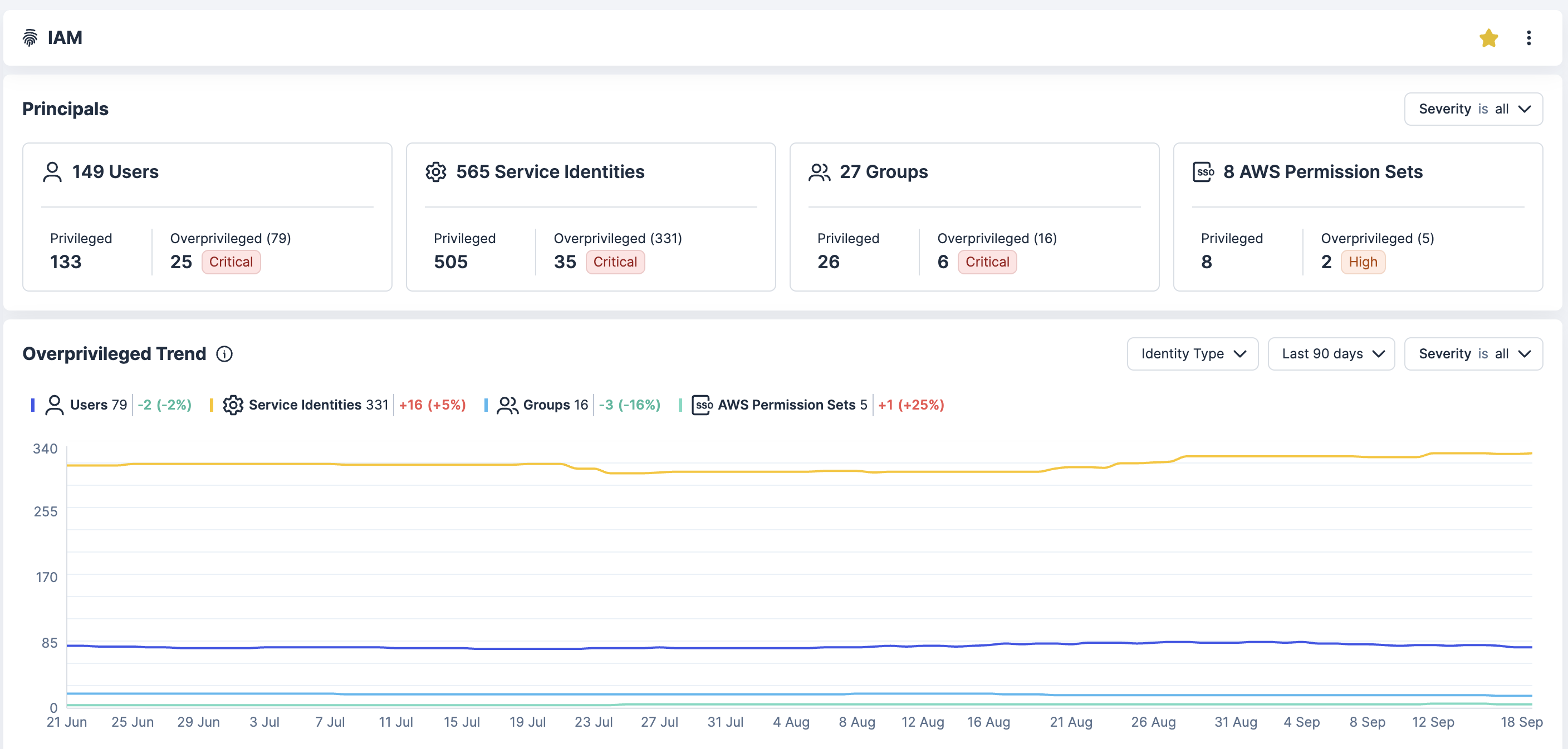
Reduzca los permisos excesivos en la nube, una de las principales causas de vulneraciones y auditorías fallidas. Reduzca el radio de ataque a las identidades con visibilidad, automatización y aplicación de políticas que se alineen con las prácticas recomendadas de privilegios mínimos.
Detecte identidades y derechos
Obtenga visibilidad completa hacia todas las identidades de AWS, Azure, GCP y Kubernetes, incluidos usuarios humanos, cuentas de servicio e integraciones de terceros. Detecte cuentas huérfanas, roles no utilizados y derechos excesivos
Analice el riesgo de los privilegios
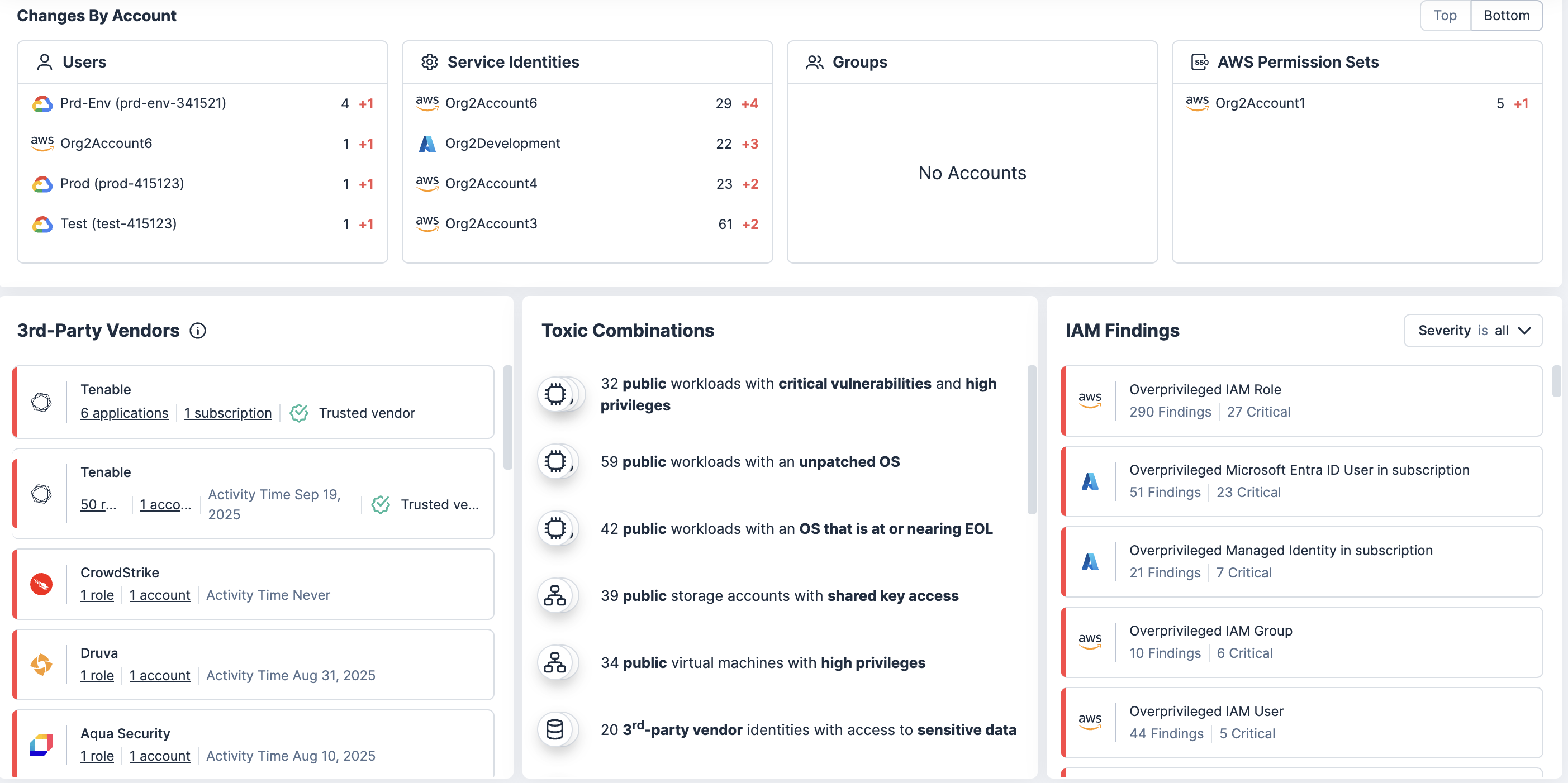
Analice políticas, membresías de grupos y suposiciones de roles para detectar riesgos de escalación de privilegios y oportunidades de movimiento lateral. Este contexto ayuda a sus equipos a eliminar las rutas de alto riesgo.
Obtenga correlación y priorización contextuales
Correlacione los permisos excesivos con vulnerabilidades, errores de configuración y datos confidenciales para saber dónde podría tener el mayor impacto el uso indebido de privilegios.
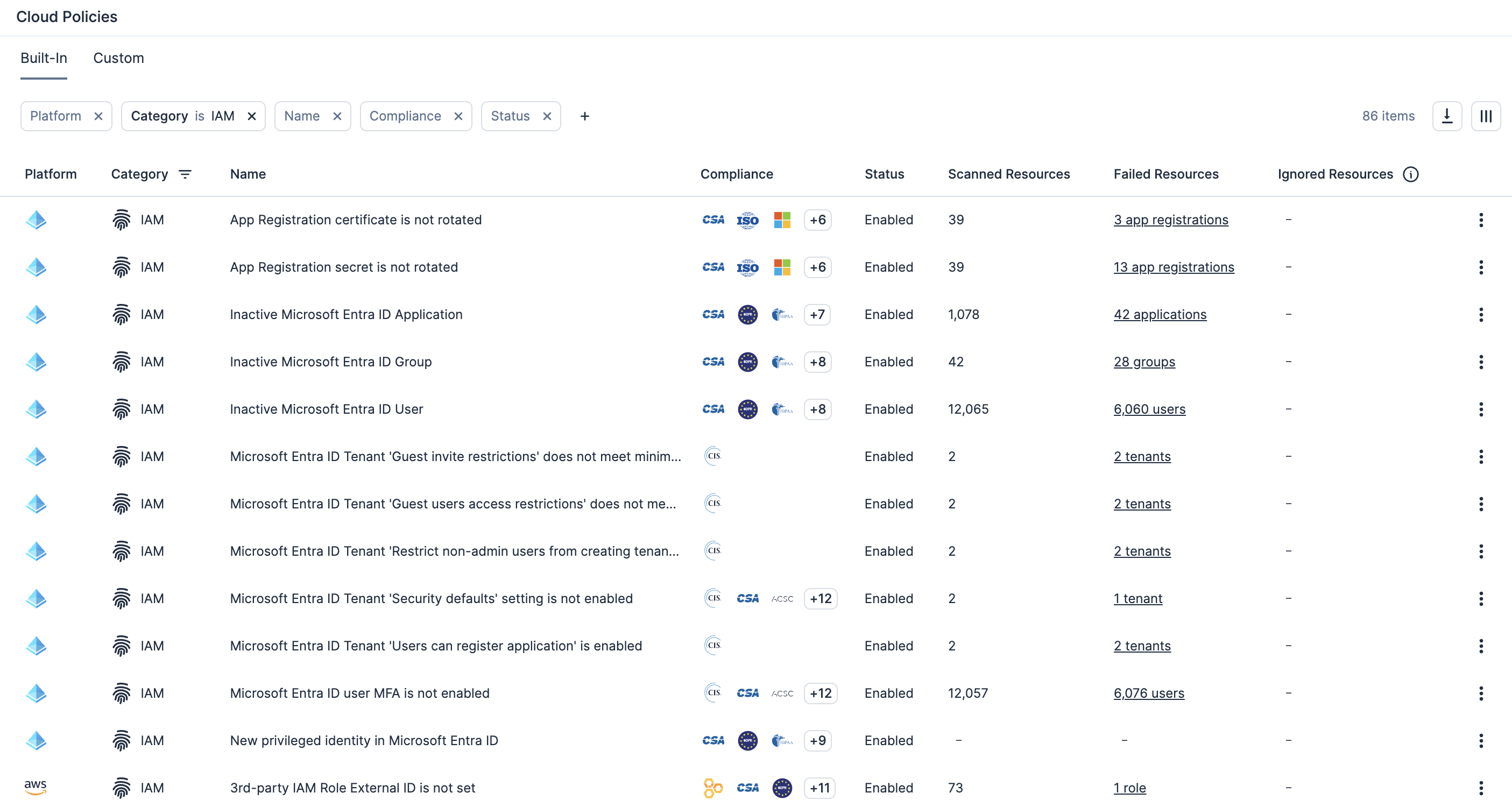
Haga cumplir las políticas personalizadas y la corrección automatizada
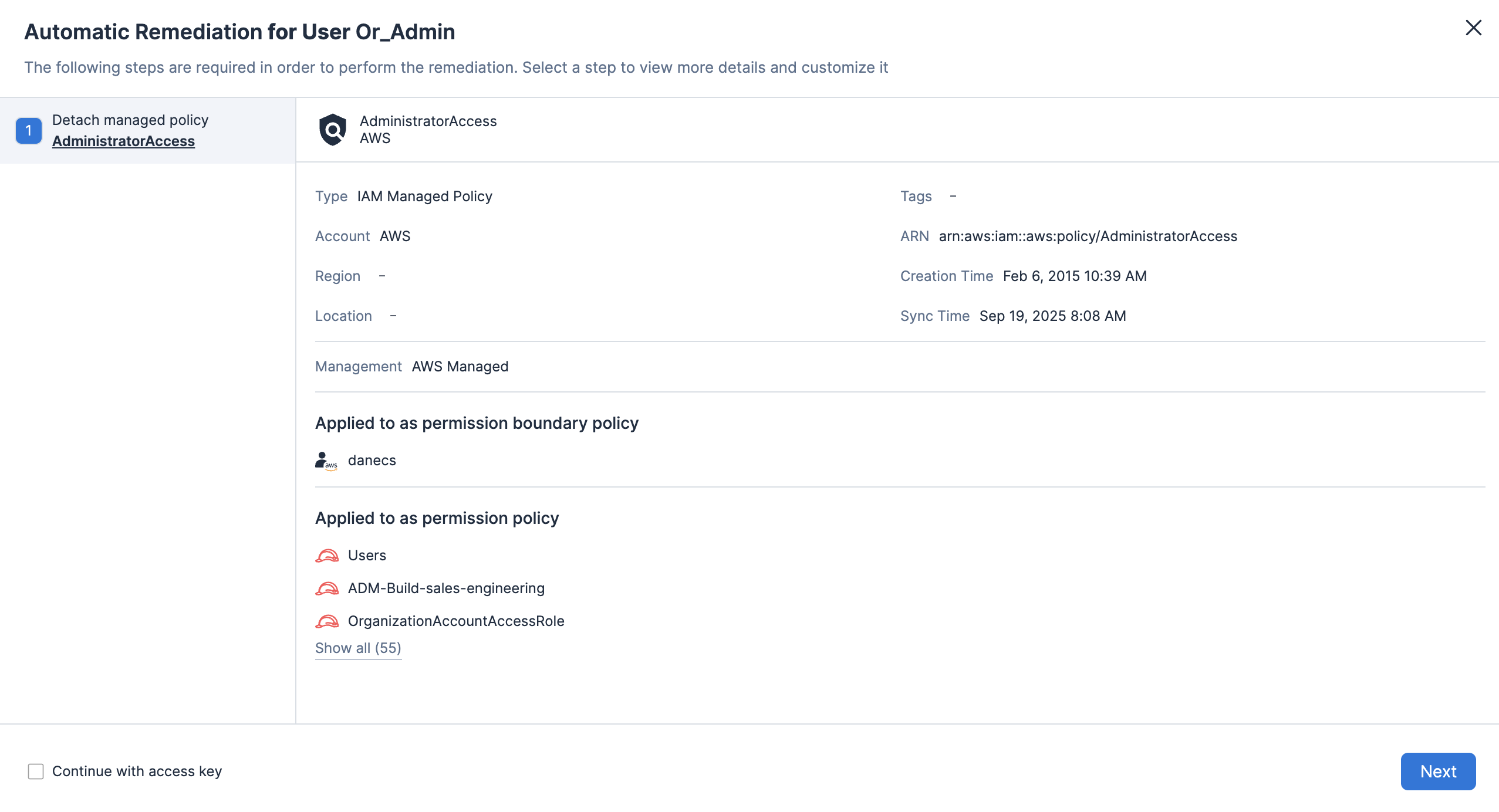
Habilite la definición de políticas personalizadas para detectar permisos excesivos o configuraciones riesgosas en recursos y, a continuación, active automáticamente flujos de trabajo de corrección.
Integre la CIEM con Tenable One
Haga cumplir continuamente los privilegios mínimos con Gestión de derechos de infraestructura en la nube (CIEM) para garantizar que los permisos sean suficientes, justo a tiempo y nunca excesivos.
Obtenga más información sobre Tenable Cloud Security
El uso de la automatización [de Tenable Cloud Security] nos permitió eliminar procesos manuales exhaustivos y realizar en minutos lo que le habría llevado a dos o tres profesionales de seguridad meses.
- Tenable Cloud Security