Exploring the Exposure Management Maturity Model

Each Monday, the Tenable Exposure Management Academy provides the practical, real-world guidance you need to shift from vulnerability management to exposure management. In the first of a two-part blog series, Tenable’s Pierre Coyne guides you through the Tenable Exposure Management Maturity Model. You can read the entire Exposure Management Academy series here.
Key takeaways:
- Cybersecurity programs mature across five distinct levels, often plateauing at the third stage, Standardized. Traditional siloed security approaches limit the ability to scale and drive greater value, which makes it hard to keep pace with threats despite significant investment.
- Exposure management helps you advance beyond traditional security silos and achieve higher levels of maturity. It bridges data gaps by unifying and enriching asset and risk data with critical relationship context, enabling better insights, productivity and effectiveness.
- Exposure management involves ongoing assessment and adaptation at every stage of an organization's security maturity, ensuring a robust and evolving defense against emerging threats.
Over the years, Tenable has worked with thousands of clients across industries to develop their cybersecurity programs and realize better outcomes.
Although every business and program is unique, there are common patterns in how organizations progress their proactive cybersecurity programs over time. Equally enlightening, despite continued investment in staffing and tools, even the most mature programs seem to reach a plateau, where they have trouble scaling and driving greater value from their investments.
Why is that? Mainly because of the siloed nature of security. Traditional siloed security, although it delivers incremental improvements in visibility, lacks critical relationship context needed to drive high value insights.
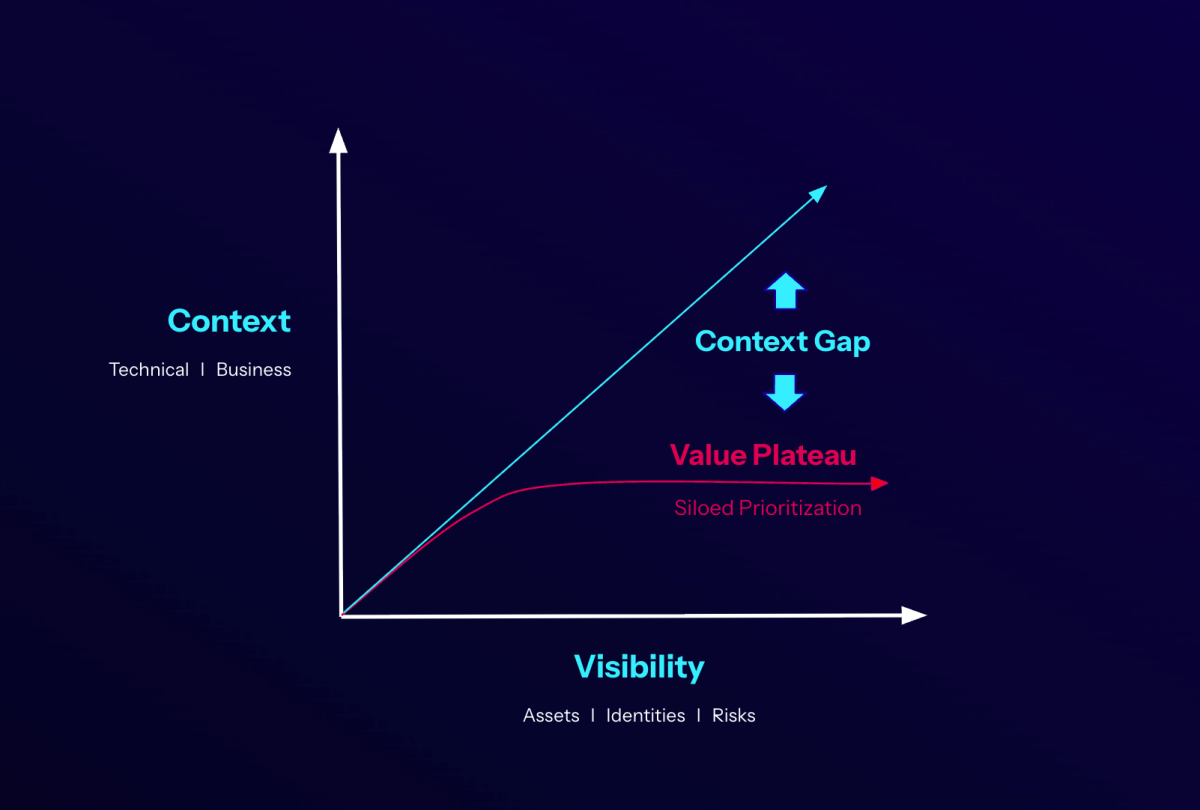
This is where exposure management comes in. Exposure management helps bridge silos and, more importantly, deliver critical context to fuel better insights, productivity and effectiveness. As a result, it takes cybersecurity maturity to new levels.
As the leader in proactive security that pioneered exposure management, Tenable has found that program maturity moves across five levels: Ad Hoc, Defined, Standardized, Advanced and Optimized. At the low end of the spectrum, security is siloed and teams lack an understanding of the cross-domain relationships that attackers exploit. The focus is on individual findings, which makes less mature programs inefficient. At the high end of the spectrum, organizations have unified their data, enriched it with context about the relationship between assets and identities, and they focus on exposure to cut through the noise.
Let’s walk through the common characteristics that define each level. (Also, see our one-pager on the five stages of exposure management maturity.)

Exposure Management Maturity Model Stage 1: Ad Hoc
Ad Hoc characteristics:
- Limited tools (e.g., Nessus)
- Highly reactive
- No defined processes
Ad Hoc is the lowest level of maturity, where security is a part-time job. Typically, organizations have very small teams of generalists wearing both IT and security hats. If you’re at this level, you probably also have minimal tooling and may be reliant on free security scanners, such as vulnerability assessment tools, or security functionality provided within existing IT tools.
Scanning is infrequent. As a result, there are large gaps in visibility and regular fire drills. Teams are typically reactive and focused on keeping the lights on rather than proactive reduction of the viable attack surface.
At this stage, you probably have no documented processes or best practices in place.
Which stage of exposure management maturity best defines your organization? You may be more advanced than you think. Take our exposure management maturity assessment to find out.
Exposure Management Maturity Model Stage 2: Defined
Defined characteristics:
- Priority siloed tools (e.g., vulnerability management and web application scanning)
- Manual, documented processes
- Some best practices
Organizations at this stage have defined some initial security silos based on the existing scope of infrastructure and organizational priorities. Most organizations will now have a vulnerability management program in place. Although scanning is periodic, it’s frequently limited to servers and endpoints.
At the Defined stage, you may have dedicated staff and tools in place to cover other security domains, such as web application scanning or cloud security posture management (CSPM).
With siloed operations and a lack of holistic tooling and integration, you probably have visibility gaps across shadow IT, OT, IoT and third-party SaaS. The volume of findings and limited context means you and your analysts spend many hours manually correlating and sifting through the noise.
Exposure Management Maturity Model Stage 3: Standardized
Standardized characteristics:
- Robust siloed toolset (e.g., risk-based vulnerability management, cloud-native application protection platforms and others)
- Mature processes, with higher automation
- Difficulty scaling
Reflecting some of the most mature security organizations and largest budgets in the world, this level of maturity is often where organizations reach a plateau. At this point, you have invested in the broadest range of specialized, best-of-breed tools to assess every individual security domain across the extended attack surface. You have highly skilled, certified and dedicated staff aligned to each domain. You’ve also documented processes and might even be utilizing greater levels of automation.
To better support business priorities, organizations have implemented tagging and enhanced risk prioritization, such as risk-based vulnerability management, which factors in asset criticality and threat intelligence to improve risk scoring.
Yet, despite these investments in the best tools and staff, and a more business-aligned view of risk findings, you still struggle to keep pace with increasing volumes of findings and threat actor activity. You might have many dozens of tools and vendors, with redundant and time-consuming procurement processes and licensing expenses. As a result, some security leaders at this phase look to consolidate around a subset of strategic vendors in hopes of uncovering new economies of scale.
At the heart of the problem is the siloed nature of security. Data remains trapped in siloed tools, so teams lack an understanding of technical relationships between assets, identities and risks they need to understand how attackers move, and the potential impact to the organization needed to be more effective.
Worth noting: Most organizations fall into either the Defined or Standardized levels of maturity.
Which stage of exposure management maturity best defines your organization? You may be more advanced than you think. Take our exposure management maturity assessment to find out.
Exposure Management Maturity Model Stage 4: Advanced
Advanced characteristics:
- Unified asset and risk data
- Consistent visualization, scoring, workflow and reporting
- Greater economies of scale
To move to the Advanced stage, you need to bring asset and risk data together across siloes and put it to work in more efficient and effective ways. The security industry has made various attempts in recent years to address this challenge.
Cyber asset attack surface management (CAASM) tools looked to unify asset data across vendor tools to achieve a single unified view of assets across the attack surface. Similarly, unified vulnerability management (UVM) solutions have tried to unify risk findings from across tools in a single place. Yet neither solution addresses the full scope of the challenge nor the use cases security teams require.
As a result, we see many organizations trying to build it themselves — exporting asset and risk data from all their tools into a single data lake. The challenge is that unification is only part of the problem. The development required to bring the data into one place and then do more things with it (whether it’s reporting or workflow orchestration) is not a core competency of security teams. And a custom-built solution isn’t cost effective to maintain over time.
This is where exposure management platforms (or exposure assessment platforms) enter the picture.
You can achieve massive efficiency gains across security silos if teams have a consistent way to:
- Visualize aggregated asset and risk data
- Normalize how they measure risk
- Consistently implement workflows
- Simplify communication, risk reporting and compliance
Exposure management platforms collect and normalize asset and risk data across diverse tool sets and vendors, providing a single unified view of the attack surface, and a consistent means to assess and communicate risk posture across the organization.
But unification alone isn’t enough. To scale operations and drive higher value from existing investments in tools and people, we must also understand the technical and business relationships attackers exploit — before breaches get underway.
Exposure Management Maturity Model Stage 5: Optimized
Optimized characteristics:
- Rich technical and business context
- Highly scalable attack path prioritization
- Exposure-centric mobilization and investment
Using AI, exposure management platforms create a robust data fabric of asset, identity and risk relationships, and commonly used MITRE techniques. They map viable attack paths that lead to crown jewel assets, such as critical servers or administrator accounts. These are the same attack paths attackers use to gain access, move laterally and achieve their objectives.
With the mapping in place, the attack paths are prioritized using aggregate scoring that factors in known threat actor activity and tactics, accessibility, exploitability, blast radius and business impact, among other variables. You can instantly focus on attack paths in context of what matters most to the business, including potential impact to revenue, clients or compliance.
Rather than trying to chase and fix every individual risk finding, you can focus on closing specific choke points that have the largest blast radius and potential business impact first, breaking multiple attack paths at once. The result is massively scalable operations and productivity gains, enabled through prioritized focus on exposure.
Ready to begin your exposure management maturity journey?
Every organization sits at a different level of security maturity, but only the Tenable One Exposure Management Platform can accelerate maturity at every stage. By unifying siloed data and providing greater context across your security instrumentation, exposure management helps you move beyond managing findings to understanding and addressing true exposures.
To help you understand where your organization stands on the exposure management Maturity curve, Tenable has developed a free online maturity assessment tool. In less than five minutes, you’ll get a personalized report with recommendations for your organization. View the video summary below:

Learn more
In the next post in this series, we explore case studies of organizations at various levels of maturity and how they accelerated their journey to exposure management value. Read How Exposure Management Helped Three Companies Transform Their Cybersecurity Program now.
- Exposure Management
- Exposure Management Academy


