Cybersecurity Snapshot: Asset Inventories Key for OT Security, CISA Says, as NIST Issues Lightweight Algorithms to Secure IoT Devices

CISA stresses that an asset inventory is the foundation for OT security. Meanwhile, NIST has finalized cryptographic algorithms for resource-constrained devices. The agency is also developing control overlays for AI systems. Plus, a report reveals that security budget growth has slowed to a five-year low due to economic uncertainty. And much more!
Here are five things you need to know for the week ending August 15.
1 - CISA to OT operators: If you can’t see it, you can’t secure it
Struggling to track your operational technology (OT) wares? Check out a new playbook for how to structure, manage and update an inventory of your OT assets.
Published this week, the new guidance from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has a clear message: an OT asset inventory is the bedrock of any OT security architecture.
“An OT asset inventory – an organized, regularly updated list of an organization’s OT systems, hardware, and software – is foundational to designing a modern defensible architecture,” the document reads.
Organizations lacking an OT asset inventory have no visibility into their OT wares and consequently can’t secure them, CISA added in the guidance titled “Foundations for OT Cybersecurity: Asset Inventory Guidance for Owners and Operators.”
The guide, aimed at OT system owners and operators from all critical infrastructure sectors, recommends inventorying all hardware, software and network components, including each asset’s vendor, model, firmware version, physical location and more.
But OT operators shouldn’t stop there.
They also must create a taxonomy, because of the diversity of assets in OT environments, such as legacy systems, specialized devices, sensors and instrumentation – along with their usual variety of proprietary communication protocols.
“Owners and operators need context on a component’s role in monitoring and control of the physical process; this may require owners and operators to physically review and inspect assets and associated process areas,” the document reads.
The benefits of classifying OT assets by function and importance are significant:
- Prioritize what matters most.
- Sharpen risk identification and vulnerability management.
- Boost incident response.
Steps To Build An OT Asset Taxonomy

(Source: CISA)
The document, which CISA created in collaboration with multiple U.S. and international government agencies, also details how to continuously maintain and improve OT asset inventories and taxonomies.
The guidance’s ultimate goal is to help critical infrastructure organizations shift from a reactive to a proactive security posture via full asset visibility and thus attain a more resilient and secure OT environment.
“As cyber threats continue to evolve, CISA through this guidance provides deeper visibility into OT assets as a critical first step in reducing risk and ensuring operational resilience,” CISA Acting Director Madhu Gottumukkala said in a statement.
For more information about OT security, check out these Tenable resources:
- “Mind the Gap: A Roadmap to IT/OT Alignment” (white paper)
- “Unlock Advanced IoT Visibility in your OT Environment Security” (on-demand webinar)
- “Blackbox to blueprint: The security leader’s guidebook to managing OT and IT risk” (white paper)
- “Fortifying Your OT Environment: Vulnerability and Risk Mitigation Strategies” (on-demand webinar)
- “Identity Security Is the Missing Link To Combatting Advanced OT Threats”
2 - New cryptographic algos issued to protect IoT devices
Here’s one for teams tasked with securing IoT devices.
The National Institute of Standards and Technology (NIST) has finalized a new standard for lightweight cryptography to protect electronic devices with limited computational resources.
“We encourage the use of this new lightweight cryptography standard wherever resource constraints have hindered the adoption of cryptography,” NIST computer scientist Kerry McKay, who co-led the project, said in a statement this week.
The standard was built for protecting the billions of devices that lack the power for conventional encryption. Think smart appliances, medical implants and industrial sensors that don't have the processing muscle for heavy security.

(Credit: Image generated by Tenable using Google Gemini)
Detailed in NIST Special Publication 800-232, the standard is built around the Ascon family of cryptographic algorithms and includes four specific algorithms designed for different security needs.
- ASCON-128 AEAD: Encrypts data and proves it hasn't been tampered with.
- ASCON-Hash 256: Creates a digital fingerprint to detect alterations.
- ASCON-XOF 128 and ASCON-CXOF 128: Allow developers to fine-tune security to match devices’ capabilities.
This new standard is designed for straightforward implementation and offers better protection against "side-channel attacks," where adversaries analyze a device's power consumption or timing to glean information.
NIST has indicated that this is a foundational standard, with plans to add more features in the future based on community feedback. The goal is to provide a robust and adaptable security solution that can evolve as technology and cyber threats advance.
“There are additional functionalities people have requested that we might add down the road, such as a dedicated message authentication code,” McKay said.
For more information about IoT security:
- “How to Remediate Risk to Critical OT/IoT Systems without Disrupting Operations” (Tenable)
- “What is IoT security?” (TechTarget)
- “How to Unlock Advanced IoT Visibility for Cyber-Physical Systems” (Tenable)
- “Disaster Awaits if We Don’t Secure IoT Now” (IEEE)
- “Top 15 IoT security threats and risks to prioritize” (TechTarget)
3 - Report: Economic uncertainty impacts security budgets
Just as cyber threats get worse and security teams get more responsibility, CISOs' budgets are being squeezed due to macroeconomic headwinds.
That’s a key takeaway from the "2025 Security Budget Benchmark Report" published by IANS Research and Artico Search.
"Once again, we find that security budgets are not immune to macro conditions," Steve Martano, IANS Faculty and Partner at Artico Search, said in a statement.
"Despite most companies identifying cyber as a top five business risk, most CISOs are not receiving budget increases commensurate with the increase in security program scope,” he added.
Specifically, year-over-year average growth in security budgets has fallen to a five-year low of 4%, a steep decline from the 8% growth seen in 2024, as companies become more cautious with their spending due to economic unpredictability.
The report, based on a survey of 587 CISOs, blames global market volatility, including geopolitical tensions, tariff uncertainty and fluctuating economic indicators.
Other key findings include:
- Budgets aren't keeping pace: Security's slice of the total IT budget fell from 11.9% to 10.9%.
- Hiring has slowed: Security staffing growth is down to 7%, the lowest in four years.
- Teams are stretched thin: Only 11% of CISOs say their teams are adequately staffed.
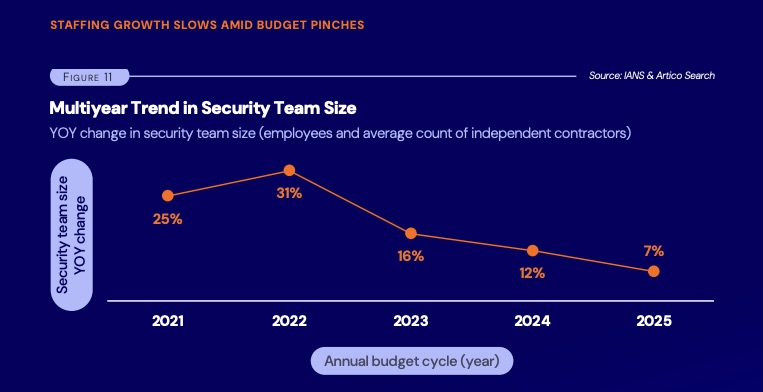
(Source: "2025 Security Budget Benchmark Report" from IANS Research and Artico Search, August 2025)
So what should CISOs do? The report offers three recommendations:
- Align every project with clear business goals.
- Prioritize ruthlessly to protect the organization’s crown jewels.
- Be realistic with your budget asks, and prove the ROI.
For more information about cybersecurity budget strategies:
- “Blown the cybersecurity budget? Here are 7 ways cyber pros can save money” (CSO)
- “Cybersecurity budget justification: A guide for CISOs” (TechTarget)
- “5 steps to prioritize cybersecurity in your 2025 budget” (CFO)
- “How to create an enterprise cloud security budget” (TechTarget)
- “2025 will be the year of CISO fiscal accountability” (VentureBeat)
4 - NIST wants your help to secure AI
NIST is building a set of "control overlays" to help organizations lock down their AI systems, and it’s looking for feedback about the initiative.
NIST outlined the project this week in the document “NIST SP 800-53 Control Overlays for Securing AI Systems Concept Paper,” and also launched a Slack channel for collaborators.
“The control overlays are an implementation-focused series of guidelines that address use cases involving different types of AI systems and specific AI system components,” reads the Control Overlays for Securing AI Systems (COSAiS) project home page.

(Credit: Image generated by Tenable using Google Gemini)
The goal of the overlays is to protect the “confidentiality, integrity, and availability” of the users and data for these proposed use cases:
- Using generative AI to create content
- Fine-tuning predictive AI to make better decisions
- Deploying AI agents to automate tasks
- Building secure AI systems from the ground up
The ultimate goal is to offer organizations a “library of overlays” that they can use to reduce the risks of their AI use and development.
NIST is putting out the call for feedback on these use cases. It wants to know if they reflect how AI is really being adopted and which ones to prioritize. NIST is also open to adding use cases to the project.
NIST foresees releasing a draft of the first use case in early 2026.
For more information about AI security, check out these Tenable resources:
- “The AI Security Dilemma: Navigating the High-Stakes World of Cloud AI” (blog)
- “Tenable Cloud AI Risk Report 2025” (research report)
- “Introducing Tenable AI Exposure: Stop Guessing, Start Securing Your AI Attack Surface” (blog)
- “Mitigating AI-Related Security Risks: Insights and Strategies with Tenable AI Aware” (on-demand webinar)
- “Expert Advice for Boosting AI Security” (blog)
5 - FBI: Beware of fake law firms offering crypto fund recovery
Individuals and organizations that have lost money in crypto scams are being targeted by cyber crooks posing as lawyers.
The warning comes courtesy of the FBI's Internet Crime Complaint Center (IC3), which issued a public service announcement this week, updating a similar one it published last year.
The cyber scammers are now combining multiple exploitation tactics, making their schemes more sophisticated and harder to detect.
“Contact with scammers impersonating law firms continue to pose many risks, including the theft of personal data and funds from unsuspecting victims to the reputational harm of actual lawyers being impersonated,” reads the PSA.

(Credit: Image generated by Tenable using Google Gemini)
New information in this updated advisory includes red-flag indicators and due-diligence recommendations.
Red-flag indicators include:
- Scammers using the names and letterhead of real lawyers
- Claims of affiliation with government agencies
- Demands for payment in crypto or prepaid gift cards
- Detailed knowledge of the scams victims suffered, such as exact amounts stolen and wire transfer service used
Due-diligence recommendations include:
- Trust no one, especially alleged law firms that contact you out of the blue.
- Demand proof. Ask for a law license and notarized ID.
- Verify employment if someone claims to work for the government. Call the agency’s local office yourself.
If you believe you have been targeted, file a report with the IC3 at www.ic3.gov.
For more information about cryptocurrency cyber scams:
- “What To Know About Cryptocurrency and Scams” (FTC)
- “Cryptocurrency Investment Fraud” (FBI)
- “Cryptocurrency Scams: How to Spot, Report, and Avoid Them” (Investopedia)
- Cloud
- Cybersecurity Snapshot
- Endpoint security
- Exposure Response
- Federal
- Government
- Malware
- NIST
- OT Security
- Risk-based Vulnerability Management

