Cybersecurity Snapshot: CIS Guide Outlines How To Attain an Affordable Cyber Hygiene Foundation

The Center for Internet Security unpacks how to establish foundational cyber hygiene at a reasonable cost. Plus, the Cyber Safety Review Board issues urgent security recommendations on its Lapsus$ report – and announces it’ll next delve into cloud security. Moreover, are humans or AI better at crafting phishing emails? Check out what a study found. And much more!
Dive into six things that are top of mind for the week ending August 18.
1 – CIS: Yes, Virginia, you can have solid cyber hygiene without breaking the bank
When tasked with beefing up their cybersecurity foundation, organizations often struggle with basic questions. What steps should we take first? Which products will we need? How much money should we plan to spend?
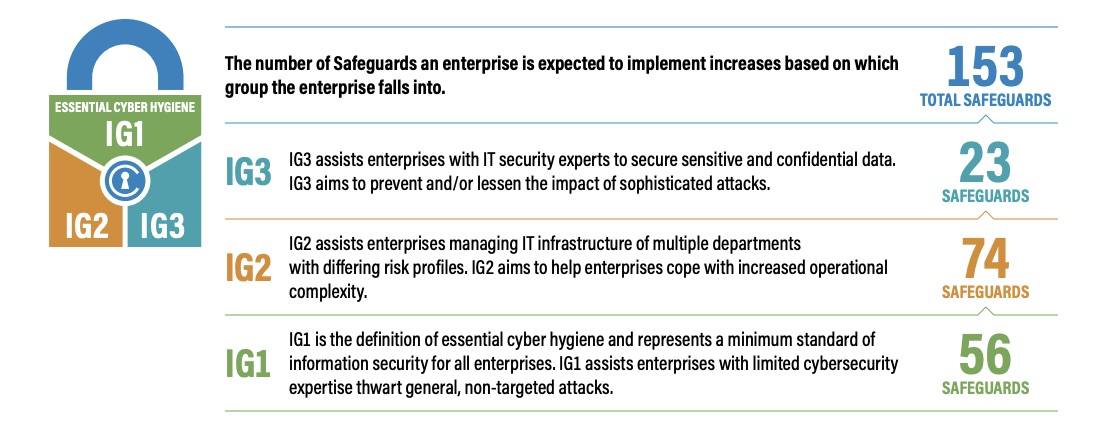
To help with such a scenario, the Center for Internet Security released a guide this week titled “The Cost of Cyber Defense: CIS Controls Implementation Group 1 (IG1).” The 36-page document outlines how organizations can adopt the CIS’ first tier of safeguards – known as IG1 – contained within the 18 CIS Controls.
Specifically, there are 56 safeguards in IG1, and this new guide organizes these actions into 10 categories: asset management; data management; secure configurations; account and access control management; vulnerability management; log management; malware defense; data recovery; security training; and incident response.

The guide is divided into five sections:
- Methodology
- Protections to start with
- IG1 enterprise profiles
- Tooling
- Costs
“The safeguards in IG1 can be implemented for a relatively low cost and are a foundational and achievable set of security actions for even the smallest of enterprises,” the guide reads. “Additionally, enterprises can implement IG1 and defend against a wide array of threats with a relatively small number of tools.”
CIS has two other Implementation Groups – IG2 and IG3 – with more advanced safeguards, but those aren’t discussed in this particular guide.
(Source: Center for Internet Security)
To get more details, check out:
- the CIS blog “Essential Cyber Hygiene: Making Cyber Defense Cost Effective”
- the full guide “The Cost of Cyber Defense: CIS Controls Implementation Group 1 (IG1)”
- a page about the CIS Implementation Group 1 (IG1)
- a page about all three CIS Implementation Groups: IG1, IG2 and IG3
- the home page for the CIS Critical Security Controls Version 8
2 – Prompted by Exchange Online breach, CSRB tackles cloud security
The U.S. government will probe the recent Microsoft Exchange Online breach in which hackers backed by the Chinese government swiped emails from U.S. government officials’ inboxes.
The Department of Homeland Security’s Cyber Safety Review Board (CSRB) will carry out the review, which will also focus more broadly on the security of cloud computing environments and their identity and authentication infrastructure.

“Organizations of all kinds are increasingly reliant on cloud computing to deliver services to the American people, which makes it imperative that we understand the vulnerabilities of that technology,” Secretary of Homeland Security Alejandro N. Mayorkas said in a statement.
When completed, the review will offer recommendations aimed at arming cloud computing customers and providers with cybersecurity best practices. Previously, the CSRB has issued reports on the Log4j vulnerabilities and on the Lapsus$ ransomware gang, which we cover in our next item – so read on!
To get more details, check out the DHS announcement, along with coverage from CRN, Reuters, TechCrunch and The Register.
3 – CSRB Lapsus$ report calls for stronger MFA
After a months-long deep dive into Lapsus$, the CSRB has concluded that the notorious ransomware gang used a playbook of well-known, run-of-the-mill techniques that other cyber criminals use and will continue to employ.
“If richly resourced cybersecurity programs were so easily breached by a loosely organized threat actor group, which included several juveniles, how can organizations expect their programs to perform against well-resourced cybercrime syndicates and nation-state actors?,” reads the “Review Of The Attacks Associated with Lapsus$ And Related Threat Groups” report.
Given this troubling finding, the 59-page document offers a slate of recommendations for businesses, the government and telecom and tech vendors, including:
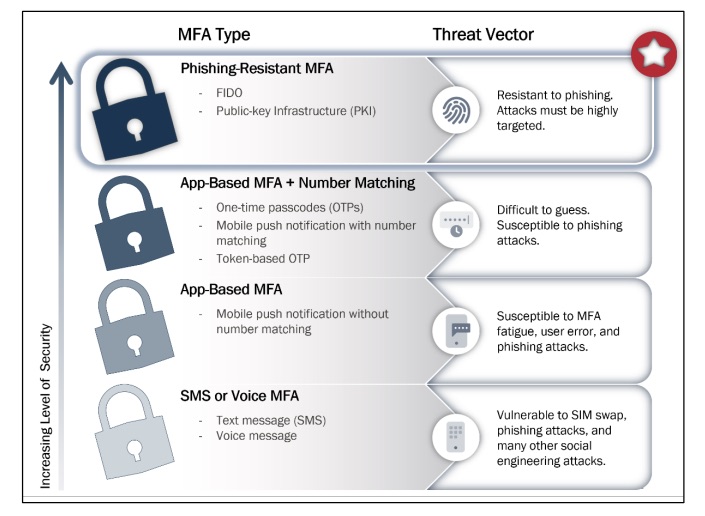
- Voice- and SMS-based multi-factor authentication should be replaced by passwordless methods. Software and device manufacturers, as well as the U.S. government, should actively try to facilitate this transition, and end-user organizations should be willing to adopt these new phishing-resistant options.
MFA Methods and Common Exploitations
(Source: CSRB’s “Review Of The Attacks Associated with Lapsus$ And Related Threat Groups” report, August 2023)
- Because mobile devices are widely used for authentication, telecom providers should take steps to make their devices more secure through technological, process and oversight measures.
- End-user organizations should be ready to face cyberattacks through planning and investing in prevention, detection, response and recovery capabilities. They also should incorporate cybersecurity requirements into their contracts with tech providers.
To get more details, read the DHS announcement and the full report.
4 – Study: Expert phishers trounce GPT-4 – for now
Much has been said about how attackers are using generative AI chatbots like ChatGPT to quickly automate the creation of effective and polished phishing emails. Well, a new research study concluded that skilled scammers still outperform the AI robots when it comes to phishing attacks – with one caveat. When advanced manual phishing rules are combined with generative AI, the success rate edges all other methods.
According to the paper “Devising and Detecting Phishing: Large Language Models vs. Smaller Human Models,” the researchers randomly selected 112 people for the study and sent them four types of phishing emails.
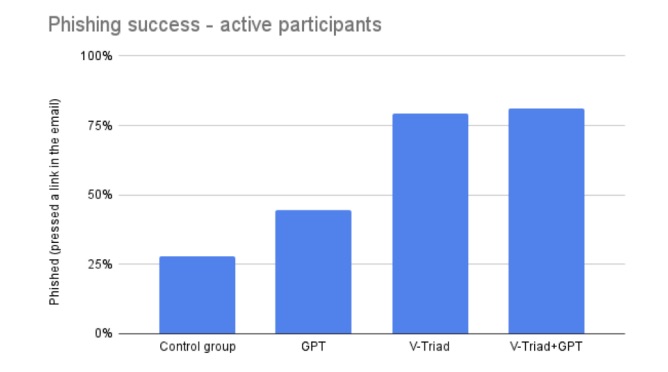
These were the results, based on the 77 people who fully participated in the survey:
- Manually-written generic emails had a click-through rate (CTR) of 19%-28%
- Emails generated by OpenAI’s GPT-4 had a CTR of 30%-44%
- Emails written manually using the V-Triad advanced set of rules got a CTR of 69%-79%
- Emails crafted using both the V-Triad rules and ChatGPT nabbed a CTR of 43%-81%
(Source: “Devising and Detecting Phishing: Large Language Models vs. Smaller Human Models” research paper, August 2023)
The study, authored by Fredrik Heiding, Bruce Schneier, Arun Vishwanath and Jeremy Bernstein, also probed the ability of GPT-4 and three other large language models to detect phishing emails. The result? The LLMs proved to be “surprisingly good” at this task in some cases, besting human detection at times, but overall fell short compared with humans.
For more information about the use of generative AI for phishing creation and detection:
- “7 guidelines for identifying and mitigating AI-enabled phishing campaigns” (CSO Online)
- “How AI Protects (and Attacks) Your Inbox” (Wired)
- “A.I. is helping hackers make better phishing emails” (CNBC)
- “AI vs AI: Next front in phishing wars” (TechRepublic)
- “How to Spot a Job Offer Scam Written by AI” (Lifehacker)
5 – CISA zooms in on securing remote monitoring software
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has published a roadmap for securing remote monitoring and management (RMM) software, whose exploitation the agency views as “a systemic risk” to all organizations.
Working with CISA’s Joint Cyber Defense Collaborative (JCDC), a group of public- and private-sector collaborators participated in the creation of the “Remote Monitoring and Management Cyber Defense Plan,” which was released this week.

The plan outlines actions to be taken in order to help RMM vendors, managed service providers, SMBs, and critical infrastructure operators make this software more secure and resilient.
It specifically highlights these four areas:
- Sharing cyberthreat and vulnerability information
- Creating mechanisms for the RMM community to mature its security efforts long-term
- Developing and enhancing end-user education and cybersecurity guidance
- Amplifying security advisories and alerts within the RMM ecosystem
To get more details, check out:
- CISA’s announcement
- A summary of the plan
- The “Remote Monitoring and Management Cyber Defense Plan”
- A separate CISA guide titled “Guide to Securing Remote Access Software”
6 – Study: Cloud-native apps go mainstream
To sidestep the challenge of digitally transforming operations using legacy technology, organizations are increasingly adopting a cloud-first strategy, a trend that now finds cloud-native applications and methodologies becoming the new normal.
That’s according to Enterprise Strategy Group’s “Distributed Cloud Series: The Mainstreaming of Cloud-native Apps and Methodologies” report, which surveyed 378 IT, DevOps and application development pros in North America.

“This approach involves prioritizing cloud-based, developer-friendly solutions over traditional on-premises software and infrastructure to increase agility,” reads an ESG infographic about the report.
Of course, this enthusiastic embrace of cloud-native apps and methodologies has major implications for security and compliance teams, which must be in sync with these cloud shifts to properly protect their organizations’ digital assets and data.
Here are some of the findings from the survey, whose respondents evaluate, purchase, build and manage application infrastructure in their organizations:
- 94% of organizations use two or more cloud infrastructure service providers
- 64% develop cloud-native apps based on microservices architectures
- 63% release new code to production every day
- 91% will bump up tech spending for cloud-native app development in the next 12-18 months
To get more details, check out:
- the report’s landing page
- the infographic
For more information about cloud security, check out these Tenable resources:
- “Unpacking the Shared Responsibility Model for Cloud Security” (blog)
- “Avoiding the Security Potluck: Good Governance Helps You from Code to Cloud” (blog)
- “Building a Resilient Container Security Strategy: The Power of Prevention” (ebook)
- “The Challenges of Multi-Cloud Compliance” (blog)
VIDEO
Tenable Cloud Security Coffee Break Episode 15: Container Security
- Cloud
- Cybersecurity Snapshot
- Exposure Management
- Federal
- Vulnerability Management


