Cybersecurity Snapshot: 6 Things That Matter Right Now

Topics that are top of mind for the week ending July 29 | Boost your security awareness program. Why fire drills hurt security teams. A quick temperature check on attack surface management. Protecting smart factories from cyberattacks. And much more!
1. Struggling to fill cybersecurity jobs? Focus on folks starting out.
Cybersecurity hiring managers face intense competition for talent amid chronic staffing shortages. A new report from the (ISC2) offers hope, saying you can find strong candidates among the entry-level and junior-level crowd – those with under a year of experience, and with one to three years, respectively.
The report, based on a poll of 1,250 hiring managers, found that the cost to train these employees is reasonable and that they get up to speed fairly quickly. Even better, they contribute fresh perspectives, ideas, and skills in new technologies.
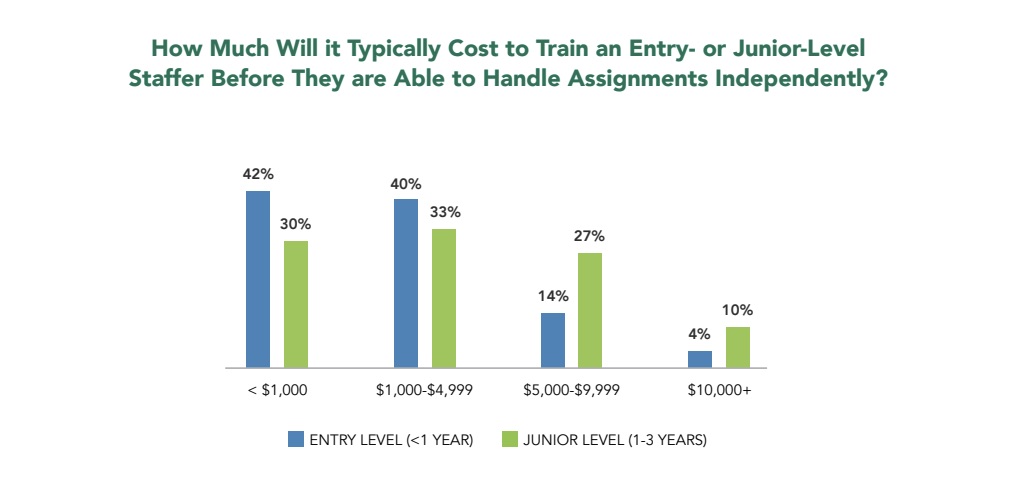
(Source: “Best Practices for Hiring and Developing Entry-Level and Junior-Level Cybersecurity Practitioners” report from (ISC2)
Recommendations from the (ISC2) include:
- Don’t limit your search to the IT field. Look for people who are good at project management, customer service, problem solving, analytical thinking, and teamwork.
- Get the job descriptions right. Partner with human resources to explain the job realistically and establish clear expectations.
- Assign the right tasks to these new hires. Craft a workload that’s appropriate to their level of experience and that allows them to learn and grow on the job.
- Offer them professional development opportunities. Provide mentorship programs, facilitate attainment of certifications and offer training.
To get all the details, read the full 21-page report “Best Practices for Hiring and Developing Entry- and Junior-Level Cybersecurity Practitioners.”
2. Here’s the top malware for June
The Center for Internet Security (CIS) recently released its top 10 list of malicious software for June, its most recent ranking. Here it is, in order of prevalence:
- Shlayer, a downloader and dropper for MacOS malware
- CoinMiner, a cryptocurrency miner family
- QakBot, a multifunctional banking trojan
- ZeuS, a modular banking trojan
- NanoCore, a remote access trojan (RAT)
- GravityRAT
- Gh0st, a RAT
- Agent Tesla, a RAT
- Mirai, a malware botnet
- RedLine, an infostealer
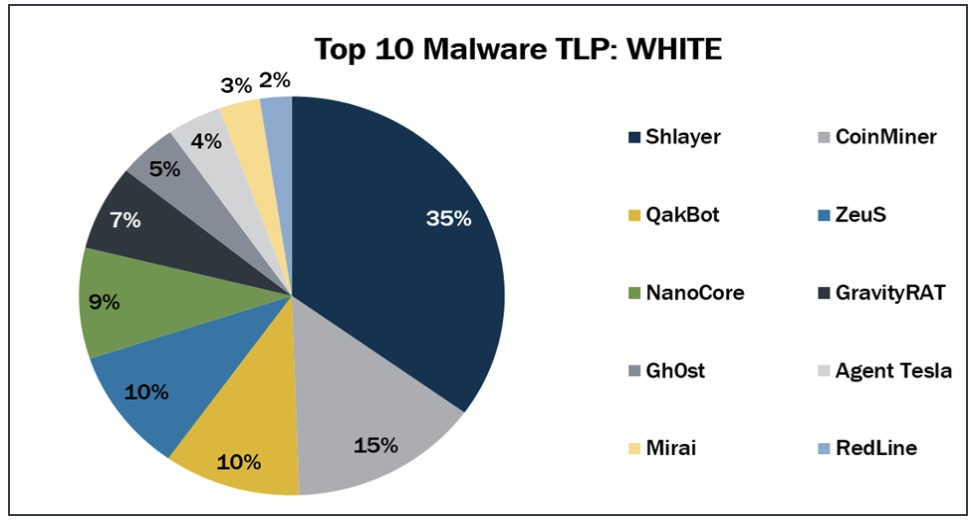
(Source: The Center for Internet Security)
To get all the details, context and indicators of compromise for each malware, read the CIS report.
3. Analyst to CISOs: End “fire drill” culture
It’s a chronic problem among many security teams: Spending most of their time responding to emergencies while devoting little time to strategic plans. Well, CISOs must extinguish “fire drill” mode once and for all, a cybersecurity analyst warns.
Writing in CSO Magazine, Jon Oltsik from Enterprise Strategy Group admits he, too, had become “numb” to this perennial issue, until he pondered its dangerous implications, including:
- Chaos reigns, causing stress, increasing complexity and decreasing efficiency.
- Cutting corners inevitably becomes standard procedure.
- Tribal knowledge, not proven processes, drive incident responses.
- There’s poor preparation for newer types of attacks.
The good news? The solution isn’t rocket science. Common sense steps like improving security hygiene, segmenting networks and automating processes will go a long way.
For more information about this topic:
- “What Is Proactive Cybersecurity?” (SecurityIntelligence)
- “Build a proactive cybersecurity approach that delivers” (TechTarget)
- “12 steps to building a top-notch vulnerability management program” (CSO Magazine)
- “Vulnerability management mistakes CISOs still make” (CSO Magazine)
4. Smart factories: A big target for hackers
Digitized smart factories are the future of manufacturing but their broad exposure to the internet makes them an increasingly popular attack target. Their security teams must up their game.
A recent Capgemini Research poll of 950 organizations’ smart factory cybersecurity found they are in general “inadequately prepared in terms of awareness, governance, protection, detection and resilience.” Yikes.

In fact, respondents say, it’s common for cybersecurity analysts to feel overwhelmed by the myriad operational technology (OT) and Industrial Internet of Things (IIOT) devices they must track.
So how can these teams shore up their smart factories’ cybersecurity? Report recommendations include:
- Perform an initial assessment, creating an inventory and tracking mechanism for all connected devices.
- Build organization-wide awareness of cyberthreats, from top management to staff.
- Identify clear risk ownership for cyberattacks.
- Establish a governance structure that adheres to global protocols and regulations.
- Tailor practices and frameworks for the smart-factory environment.
To get all the details, download the full 52-page report “Smart & Secure: Why smart factories need to prioritize cybersecurity” and view the accompanying infographic.
For more information about this topic:
- “Arming smart factories with the right tools to keep threats at bay” (The Manufacturer)
- “Guide to Operational Technology (OT) Security” (NIST)
- “Operational Technology Cybersecurity for Energy Systems” (U.S. Energy Department)
- “IT-OT Convergence: Managing the Cybersecurity Risks” (ISA Global Cybersecurity Alliance)
- “Identifying blind spots: OT infrastructure vulnerability” (Technology Decisions)
5. A reality check on attack surface management
Check out these insights about attack surface management – the continuous discovery and identification of internet-facing assets that could be targeted by attackers – from attendees polled informally at a recent Tenable webinar.
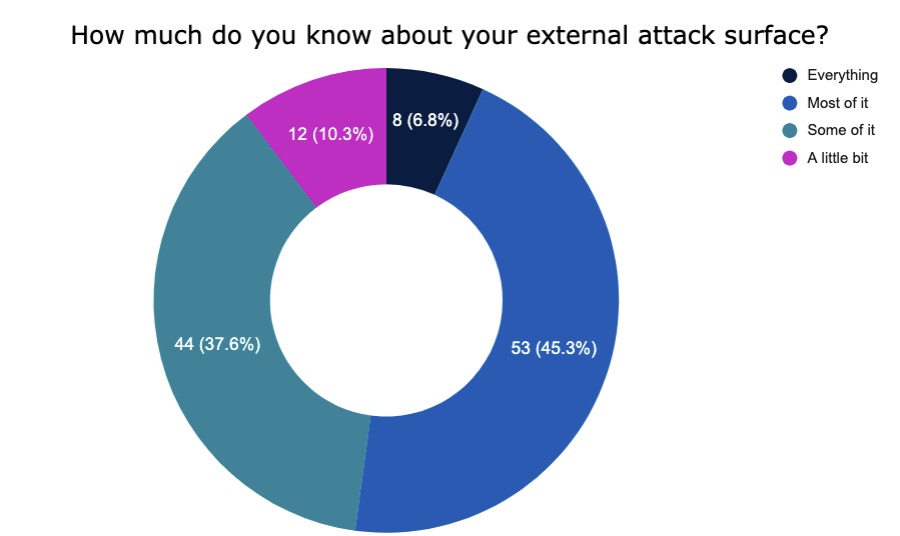
(117 respondents polled by Tenable in July 2022)
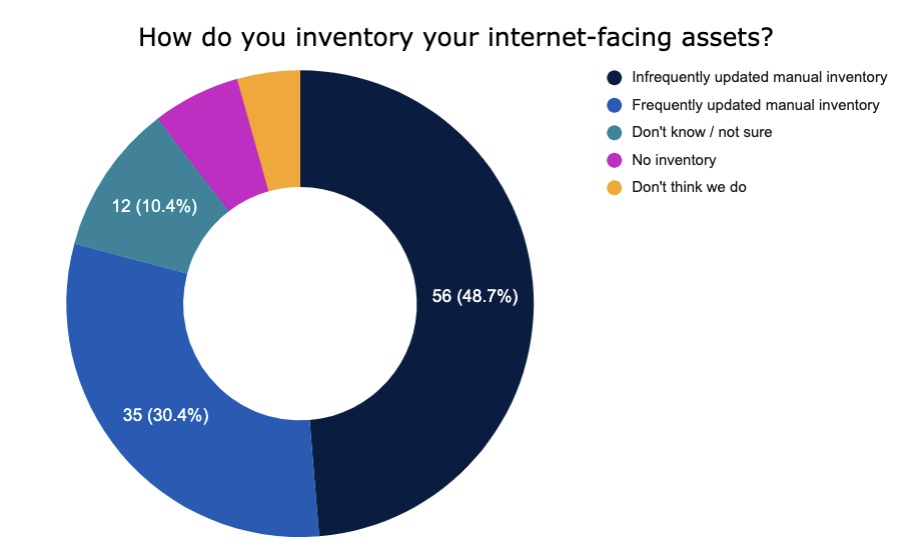
(115 respondents polled by Tenable in July 2022)
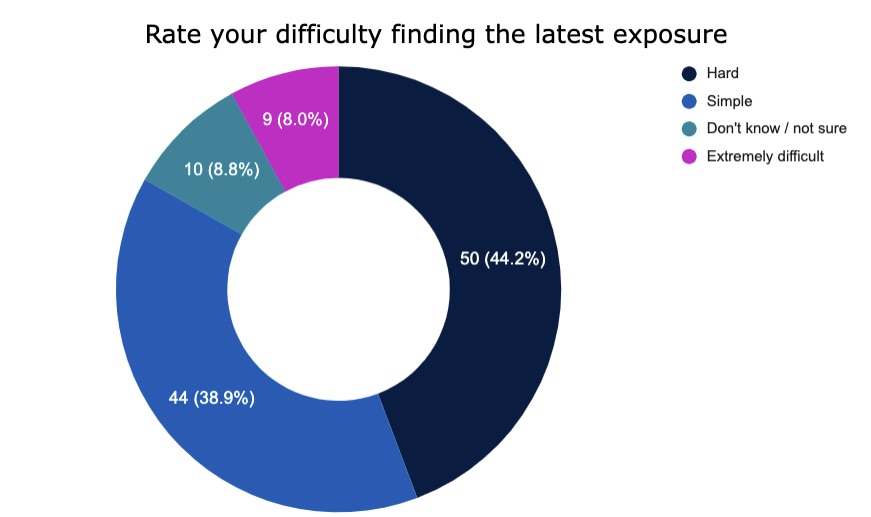
(113 respondents polled by Tenable in July 2022)
For more information about attack surface management, check out these Tenable blogs:
- “High-Fidelity Attack Surface Mapping”
- “An Introduction to ‘Scan Everything’”
- “The Right Way to Do Attack Surface Mapping”
- “False Negatives in Attack Surface Mapping”
6. Your weakest link? Hint: It’s not tech
And, finally, here’s a hard truth: The biggest threat to a company’s cybersecurity is – drumroll! – its staff. Yep, it’s the employees, not the technology. And that means one thing: You need a strong security awareness program.
That’s the word from this year’s Security Awareness Report from SANS Institute. Here are some takeaways from the report, which polled 1,000-plus pros involved in security awareness programs:
- To succeed, you need leadership support; enough staff (about 10% of the overall security team); and frequent employee security training (ideally monthly.)
- Talk to leadership in terms of risk, not just about compliance requirements, explaining why – not what – you’re doing, and how this yields business benefits.
- Closely collaborate with the larger security team, and partner with other teams, like communications and human resources.
- Create a sense of urgency, documenting the importance of security awareness for reducing employee-caused incidents.
- Have a metrics framework that tracks the program’s impact on the organization, and submit regular reports to leadership.
- Seek to change not just people’s security behaviors, but also attitudes and beliefs.
For more information read the SANS Institute press release and download the full 17-page report.
More resources about building security awareness programs:
- “What is security awareness training?” (TechTarget article)
- “Building a Cybersecurity Awareness Program” (Carnegie Mellon University study)
- “Security Awareness Training: 6 Important Training Practices” (EC-Council article)
- “How to Build a Strong Security Awareness Program for Your Employees” (EC-Council video)
- “CIS Control 17: Implement a Security Awareness and Training Program” (Tenable document)
- Cybersecurity Snapshot
