Cybersecurity Snapshot: 6 Things That Matter Right Now

Topics that are top of mind for the week ending Aug. 5 | Don’t take your eye off the Log4j ball. The dangers of unsupported software. Why low MFA adoption is everyone’s problem. Preventing ransomware attacks. And much more!
1. Log4j: It’s a marathon race not a sprint
Like an insufferable houseguest who overstays his welcome, the cataclysmic Log4j vulnerability will be around for a long time – possibly as much as a decade after its earth-shaking discovery in December of last year.
That’s the bad news the Cybersecurity and Infrastructure Security Agency’s Cyber Safety Review Board delivered in a recent report. So let’s cut straight to CISA’s recommendations for staying safe, which include:
- Continue to address Log4j risks through persistent, long-term vigilance, so that you can monitor, discover and upgrade vulnerable software and prevent reintroduction of vulnerable Log4j versions.
- Drive best practices for security hygiene, such as automated vulnerability management, asset inventorying and vulnerability mitigation, as well as secure software development practices.
- Build a better software ecosystem that yields software that’s secure by design, which can be achieved by:
- encouraging open source developers to participate in community-based security initiatives
- training developers in secure software development
- improving the capabilities and adoption of tools for creating software bills of materials (SBOMs)
For more Log4j resources, check out:
- Tenable’s main Log4j resource page
- “DHS Review Board Deems Log4j an 'Endemic' Cyber Threat” (DarkReading)
- “CISA releases IOCs for attacks exploiting Log4Shell in VMware” (CSO Magazine)
- “How to address the ongoing risk of Log4j and prepare for the future” (Help Net Security)
- “The Impact Of Assessing And Addressing Log4j Installations Proactively” (Tenable blog)
- “Apache Log4j Vulnerability Guidance” (CISA)
2. SMBs slow on the MFA uptake
There’s a multifactor authentication (MFA) problem among small and mid-sized businesses (SMBs) – namely, a troubling lack of awareness and use of this security method, which puts them, their customers and their partners at risk.
A survey by the Cyber Readiness Institute of about 1,400 SMBs in eight countries found, among other things, that:
- 55% of respondents aren’t very aware of MFA and its benefits
- 54% don’t implement MFA for their business
- Only 13% require the use of MFA
If you’re reading this and thinking this isn’t your problem because your business is hip to MFA, think again. How many SMBs are on your trusted third-party vendor and partner list, and have some access to your systems and data? Are they all using MFA?
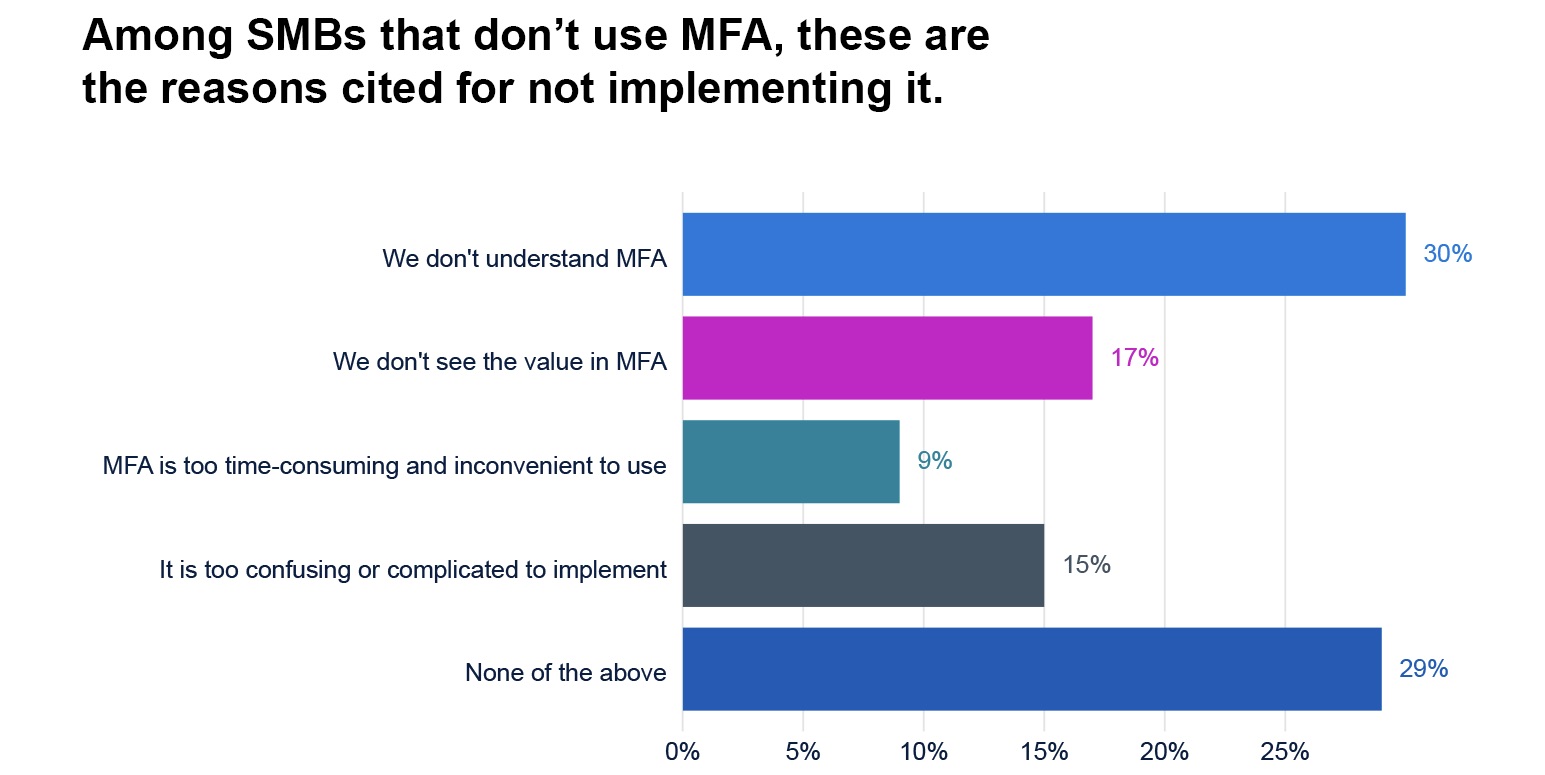
In a companion guide about MFA, the non-profit group includes these recommendations:
- Every employee should use MFA for business-operations services, such as email, accounting and HR, across all of their devices.
- When choosing an MFA tool, pick one that’s easy to use, can be used in the office or remotely, includes employee training and offers around-the-clock support.
- Prioritize systems and data to be protected.
- Create awareness about MFA’s importance among employees.
More information:
- MFA Guide (U.S. Cybersecurity & Infrastructure Security Agency - CISA)
- “Focus on the Fundamentals: 6 Steps to Defend Against Ransomware” (Tenable blog)
- “What is multifactor authentication and how does it work?” (TechTarget)
- “Adopting Multi-Factor Authentication” (Identity Management Institute)
- “A Refresher on Multifactor Authentication and Best Practices” (Governing)
3. Do you own any of these newly unsupported software products?
When vendors stop supporting a software version or product, it immediately becomes a security risk. In its most recent roundup for recently unsupported software, the Center for Internet Security (CIS) reminds organizations that continuing to use these software assets – operating systems, applications, firmware and the like – puts them at risk in various ways, including:
- You no longer get updates and patches for it, even if new vulnerabilities are disclosed.
- You may be subject to regulatory compliance violations.
- You may experience malfunctions and incur higher support costs.
More information about these risks:
- U.K. National Cyber Security Centre’s guidance on obsolete products
- Guidance on outdated components from the Open Web Application Security Project (OWASP)
- “Unsupported IoT Devices Are Cyber-Trouble Waiting To Happen” (ECommerce Times)
- Tenable document about unsupported software
- “Agencies Work Diligently to Upgrade Legacy Systems” (FedTech)
- MITRE document on assigning CVE IDs to End-of-Life products
4. Time to prep for the quantum computing threat
They don’t exist yet, but quantum computers that can break existing cryptographic algorithms will be developed. When? No one knows exactly. (The Cloud Security Alliance says in 2030.) But this much is clear: This will put digital systems worldwide at risk, creating a potential data-privacy catastrophe. Efforts to address this problem have been underway for years.
For example, the U.S. government recently selected the first four “quantum resistant” cryptographic algorithms resulting from a competition launched by the National Institute of Standards and Technology (NIST) in 2016. Four other algorithms are under consideration. The final standardized algorithms aren’t expected before 2024.

While all this plays out, the government has outlined a roadmap with a list of tasks security teams can start to do today – yep, as in “now” – to prepare for the arrival of “post quantum cryptography,” including:
- Create an inventory of systems and applications that use public-key cryptography.
- Create an inventory of the most sensitive and critical data to be secured long-term.
- Prioritize systems for transition, by asking questions like:
- Is this system a “high value” asset for the organization?
- What is this system protecting?
- What other systems does it communicate with?
- Does this system share information externally and to what extent?
- Does it support critical infrastructure?
More U.S. government and industry resources:
- “Post-Quantum Cryptography: the Good, the Bad, and the Powerful” (NIST video)
- “Getting Ready for Post-Quantum Cryptography” (NIST white paper)
- White House Memorandum on Quantum Computing
- “Quantum Computing and Post-Quantum Cryptography” (National Security Agency FAQ)
- Cloud Security Alliance’s Quantum-safe Working Group
Articles and commentary about this topic:
- “Inside NIST's 4 Crypto Algorithms for a Post-Quantum World” (DarkReading)
- “Now Is the Time to Plan for Post-Quantum Cryptography” (DarkReading)
- “Four new defenses against quantum codebreakers” (Politico)
- “NIST PQ: ‘Lattice’ Pick A Winner” (Forrester blog)
- “Senators look to thwart future quantum hacks” (FCW)
5. Knowledge is key for defeating ransomware
Ransomware remains a critical problem globally, and understanding this threat is key for successful prevention. That’s why it’s a big focus for Tenable, and for our Security Response Team (SRT) in particular.

Recent resources from SRT include the white paper “The Ransomware Ecosystem,” as well as blogs about the LAPSUS$ extortion group and about the different ecosystem players and their motivations. You can also check out interviews with SRT research engineers on DarkReading, Enterprise Security Tech, KBI Media and Manufacturing.net.
Tenable recommendations to prevent ransomware attacks include:
- Use MFA for all accounts within your organization
- Require the use of strong passwords for accounts
- Continuously audit permissions for user accounts
- Identify and patch vulnerable assets in your network in a timely fashion
- Review and harden Remote Desktop Protocol
- Strengthen Active Directory security
6. Vulnerabilities, incidents and trends to keep your eye on
- Tenable Research recently discovered that the Jumpstart environments for Microsoft’s Azure Arc do not properly use logging utilities, leading to potentially sensitive information being logged in plaintext. Microsoft has patched the issue.
- Got info on North Korean hackers? The U.S. is offering a $10 million reward.
- Patch the Atlassian Confluence vulnerability ASAP!
- Oracle addressed 188 CVEs with 349 patches, including 66 critical updates.
- VMware patched serious vulnerabilities across multiple products including VMware Workspace ONE Access.
- Microsoft is blocking macros by default in Office.
- The cost of a data breach? For T-Mobile, it’s hundreds of millions.
- The personal data of 1.9 million patients was exposed in a healthcare breach.
- Cybersecurity Snapshot
- NIST
- Public Policy
- Research Reports
- Threat Management
- Vulnerability Management
