CVE-2018-13379, CVE-2019-5591, CVE-2020-12812: Fortinet Vulnerabilities Targeted by APT Actors

Threat actors and ransomware groups are actively targeting three legacy Fortinet vulnerabilities.
Background
On April 2, the Federal Bureau of Investigation (FBI) along with the Cybersecurity and Infrastructure Security Agency (CISA) issued a joint cybersecurity advisory regarding activity involving advanced persistent threat (APT) actors.
In March 2021, the FBI and CISA observed APT actors scanning and enumerating publicly accessible Fortinet systems over ports 4443, 8443 and 10443. The agencies believe these APT actors are gathering a list of vulnerable systems in both the public and private sectors in preparation for future attacks. The advisory highlights three Fortinet vulnerabilities.
| CVE | Vulnerability Type | CVSSv3 | VPR* |
|---|---|---|---|
| CVE-2018-13379 | Path Traversal/Arbitrary File Read (FortiOS) | 9.8 | 9.8 |
| CVE-2019-5591 | Default Configuration (FortiOS) | 7.5 | 7.3 |
| CVE-2020-12812 | Improper Authentication (FortiOS) | 9.8 | 9.6 |
*Please note: Tenable’s Vulnerability Priority Rating (VPR) scores are calculated nightly. This blog post was published on April 8 and reflects VPR at that time.
All three vulnerabilities reside within Fortinet’s FortiOS, the operating system that underpins Fortinet’s devices.
Analysis
CVE-2018-13379 is a path traversal vulnerability in Fortinet’s FortiGate SSL VPN. An unauthenticated, remote attacker could exploit this vulnerability by sending a specially crafted request containing a path traversal sequence to a vulnerable Fortigate SSL VPN endpoint in order to read arbitrary files from the device. This vulnerability is a pre-authentication flaw, which means an attacker does not need to be authenticated to the vulnerable device in order to exploit it. Successful exploitation would allow the attacker to read the contents of the “sslvpn_websesion” session file that contains both usernames and plaintext passwords.
This vulnerability, along with several other Fortinet flaws, were discovered by researchers Orange Tsai and Meh Chang of the DEVCORE research team as part of their research into breaking SSL VPNs. A blog post about their findings was published in early August 2019; later that month, the first attempts to exploit CVE-2018-13379 in the wild were detected.
CVE-2019-5591 is a default configuration vulnerability in the FortiGate SSL VPN. Under the default configuration, when a Lightweight Directory Access Protocol (LDAP) server sends a connection request to the FortiGate device, the certificate is not verified. To exploit the vulnerability, an attacker could connect to a vulnerable FortiGate device by impersonating an LDAP server. Successful exploitation would allow the attacker to harvest sensitive information intended for a legitimate LDAP server.
CVE-2020-12812 is an improper authentication vulnerability in the FortiGate SSL VPN. This vulnerability exists due to settings used for two-factor authentication—specifically, when two-factor authentication has been enabled under the “user local” setting, but the authentication type is set to remote authentication, such as LDAP. If a VPN user changes the case of their username, a mismatch occurs, and the device won’t prompt for a second factor, allowing an attacker to bypass the two-factor authentication requirement.
SSL VPN vulnerabilities are a goldmine for threat actors
In our 2020 Threat Landscape Retrospective (TLR), CVE-2018-13379 cracked the Top 5 vulnerabilities of 2020, despite being disclosed in 2019. It was one of three SSL VPN vulnerabilities from 2019 that were favored by attackers in 2020. CVE-2018-13379 was also featured in multiple CISA alerts from late 2020 regarding APT groups targeting the public sector (AA20-283A) as well as activity originating from a Russian APT group (AA20-296A). We can expect to see additional advisories from government agencies regarding such legacy vulnerabilities, as threat actors will continue to leverage publicly known and unpatched vulnerabilities.
Cring ransomware group targets vulnerable Fortinet SSL VPNs
In January 2021, Amigo-A, a freelance reporter and researcher, discovered a new ransomware known as Cring.
A new #Cring #Ransomware https://t.co/NmIogn6lZZ
— Amigo-A (@Amigo_A_) January 21, 2021
Extension: .cring
Note: deReadMe!!!.txt
Email: eternalnightmare@***, qkhooks0708@***
We've tracked it down over the past 2 months.
Originals of images are in the article on the site.@demonslay335 @BleepinComputer pic.twitter.com/xztNwcBwf3
Soon after Amigo-A’s disclosure, Switzerland’s Swisscom Computer Security Incident Response Team (CSIRT) tweeted that they had observed Cring being deployed by “human operated ransomware actors.”
CRING a new strain deployed by human operated ransomware actors. After the actors have established initial access, they drop a customized Mimikatz sample followed by #CobaltStrike. The #CRING #ransomware is then downloaded via certutill. ^mikehttps://t.co/v5h8eqHCPt pic.twitter.com/fkU2USEZis
— Swisscom CSIRT (@swisscom_csirt) January 26, 2021
At the time, it was uncertain how Cring gained initial access into their victim environments. However, on April 7, researchers at Kaspersky’s ICS-CERT team published a report regarding an incident investigation involving Cring. Kaspersky’s report linked the primary cause to vulnerable firmware versions on the FortiGate VPN server, and identified CVE-2018-13379 as the initial attack vector that permitted access to the enterprise network, and ultimately led to the deployment of the Cring ransomware.
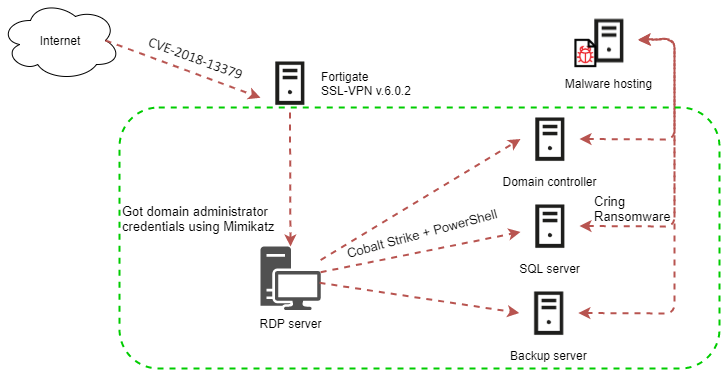
Image Source: Kaspersky ICS-CERT
Mass scanning activity observed following FBI/CISA alert
On April 3, one day after the FBI/CISA joint cybersecurity advisory was published, Troy Mursch, chief research officer at Bad Packets, tweeted that mass scanning activity for CVE-2018-13379 had been detected.
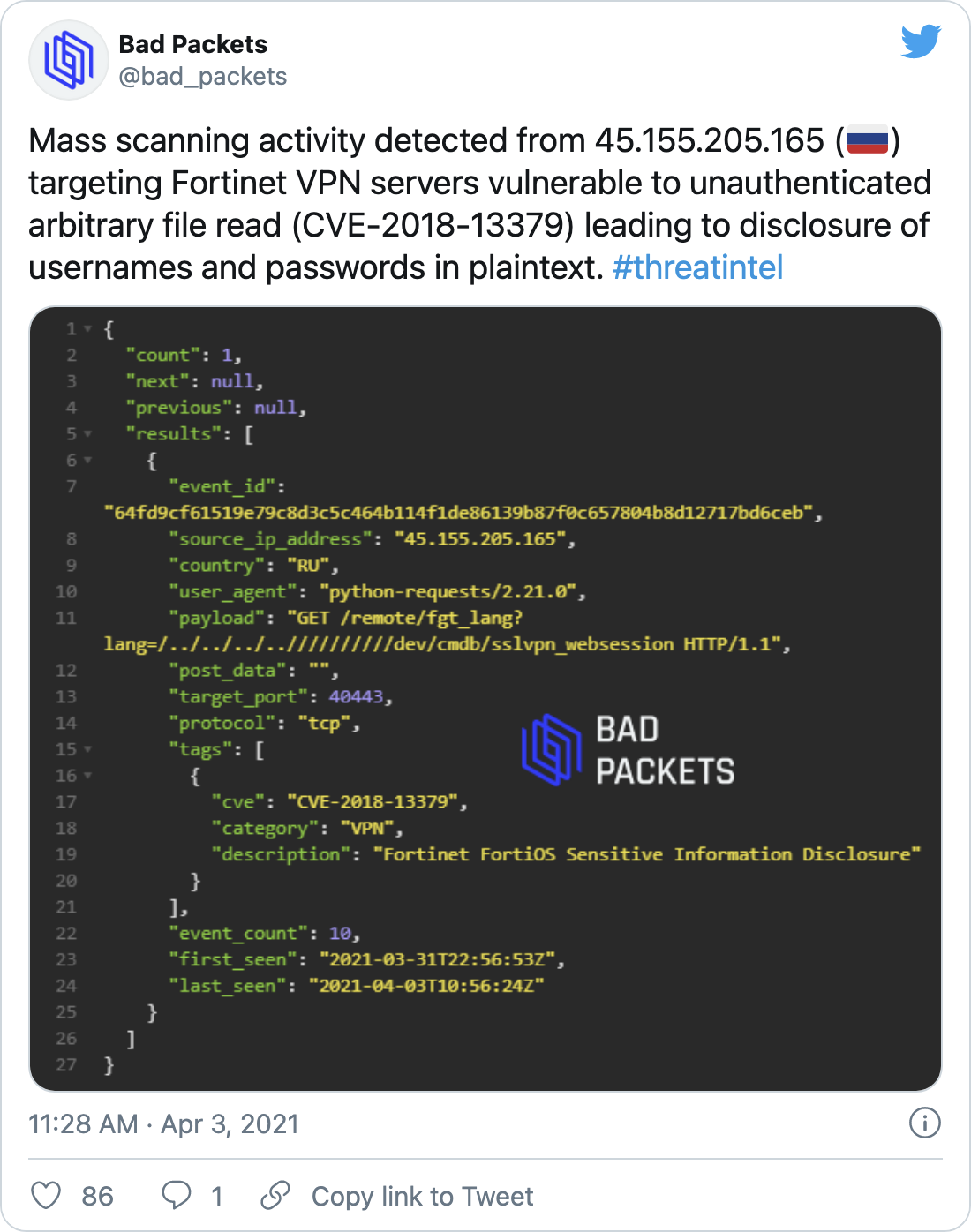
While this latest spike in activity is concerning, there has been significant mass scanning activity linked to the vulnerability since it was disclosed in 2019. As long as there are publicly accessible, unpatched Fortinet systems, we expect both sophisticated APT groups and cybercriminals in general to continue targeting them using these vulnerabilities.
Proof of concept
At the time this blog post was published, there were 10 proof-of-concept (PoC) exploit scripts available on GitHub for CVE-2018-13379.
Solution
Fortinet released patches for all three vulnerabilities over the last few years. The following table contains a list of affected versions and fixed versions by CVE.
| CVE | Affected Versions | Fixed Versions |
|---|---|---|
| CVE-2018-13379 | 6.0.0 through 6.0.4 5.6.3 through 5.6.7 5.4.6 through 5.4.12 |
6.0.5 or 6.2.0 or greater 5.6.8 or greater 5.4.13 or greater |
| CVE-2019-5591 | 6.2.0 and below | 6.2.1 or greater |
| CVE-2020-12812 | 6.4.0 6.2.0 through 6.2.3 6.0.9 and below |
6.4.1 or greater 6.2.4 or greater 6.0.10 or greater |
We strongly encourage all customers or Fortinet users to apply these patches as soon as possible to thwart exploitation attempts.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities can be found here.
Get more information
- FBI/CISA Joint Cybersecurity Advisory for Fortinet Vulnerabilities (April 2021)
- Fortinet Advisory FG-IR-18-384 for CVE-2018-13379
- Fortinet Advisory FG-IR-19-037 for CVE-2019-5591
- Fortinet Advisory FG-IR-19-283 for CVE-2020-12812
- DEVCORE Blog Post on FortiGate SSL VPN Vulnerabilities (CVE-2018-13379)
- Tenable Blog Post for In-the-Wild Exploitation of CVE-2018-13379
- CISA Alert AA20-283A (Vulnerability Chaining Including CVE-2018-13379)
- CISA Alert AA20-296A (Russian APT Activity)
- Kaspersky ICS-CERT Report on Cring Ransomware Attacks
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management



