Auditing OpenStack with Nessus 6.6
Public cloud, private cloud or hybrid cloud—regardless of which cloud-computing model you choose, there is a good chance a part of it is already powered by an open source solution. And when it comes to open source solutions for the cloud, there isn’t a better, more stable and comprehensive solution than OpenStack.
What is OpenStack
Started in 2010 as a joint project between Rackspace and NASA, OpenStack has now become the open source cloud operating system for private cloud deployments. If it’s not clear what that means, then think of it as a layer of software, which can glue together large pools of hardware resources (compute, storage, network) and then present them to be managed under a single interface either through a dashboard or APIs.
Why OpenStack
But with public cloud providers such as Amazon AWS and Microsoft Azure providing such compelling low cost, comprehensive cloud solutions, one might wonder why anyone would opt for OpenStack. There are many reasons. Some customers want complete end-to-end control over their own infrastructures, some want to avoid vendor lock-ins, some want to reduce the burden from expensive licensing fees or some just want to put their existing commodity hardware to good use. And OpenStack provides them with the option to install the software on their own hardware and spin up their own private cloud.
But with all that upside comes additional responsibility. When it comes to security, public cloud providers have long claimed they are responsible for security of the cloud, and the customer is responsible for security in the cloud. But with private cloud deployments, you are responsible for both security of the cloud, as well as security in the cloud.
So once you spin up your own private cloud, the next step is to secure it. And Tenable has just the right solution to help you out.
How can Tenable help?
Over the past few years, Tenable has gradually added support for auditing all major public cloud providers such as Amazon AWS, Microsoft Azure, and Rackspace. Now it's time to go private—to audit private clouds.
With the release of Nessus 6.6, Tenable has now added support for auditing an OpenStack deployment.
There are two things we are doing with respect to OpenStack. First, providing our customers with a snapshot of their OpenStack deployments via the REST API, and second, providing guidance to secure an OpenStack deployment based on the OpenStack Security Guide.
OpenStack deployment snapshot
Often, when traditional computing workloads transition to the cloud infrastructure (public or private), it gets hard to keep track of all the resources deployed in the cloud all the time. This is especially true when multiple users have the privileges to provision new resources on demand. Therefore, keeping tabs on active/inactive instances, tenants, users, networks and subnets changes since the last scan becomes important. Nessus 6.6 solves that problem with its new plugin for OpenStack. Here’s a sample result.
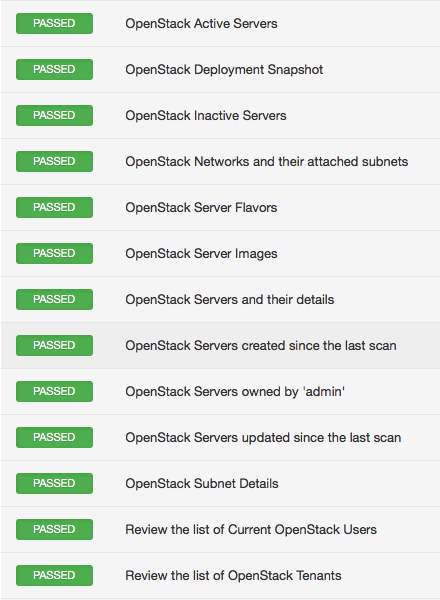
OpenStack security guide
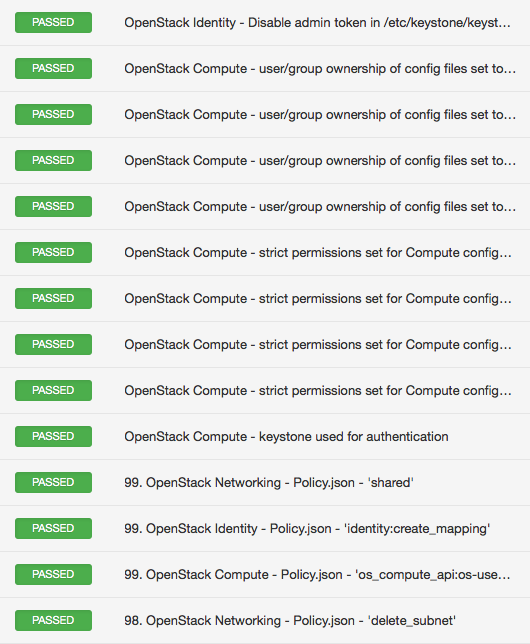
One of the indicators of a mature platform is the existence of a security guide. It shows that the vendor cares and takes security seriously. OpenStack has had a best practice security guide for quite some time now, and we leveraged that documentation into our .audit to provide guidance for hardening OpenStack deployments. The audit reviews configuration of critical files such as nova.conf and keystone.conf and many more to make recommendations if they are in line with best practice security guidelines. The audit also reviews role-based access policies listed under policy.json files, which determine which user can access which objects. Here’s a sample result.
Setting up the scan
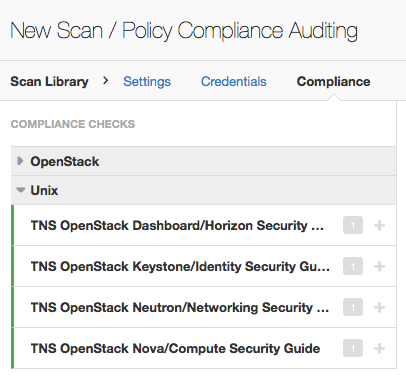
The .audits for OpenStack are under two categories: OpenStack, which includes REST API-based audits, and Unix, which includes security guide-based audits.
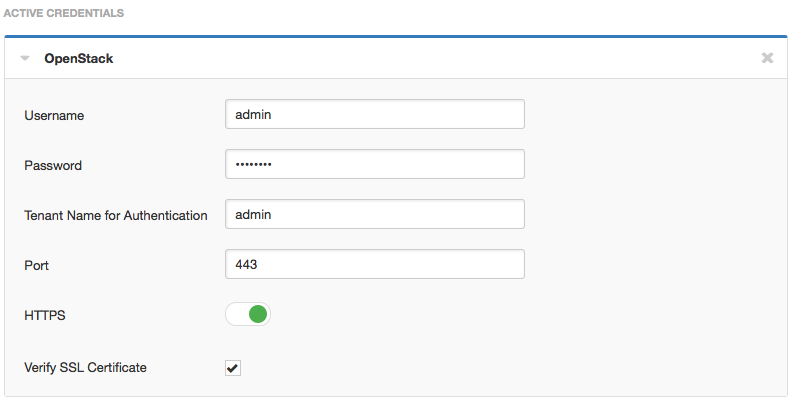
Under the Credentials/Miscellaneous tab, there is new tab to enter credentials for an OpenStack REST API audit. The Unix audits are done over SSH, provided the IP addresses for various nodes (for example, compute, network) are provided as targets.
Wrap-up
With support for OpenStack, Nessus now audits a wide variety of cloud deployments from public cloud providers such as Amazon AWS, Microsoft Azure, and Rackspace to private deployments such as OpenStack. And we plan to add support for similar technologies when they come online.
- Cloud
- Nessus
- Plugins

