by Cody Dumont
May 15, 2017
The new ransomware that is sweeping the planet, called WannaCry and the successor EternalRocks, is causing many organizations much pain as they determine if their network is at risk. Organizations that practice Continuous Vulnerability management can use this data to identify vulnerable systems. This dashboard helps to show how Tenable Security Center can identify vulnerabilities using active, passive and event logs to assist customers.
The WannaCry and EternalRocks malware appears to exploit the SMB flaw that Microsoft provided a patch for in March 2017. While the messaging in the news reports say the worm has been successfully stopped and the overall threat is negligible, the vulnerability still exists on millions of systems and can be exploited again. Failure to remediate impacted systems could leave the data on local hard drives at risk to being held hostage and systems open for exploitation. By leveraging the vulnerability and event data gathered by Security Center, the security operations team can assist the desktop and helpdesk teams in locating and mitigating threats throughout the network.
While the WannaCry malware used two of the exploited used by the NSA and released by the ShadowBrokers dump, the EternalRocks uses seven (7) exploits. EternalRocks has the potential to spread faster and infect more systems. EternalRocks is currently dormant and isn’t doing anything nefarious such as encrypting hard drives. But EternalRocks could be easily weaponized in an instant, making the need for preventive action urgent.
This dashboard displays detailed information about the vulnerabilities and events that can be used to identify vulnerable systems and show the progress to mitigation. Many of the filters used on the dashboard are using the CVEs associated with the Microsoft Knowledge Base Article (MSKB 4013389). The dashboard also provides other vulnerability information related to the Shadow Brokers vulnerability discussed in April 2017.
The Ransomware has been using a specific URL to communicate with hackers, but thanks to a researcher in the UK, the malware threat has been stopped. Using the DNS logs collected by the Tenable Security Center CV can identify any hosts making a request to that URL. Additionally, using the connection data collected from the Tenable Nessus Network Monitor (NNM), Security Center can track the systems that are communicating using SMB protocol by tracking usage of port 445. While SMB is a legitimate protocol to use, the security operations team can monitor for unusual SMB traffic. Active scanning plugins use a CVE to report to Security Center if the system is vulnerable. By using all three methods of detection, Security Center customers can have an in-depth and thorough look into their network to identify vulnerable systems.
This dashboard is available in the Security Center Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Security Center Feed under the category Threat Detection & Vulnerability Assessments. The dashboard requirements are:
- Security Center 5.4.5
- Nessus 6.10.5
- NNM 5.3.0
Tenable Security Center is the market-defining continuous network monitoring solution, which assists organizations in securing their internal network. While Security Center is continuously updated with information about advanced threats and zero-day vulnerabilities, there are several information plugins and collected events that help analysts anticipate systems that can be at risk to new threats such as the WannaCry ransomware. Active scanning periodically examines systems to determine vulnerabilities and compliance concerns. Agent scanning enables scanning and detection of vulnerabilities on transient and isolated devices. Security Center provides an organization with the most comprehensive view of risks with in the network and the intelligence needed to support effective vulnerability remediation efforts.
Components
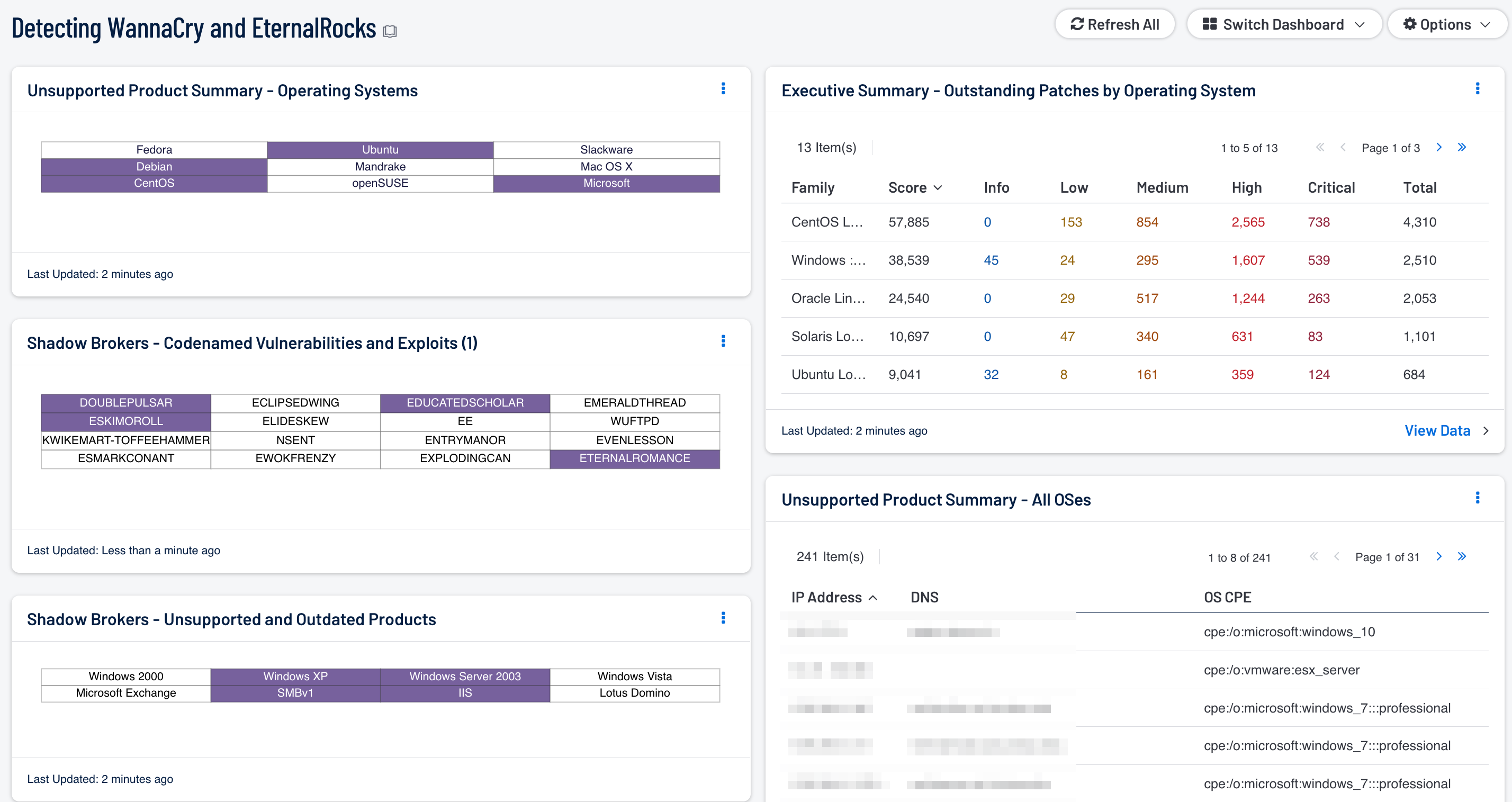
Shadow Brokers - Codenamed Vulnerabilities and Exploits: This matrix displays the codenamed vulnerabilities and associated exploits published by the Shadow Brokers hacking group. Each cell filters for a specific vulnerability or exploit and turns purple when at least one instance is detected. Security teams can use this component to quickly identify which vulnerabilities their network may be susceptible to.
Shadow Brokers - Unsupported and Outdated Products: This matrix specifically identifies the unsupported or outdated operating systems or services known to be particularly vulnerable to exploitation. Each cell filters for outdated or unsupported versions of a specific product and turns purple upon detection. Security teams can use this component to determine which systems require immediate updates in order to remediate the detected vulnerabilities.
Executive Summary - Outstanding Patches by Operating System: This table displays counts of vulnerabilities based on the OS local security check plugins. SecurityCenter CV provides a comprehensive collection of plugins for a large variety of operating systems to check for security issues. Having a great breadth of checks helps to ensure a maximum coverage for OS vulnerabilities that are identified for remediation.
Unsupported Product Summary - Operating Systems: This matrix reports on operating systems that are no longer supported. The matrix displays popular operating systems, but is easily modified to fit organizational requirements. Plugin ID #33850, with vulnerability text filters that filter for the appropriate operating system name in the plugin output, alert on Unix-based operating systems that are no longer supported. Keyword filters, along with a CPE string for Microsoft, is used to alert on end-of-life Microsoft operating systems by turning the indicator purple when an alert is present.
Unsupported Product Summary - All OSes: This table lists the hosts determined to be running unsupported operating systems. The table filters for operating systems by CPE and uses the plugin keyword “unsupported.” Security teams should use this table to prioritize systems that are running unsupported operating systems for upgrade.