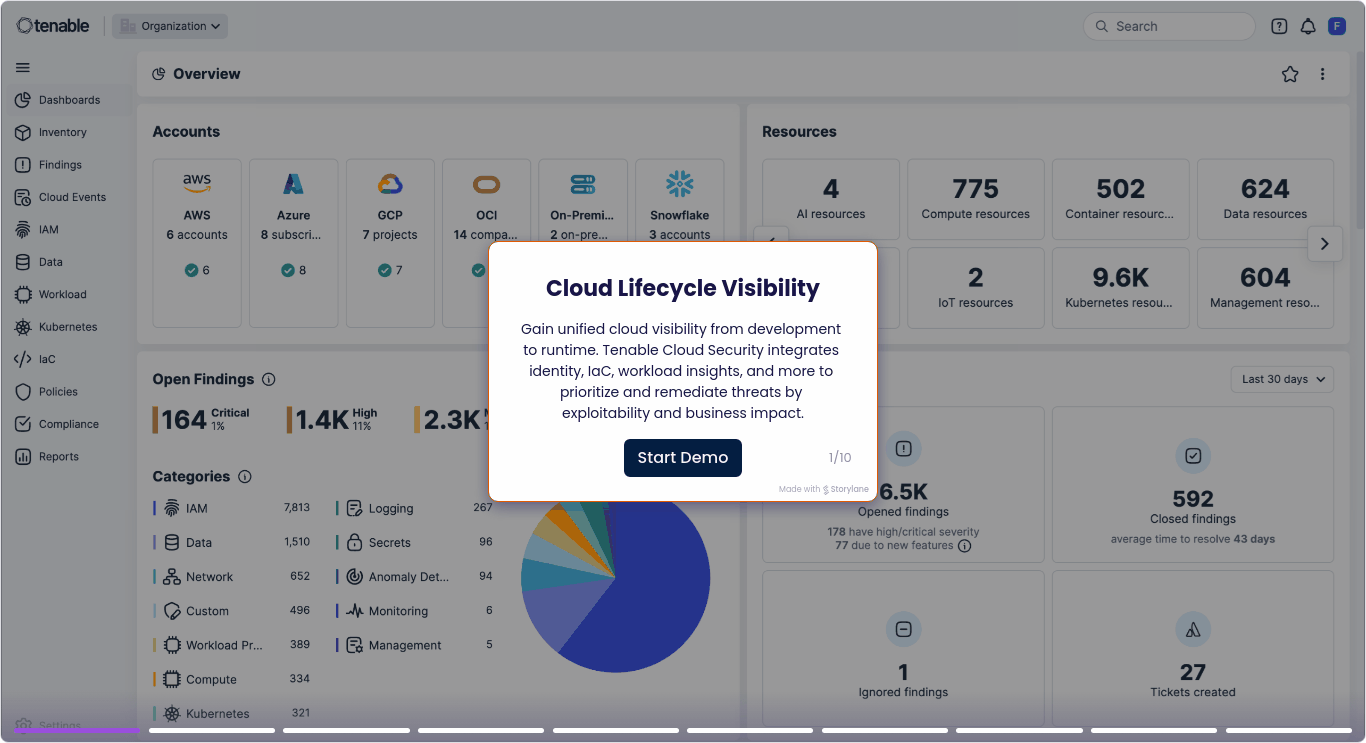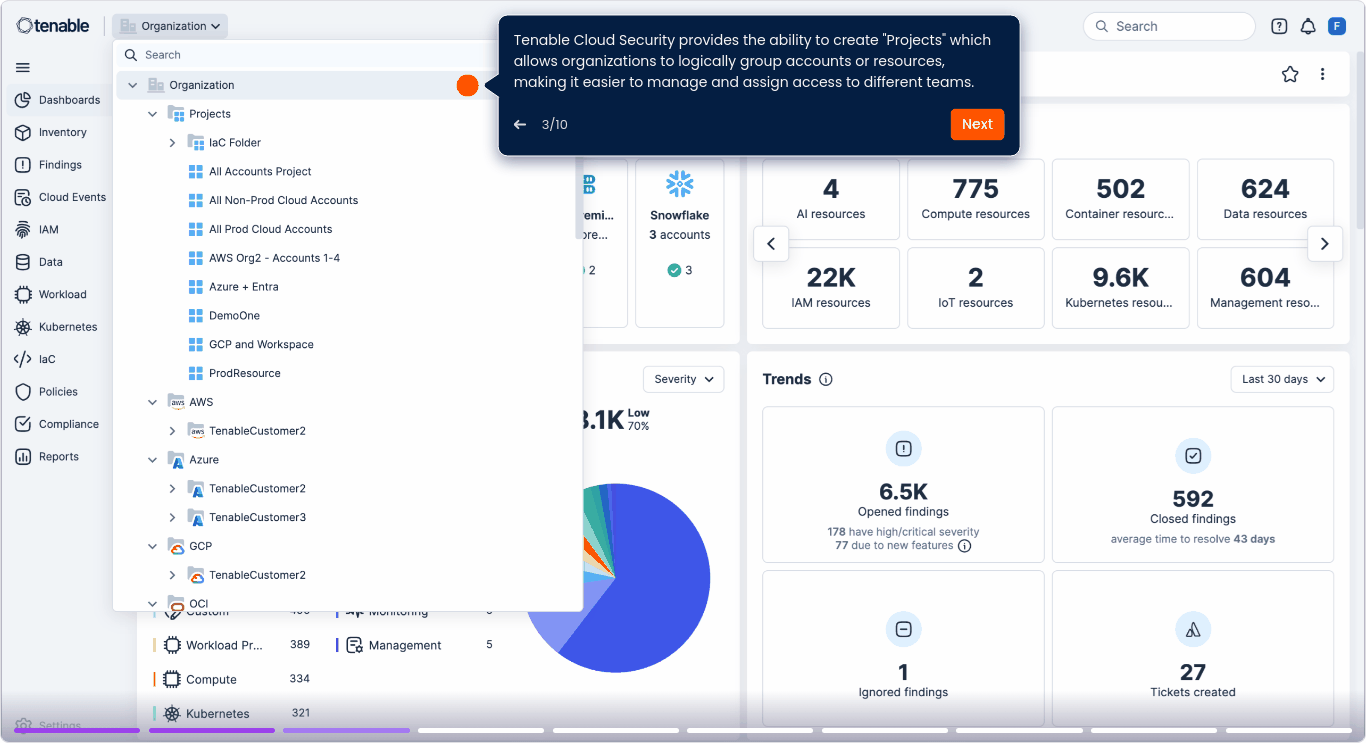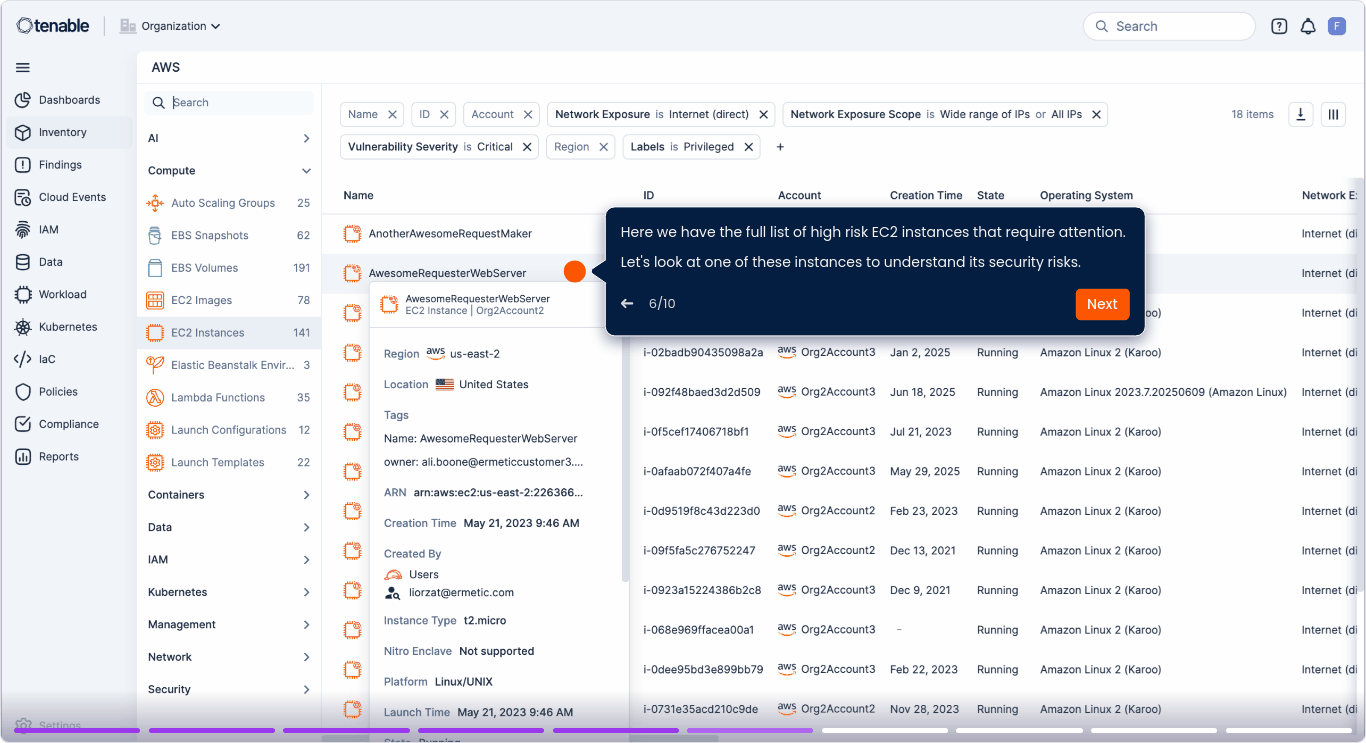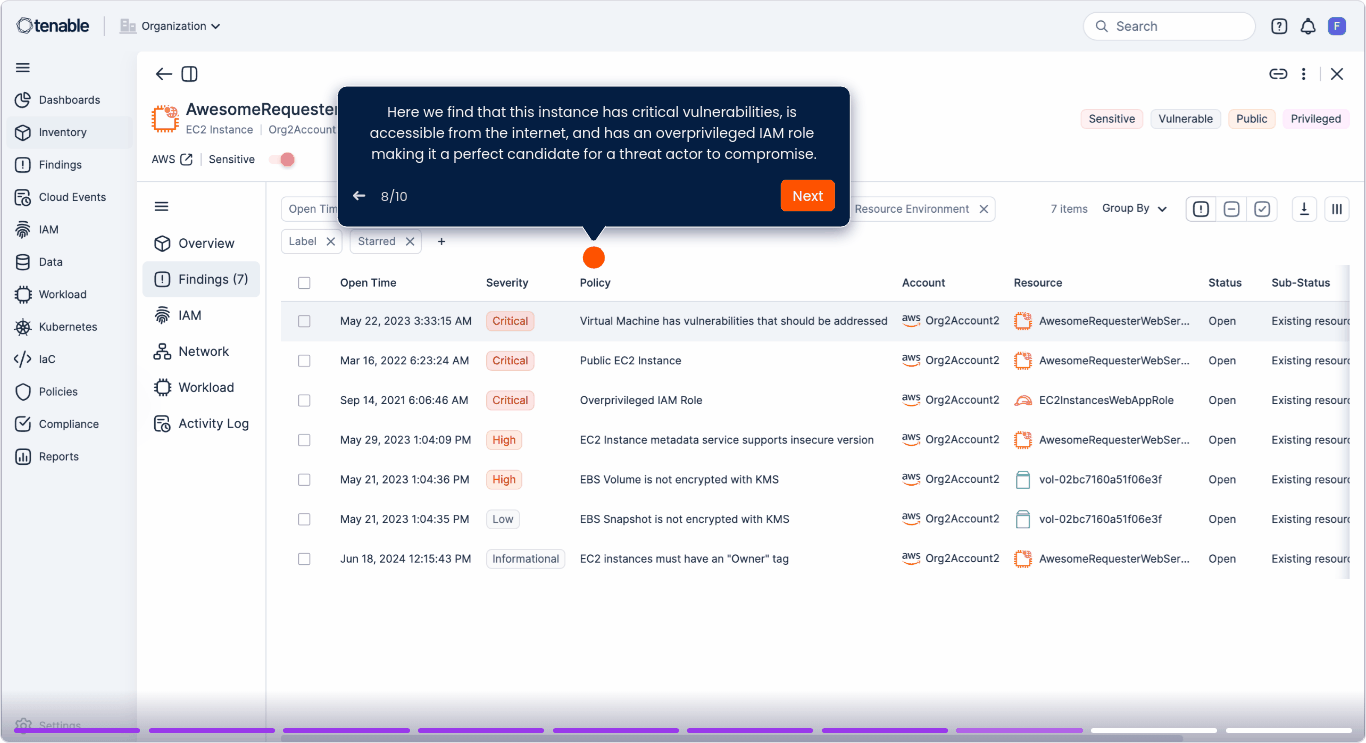
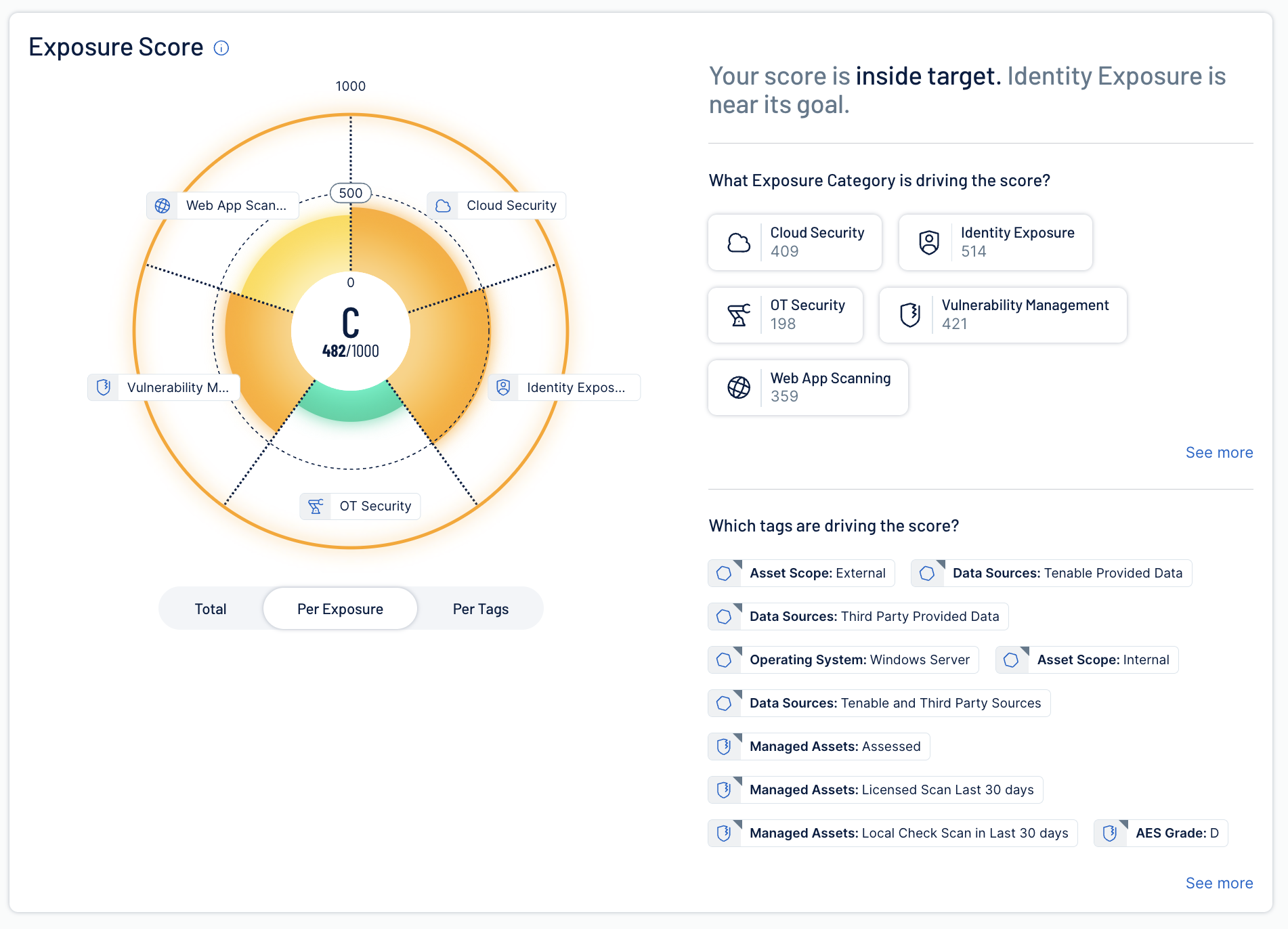
Obtenga visibilidad completa del riesgo en la nube y seguridad del SDLC
Los errores de configuración y la dispersión de la identidad a lo largo de su superficie de ataque en la nube en expansión aumentan el riesgo y abruman a sus equipos de seguridad con alertas. Elimine el ruido de las alertas y detenga los problemas antes de que lleguen a la producción. Acelere la detección (shift left) al escanear plantillas de infrastructure as code (IaC) como Terraform, CloudFormation y ARM. Con tecnología de Tenable One, usted puede conectar el código al contexto de tiempo de ejecución para detectar y reparar problemas de seguridad antes de la implementación, reducir el retrabajo y proporcionar una infraestructura en la nube segura más rápido.
Proteja todos sus flujos de trabajo, del desarrollo a la producción
Obtenga seguridad en la nube integral a lo largo de DevOps, SecOps y detección y respuesta.
Trazabilidad continua de SDLC a producción
Aceleración de la corrección a través de la atribución del propietario
Aplicación de las políticas que consideran las desviaciones
Correlación de identidades y derechos con contexto enriquecido
Gráfico de exposición unificado en la nube y TI
Seguridad en la nube que abarca todo su ciclo de vida
Tenable Cloud Security conecta las comprobaciones de tiempo de creación con la protección de tiempo de ejecución para que usted pueda detectar errores de configuración temprano y minimizar el riesgo continuo.
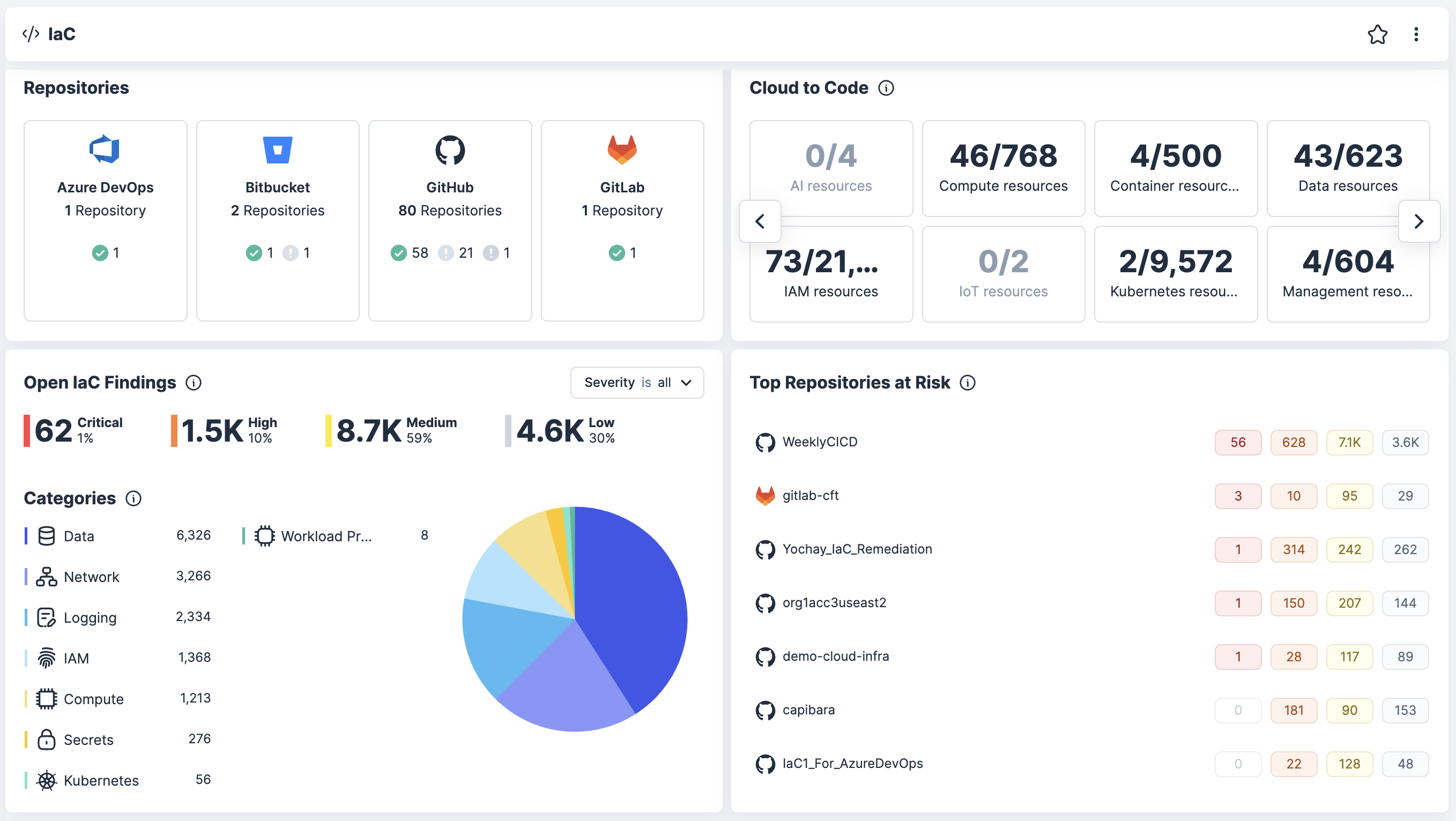
Obtenga una trazabilidad continua desde el SDLC hasta la producción
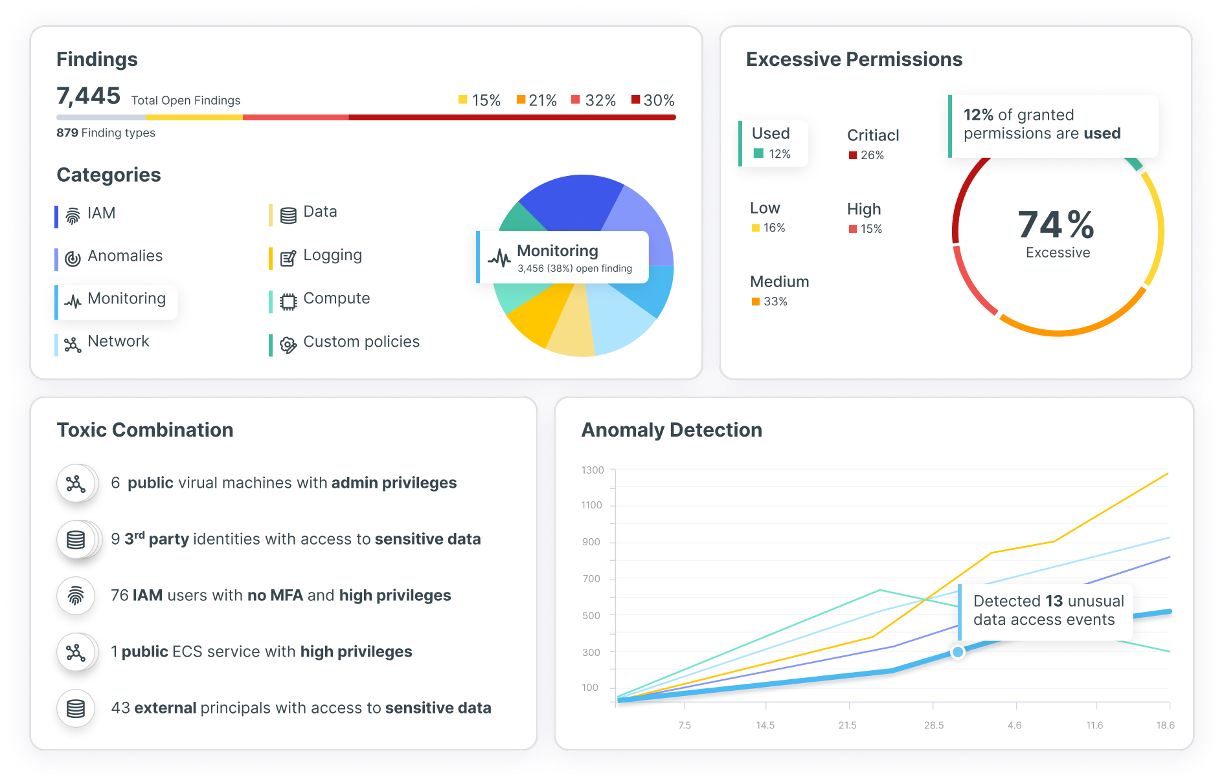
Correlacione vulnerabilidades, errores de configuración y riesgos para las identidades con el fin de revelar combinaciones tóxicas y rutas de ataque a lo largo de código, compilación, implementación, configuración y tiempo de ejecución.
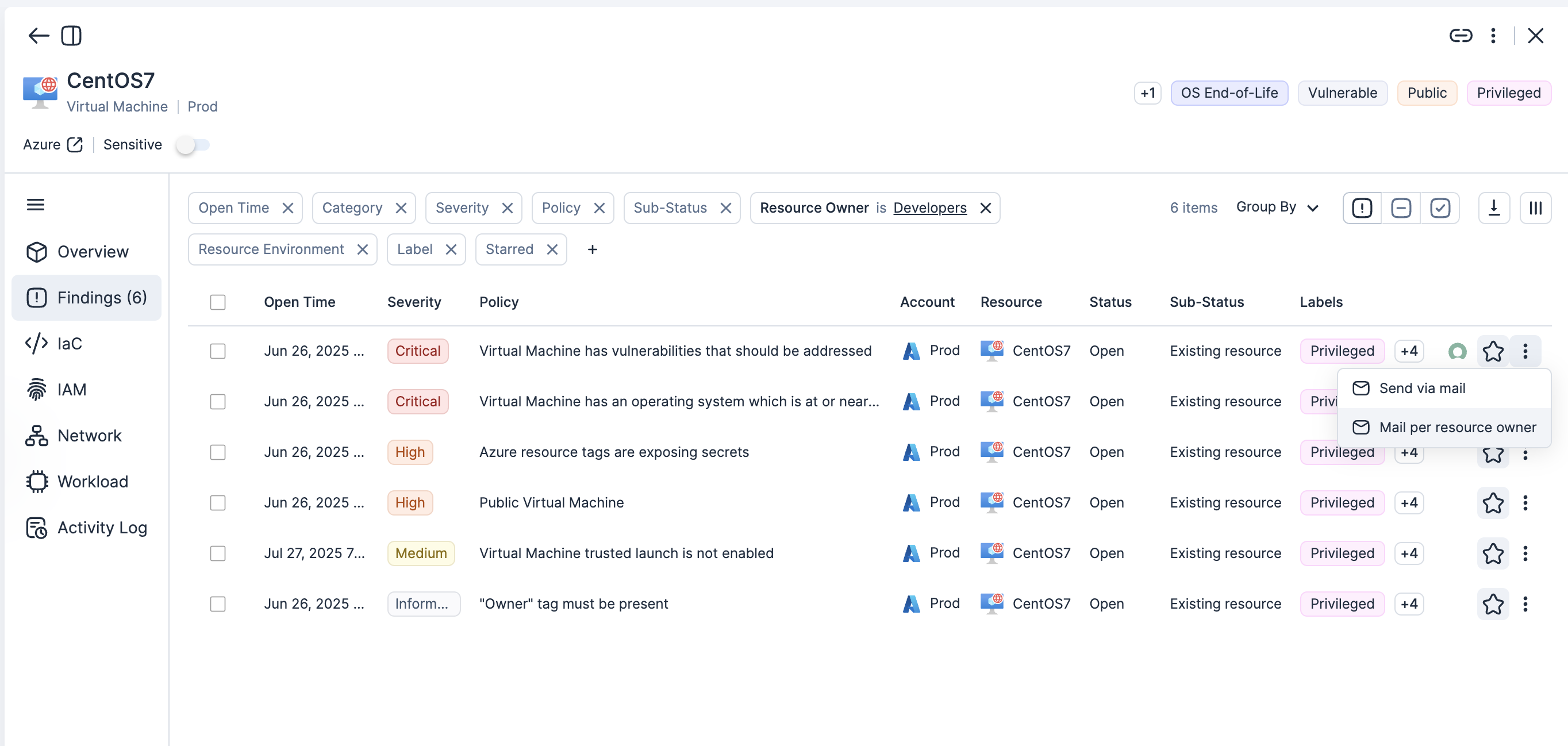
Acelere la corrección mediante la atribución del propietario
Correlacione cada problema a su equipo responsable, servicio o repositorio con guía de reparación procesable.
Aplique políticas que consideran las desviaciones
Aplique continuamente las protecciones de seguridad desde CI/CD hasta el tiempo de ejecución para detectar y prevenir las desviaciones de configuración, brinde soporte a SAST y mantenga el cumplimiento.
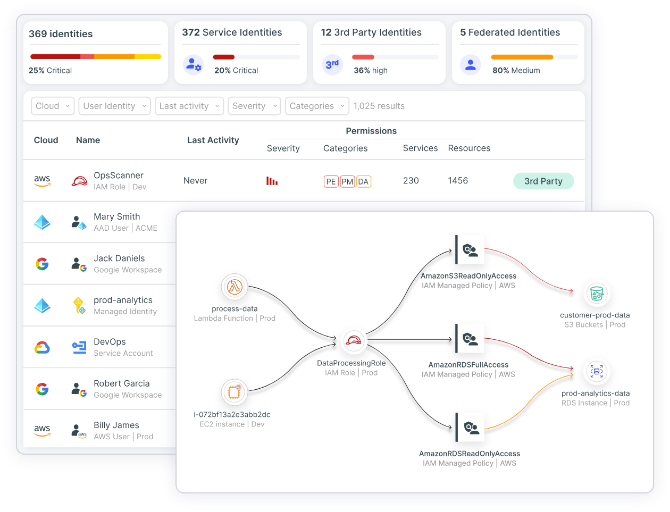
Use correlación de identidades y derechos con contexto enriquecido
Correlacione el acceso a lo largo de usuarios, roles, entidades de seguridad de servicio e identidades federadas en tiempo real.
Unifique los gráficos de exposición en la nube y TI
Correlacione los riesgos nativos en la nube y de TI en un único gráfico de exposición. Elimine los silos y priorice las amenazas en función de la explotabilidad y el impacto en el negocio.
Obtenga más información sobre Tenable Cloud Security
El uso de la automatización [de Tenable Cloud Security] nos permitió eliminar procesos manuales exhaustivos y realizar en minutos lo que le habría llevado a dos o tres profesionales de seguridad meses.
- Tenable Cloud Security