Understanding NIST’s Cybersecurity Framework
NIST’s Cybersecurity Framework (CSF) is likely to become the basis for what's considered commercially reasonable in regards to securing an organization’s infrastructure. For this reason alone companies should pay close attention to the CSF and, even if they don’t follow it completely, should at least understand where they are deficient and why.
The CSF is a valuable indicator of what a standard of care should be. The document provides a standard measurement that organizations can agree on in terms of assessing risk assessment. The CSF will give higher levels of management, such as a boards of directors, CISOs, audit committees, and senior executives an understanding of what their current security posture is, where it should be and a clear roadmap of how to get there. Hopefully this will free up some much needed resources inside organizations to address these issues too.
Another reason for paying attention is that while the framework may be voluntary, it will probably become the de-facto standard that organizations will be judged against if a breach occurs. Finally, the standard isn’t just for government agencies, but will apply to private businesses that are operating in critical infrastructure areas such as transportation, food processing and water treatment. There are actually 16 different infrastructure areas that cover just about every private business.
The CSF is not a checklist like other standards such as PCI. There is no list of requirements that if you meet you can check the box and when all checks are completed you are done. It is more a set of industry best practices to apply a risk based approach to improve your organization’s security. It offers a core set of activities to anticipate and mitigate against attacks on systems. It draws heavily from over three thousand industry corporations and individuals and is intended to adapt and change over time along with new technologies.
To understand the CSF you first have to understand its various jargon. This isn’t just tolerating government-speak, but a way to use a common language and vocabulary which organizations could adopt and use in their security policy documents in the future. So bear with me as I explain the framework terms.
It starts with five concurrent ‘Cores’ - identify, protect, detect, respond and recover. (See the infographic below.) Each Core then has several Tiers, which describe the level of sophistication and rigor an organization employs in applying its cyber security practices. Again, moving from one tier to the next is not necessarily a sign of progress but a way to evaluate how such a move plays out in terms of risk reduction. The tiers are named: partial, risk informed, repeatable and finally adaptive. Every company doesn’t have to have everything at the adaptive tier, because one size does not fit all situations.
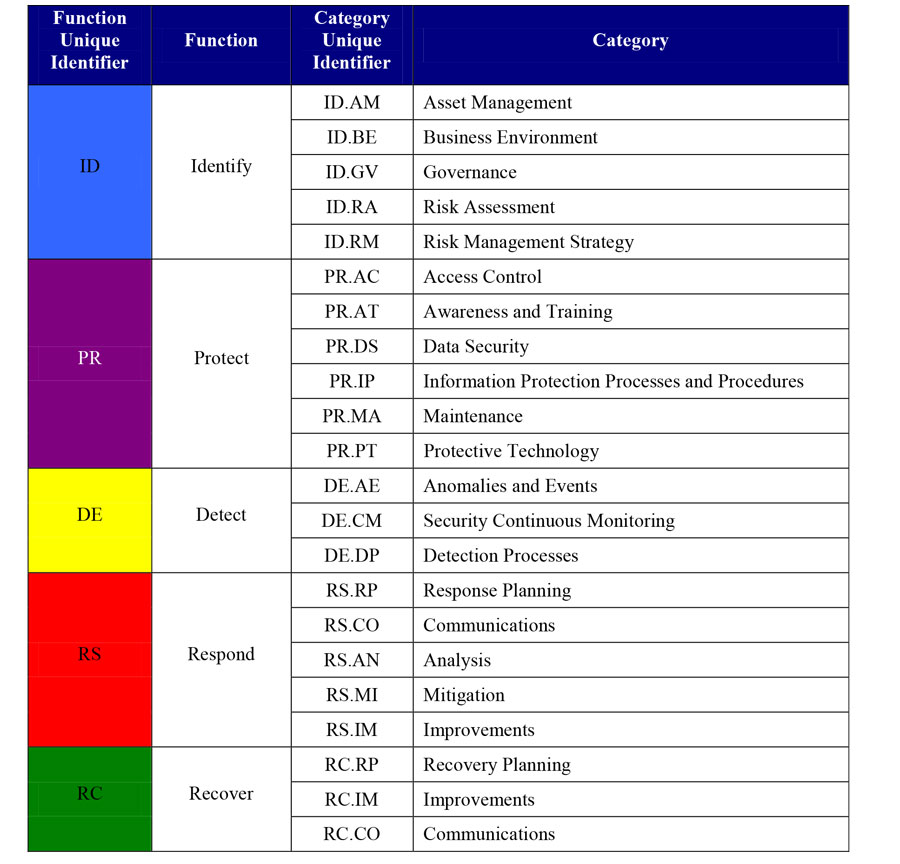
This is because each industry is different and each company is different. What works for an electric company may not work for a manufacturing company and what works for a large company may not work for a small company.
Tiers are followed by ‘Profiles’, which aligns the core functions and categories with business requirements, risk tolerance and resources. Profiles can help determine what an organization’s current risk tolerance appetite is and how to establish a roadmap for reducing risk.
The framework encourages organizations to create a profile to describe their current cyber security posture and then describe their target state for where they want to end up. This then allows for the identification and prioritization of improvement opportunities with a continuous and repeatable process that can be assessed as the organization moves toward the desired state.
The CSF does not create anything new, it draws from other existing standards that can be applied to facilitate behavioral changes in an organization. The objective of the CSF is to elevate cyber risk at the corporate level to the same level of financial or liability risk. To do this the CSF has drawn from other works such as the Control Objectives for Information and Related Technology (COBIT), Council on Cybersecurity (CCS) Top 20 Critical Security Controls, as well as ANSI/ISA and ISO/IEC standards.
SecurityCenter Dashboards
Now that you know more about the Cyber Security Framework, Tenable’s SecurityCenter can give you an idea of where your organization currently stands in regard to some of the technical metrics that are pointed out in the Framework. Several dashboards have been created for SecurityCenter that allow you to use already available data to visualize aspects of the CSF.
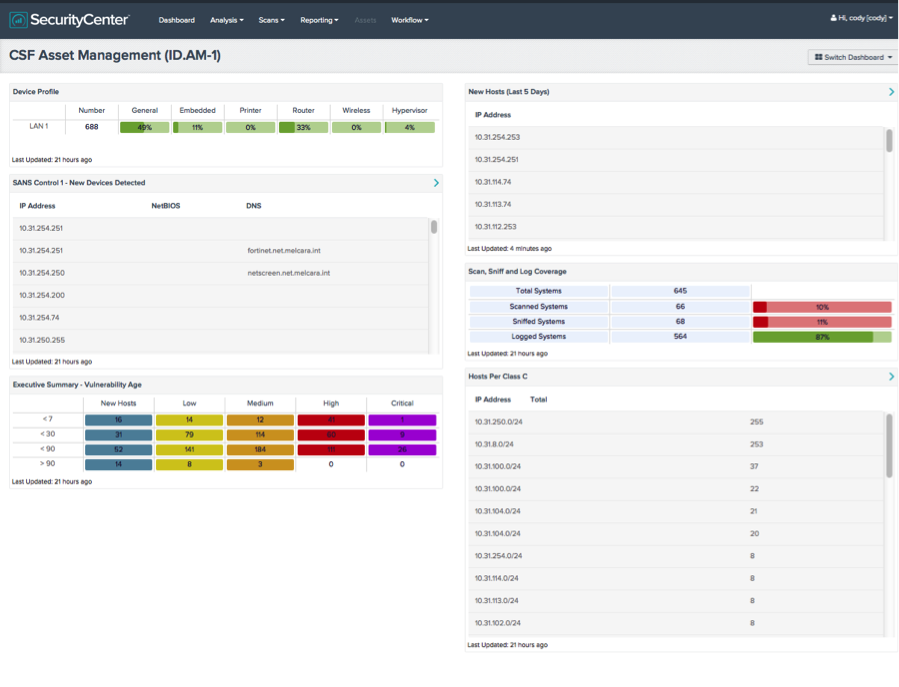
For example, the CSF Asset Management dashboard shown above helps to identify the hardware assets present on your network, will automatically discover new devices as they appear on your network and inform you of the vulnerability status of those devices.
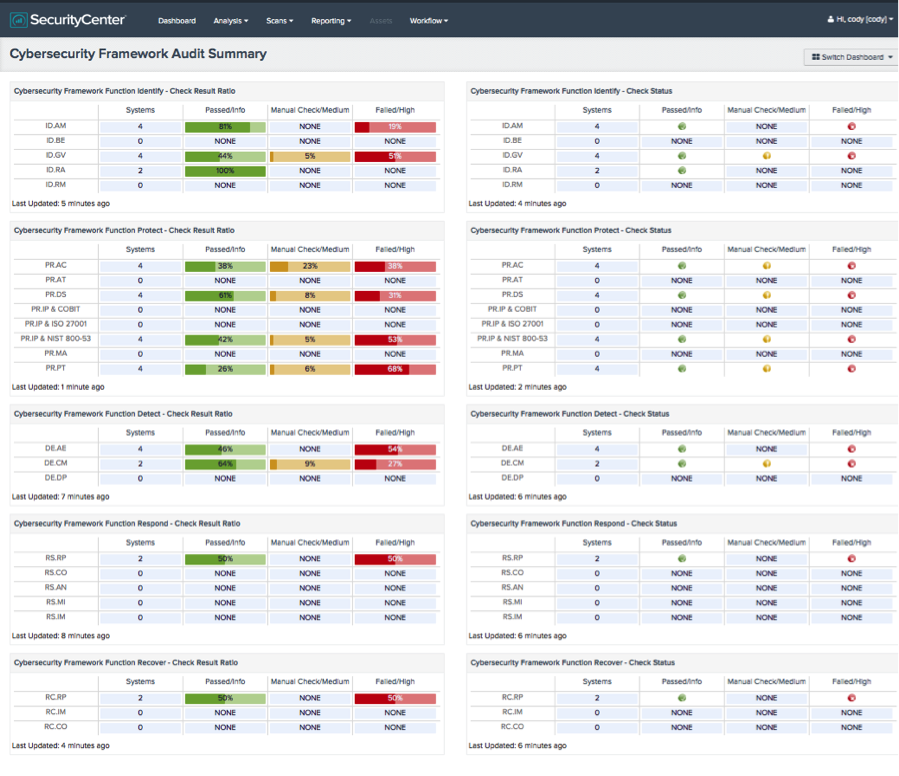
There are also three versions of the Cybersecurity Framework Audit Summary dashboard for SecurityCenter that show components as ratio based, icon based or a combination of the two.
You can use these dashboards and others to check the current status of your organization and use the information to help develop plans to move from one tier to the next.
- Dashboards
- NIST
- SecurityCenter
- Standards

