Tracking Down Privilege Escalation Failures

Credentialed scanning is a key aspect of any vulnerability management program, but how can you be sure the scans are successful? Changes to infrastructure or specific hosts could result in the wrong credentials being used to elevate privileges during scans. If this happens, your scans could fail to gather the vulnerability data essential to effectively implementing your vulnerability management plan. The Tenable.io™ Elevated Privilege Failures report can give you detailed insight into the *nix hosts in your network that may not be getting scanned as thoroughly as believed.
Privilege escalation in credentialed scans
Configuring a non-root account on all scan targets is recommended when running credentialed scans
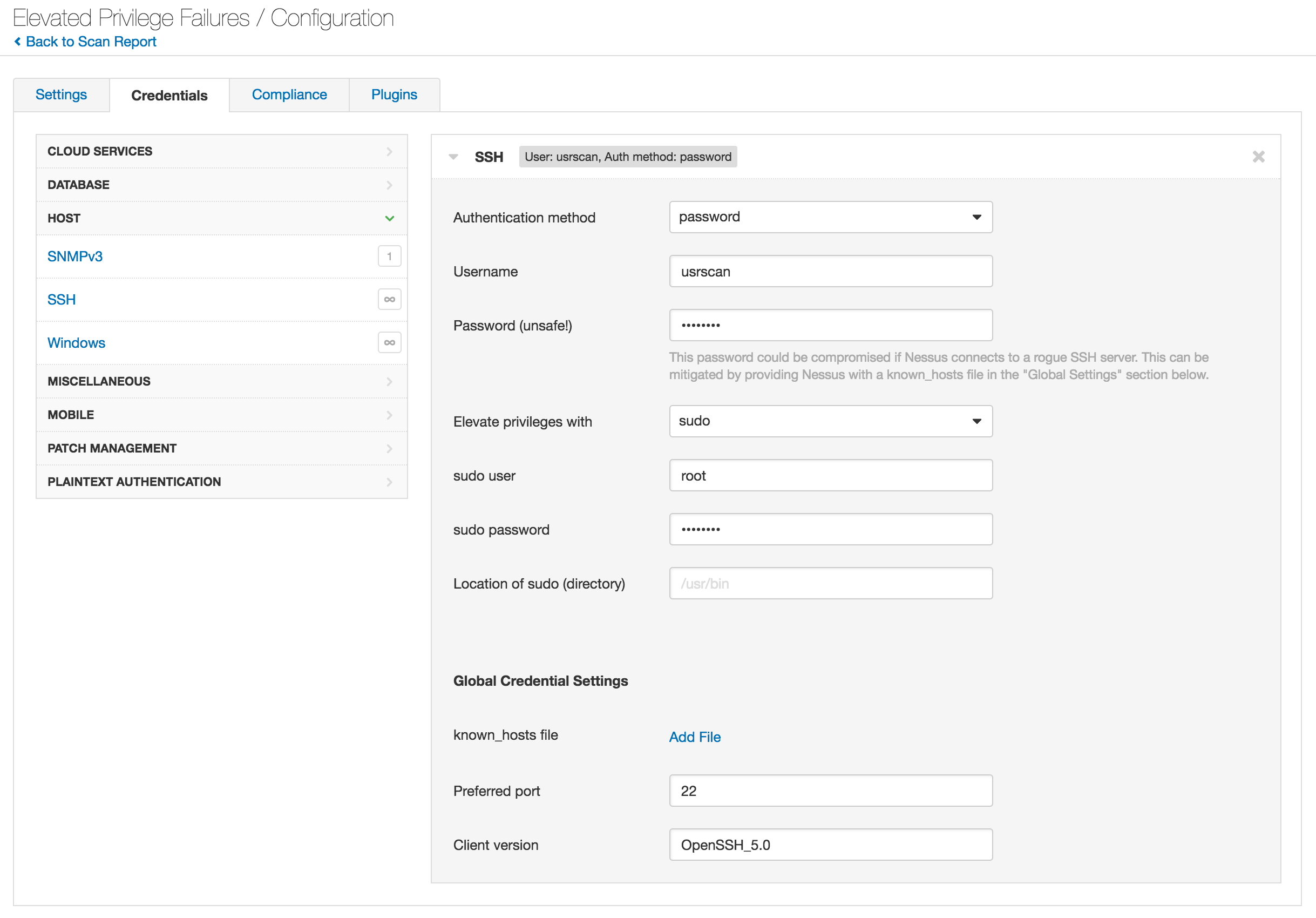
When SSH is used for credentialed scanning, you have the option of specifying an account to use for privilege elevation. This feature lets you use a non-root account for the scan to log in via SSH. The scan will then escalate privileges with the configured root account to gather data that is not available to non-root users. The method of separately logging in and elevating privileges keeps root credentials off the wire, thereby being more secure. Therefore, configuring a non-root account on all scan targets is recommended when running credentialed scans.
The Tenable.io solution
Tenable.io can efficiently identify hosts where privilege escalation in credentialed scans has failed. The Elevated Privilege Failures report provides detailed information on these hosts.
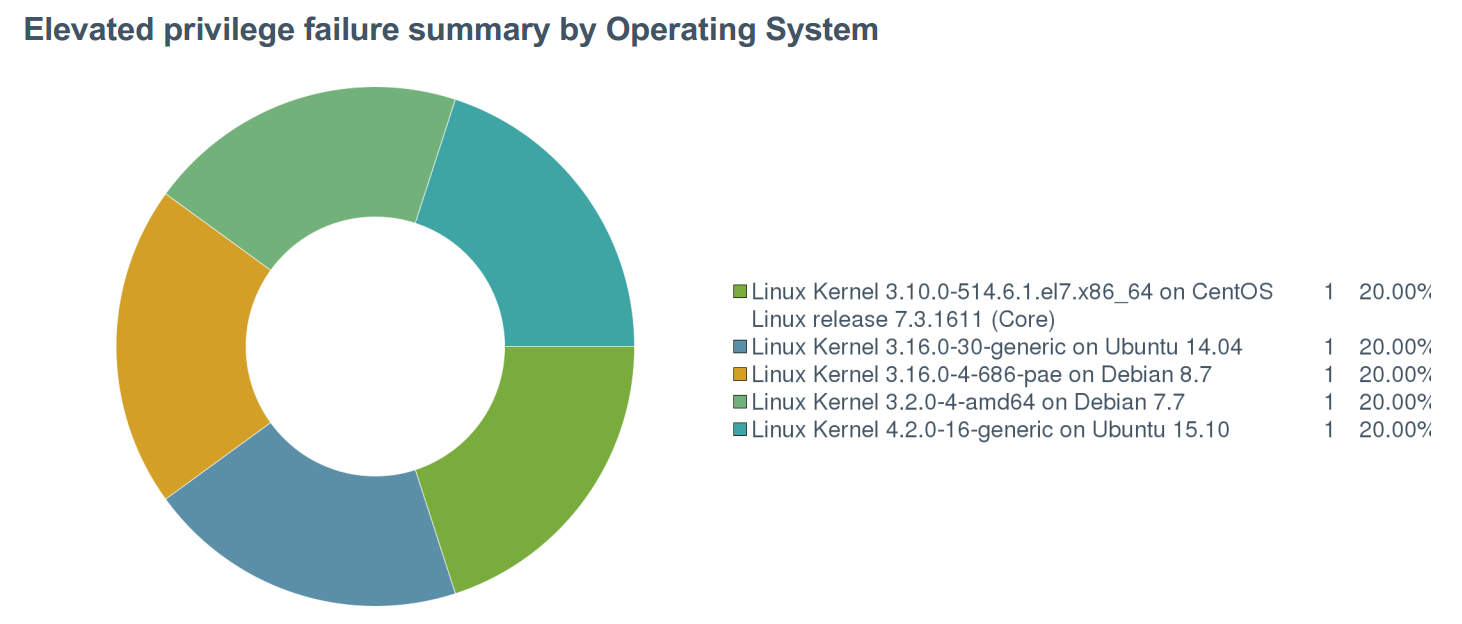
The Elevated Privilege Failures report provides you with comprehensive and detailed lists of the hosts on your network that may not be getting scanned thoroughly. This information is broken down by operating system and host. The Elevated privilege failure summary by Operating System pie chart shows privilege escalation failures by operating system and could indicate whether recent configuration changes may have caused the failures to start happening. For example, you will be better able to track the source of failures if the root account password has been changed for a specific operating system but not network-wide.
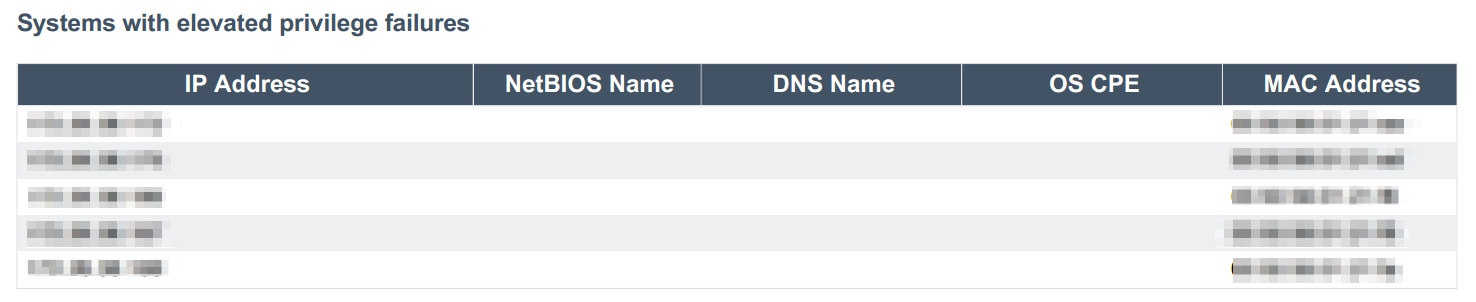
The Systems with elevated privilege failures table lists which hosts’ failures have been detected based on the results of the Authenticated Check: OS Name and Installed Package Enumeration plugin (ID 12634). The table filters for plugin results that contain a phrase indicating that local privileges were not successfully elevated. This table also acts as an index for the next table, which provides more in-depth information about the hosts impacted.
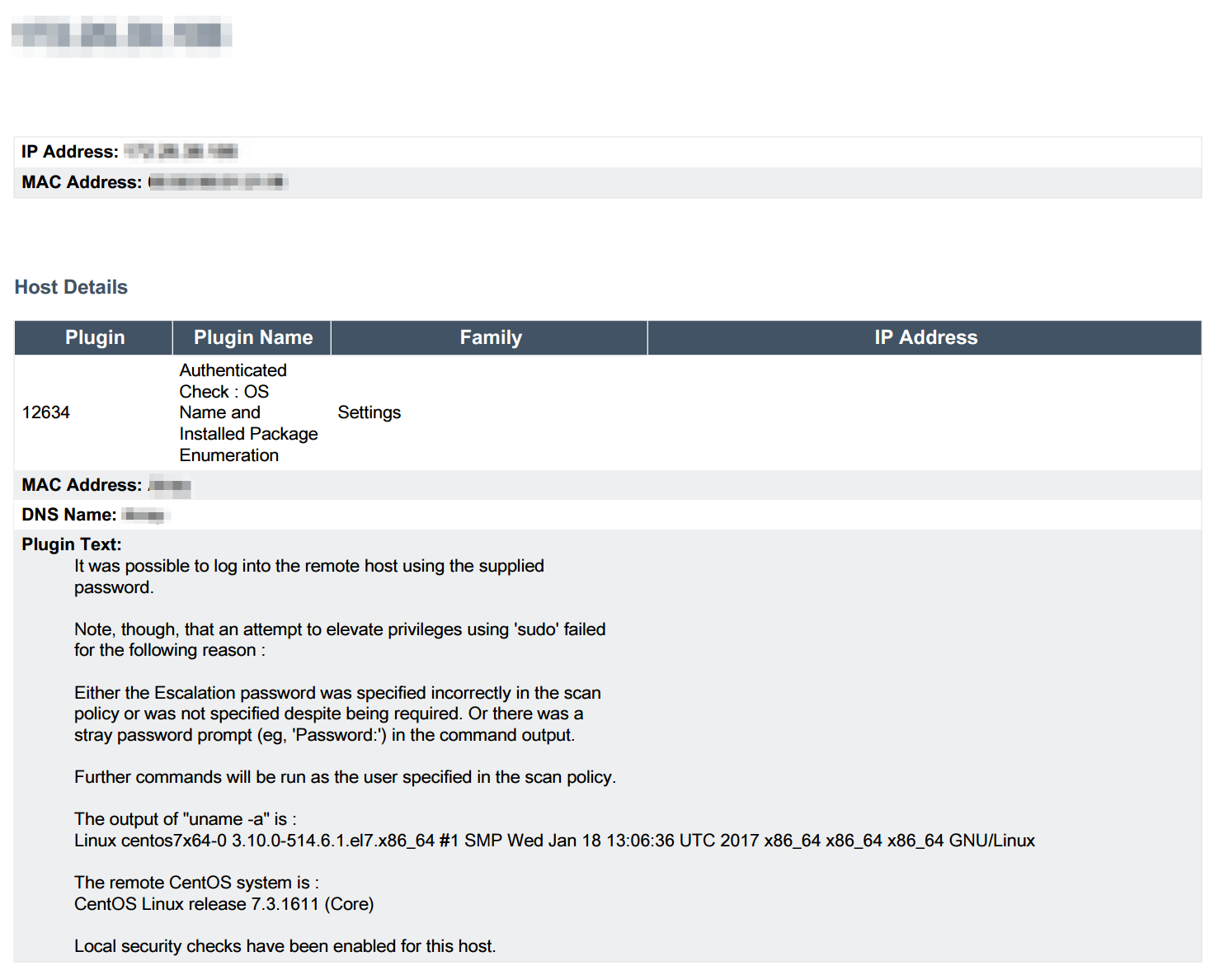
The vulnerability details table lists results from plugin ID 12634, including the plugin output, for each host impacted. Details about the host, such as the IP and MAC addresses, are provided along with the plugin output that describes the attempt and failure to elevate the privileges of the scan account.
Regardless of your approach to credentialed vulnerability scanning with Tenable.io, ensuring proper credential configuration is the first step to gathering thorough scan results. Tenable.io provides information security professionals with the tools and resources needed to perform accurate and rigorous credentialed vulnerability scanning. The Elevated Privilege Failures report provides insight into potential failures impacting the accuracy of credentialed scanning. Armed with Tenable.io, you can be sure that your credentialed scans are able to gather all available data.
Ensuring proper credential configuration is the first step to gathering thorough scan results
Try Tenable.io
Tenable.io provides accurate information on how well your organization is addressing security risks and helps track improvements over time. Get a free trial of Tenable.io Vulnerability Management for 60 days.
- Reports
- Tenable Vulnerability Management
- Tenable Vulnerability Management (DO NOT USE)
- Vulnerability Management
- Vulnerability Scanning