Objects in Mirror Are Closer Than They Appear: Reflecting on the Cybersecurity Threats from 2019

Tenable’s Security Response Team reviews the biggest cybersecurity threats of 2019.
With 2019 coming to an end, the Tenable Security Response Team reflects on the vulnerabilities and threats that had a major impact over the last year. Data breaches, malware, new vulnerabilities and exploit techniques dominated the news, as attackers and defenders continue the perpetual cat and mouse game. After reviewing hundreds of events, the team zeroed in on four areas of interest that highlight the significant threats we observed in 2019:
- Remote Desktop Protocol Vulnerabilities
- Showstopper Zero Days
- Speculative Execution Flaws
- Ransomware
2019: The year of Microsoft Remote Desktop Protocol vulnerabilities
In May, Microsoft released a patch for one of the most widely discussed CVEs of the year, CVE-2019-0708. Dubbed BlueKeep, the remote code execution (RCE) vulnerability in the Microsoft Remote Desktop Protocol (RDP) could allow an unauthenticated, remote attacker to exploit and take complete control of a vulnerable host.
This flaw occurs prior to any authentication and requires no user interaction, making this vulnerability extremely dangerous. Due to the severity of the issue, Microsoft took the extraordinary measure of releasing patches for Windows XP and Windows Server 2003 despite these operating systems being long out of support. The flaw was eventually noted to affect systems as far back as Windows 2000 all the way up to Windows Server 2008 R2. Microsoft warned of BlueKeep’s potential impact, even suggesting the vulnerability could be wormable, gaining similar notoriety to the WannaCry ransomware attack from 2017. The flaw gained so much attention that both Microsoft and the U.S. National Security Agency urged administrators to patch systems or deploy mitigations immediately.
Seeing double with DejaBlue
In nearly every month since May, Microsoft’s Patch Tuesday or Update Tuesday included various patches related to RDP vulnerabilities, as the protocol faced increased scrutiny from the security community and Microsoft alike. In August, Microsoft patched four additional CVEs (CVE-2019-1181, CVE-2019-1182, CVE-2019-1222 and CVE-2019-1226) covering pre-authentication RCE vulnerabilities in Remote Desktop Services. These new vulnerabilities, dubbed DejaBlue, expanded the list of affected OS variants for Windows. Between BlueKeep and DejaBlue, all supported versions of Windows were affected.
As the security community speculated about widespread exploitation of these vulnerabilities, researchers pleaded for organizations to patch, knowing it was only a matter of time before an exploit would be released into the wild. In November, the first confirmed in-the-wild exploitation of BlueKeep was discovered. The attackers had repurposed a recently released exploit module to distribute a cryptocurrency miner, and the exploit attempt ended up crashing several machines in the honeypot network where the attacks were discovered.
A patch a day keeps attackers at bay
While some researchers suggest BlueKeep is unlikely to spread as a worm, many agree there is still major potential for the exploitation of these RDP vulnerabilities. In any case, RDP brute force attacks have increased since BlueKeep was announced, reminding us that attackers are opportunistic and take advantage of any technique available. With over 500,000 vulnerable hosts online as of November 2019, we expect BlueKeep will continue to be a problem for organizations as we head into 2020. While it is likely that new RDP exploits could be discovered next year, common tried-and-true methods such as brute forcing RDP credentials are still popular and often successful approaches attackers will continue to employ.
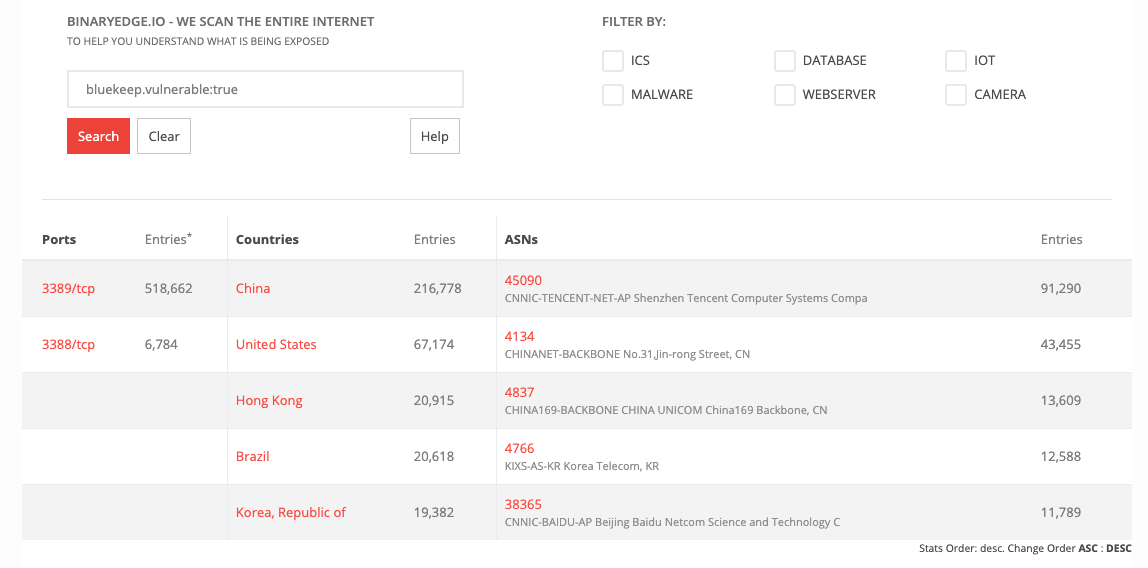
BinaryEdge results for internet-facing assets potentially affected by BlueKeep
Authored by Scott Caveza, Research Engineering Manager
Showstopper Zero Days: Vulnerabilities that Affected Everyone

Another trend in 2019 (and years prior) has been zero days and critical vulnerabilities, which can be overwhelming and difficult for businesses to keep up with. You need to find time outside your normal patch cycle – and potentially suspend other work – to get assets tested and updated. When vulnerabilities become so widespread or easy to exploit, mitigation becomes an organization-wide effort.
From hospitals to space, a look at real-time OS ubiquity
One such vulnerability this year was dubbed URGENT/11, a list of 11 RCE vulnerabilities in VxWorks, a real-time OS found in a staggering amount of critical infrastructure devices. When we covered URGENT/11 t in July, no proofs of concept (PoCs) were available. But, by the time the U.S. Food and Drug Administration released a Safety Communication in October, exploit scripts found their way into the public.
The severity of a device takeover through vulnerabilities like URGENT/11 can’t be understated. However, when it comes to URGENT/11 vulnerabilities, CISOs face further challenges. Mitigation depends on equipment manufacturers providing patches through device updates. Tenable released a group of plugins to identify vulnerable assets, and Armis released an URGENT/11 detection tool to help find devices that still need to be addressed.
It came out of nowhere, and then was suddenly everywhere
In addition to the URGENT/11 vulnerabilities, we also saw a critical vBulletin vulnerability (CVE-2019-16759) disclosed in a seclists.org post with no other advisory or public disclosure. The vulnerability itself was a pre-authentication RCE zero day that was exploited almost immediately after it was disclosed by attackers.
The next day, vBulletin released a patch for CVE-2019-16759. However, users in the vBulletin forums reported exploited forums and worked together to repair hijacked forums.
High-criticality vulnerabilities aren’t going away. The time it takes for threat actors to release public exploits for these kinds of vulnerabilities is shortening. As the technology landscape continues to expand, bugs like these will become even more commonplace. As always, we encourage organizations to create rapid detection and mitigation plans, and we’ll continue to provide detections for vulnerable assets as these threats emerge.
Authored by Ryan Seguin, Research Engineer
Let’s speculate, shall we?

As modern central processing units (CPUs) started to plateau in terms of clock rates, their manufacturers looked for other methods to enhance and optimize performance. One of these methods was speculative execution. Rather than the microprocessor sitting idle waiting to receive data, it would speculate what the next requests could be. Unbeknownst to CPU architects, this process would become a fundamental design flaw affecting the security of numerous modern processors spanning varying manufacturers and CPU architectures.
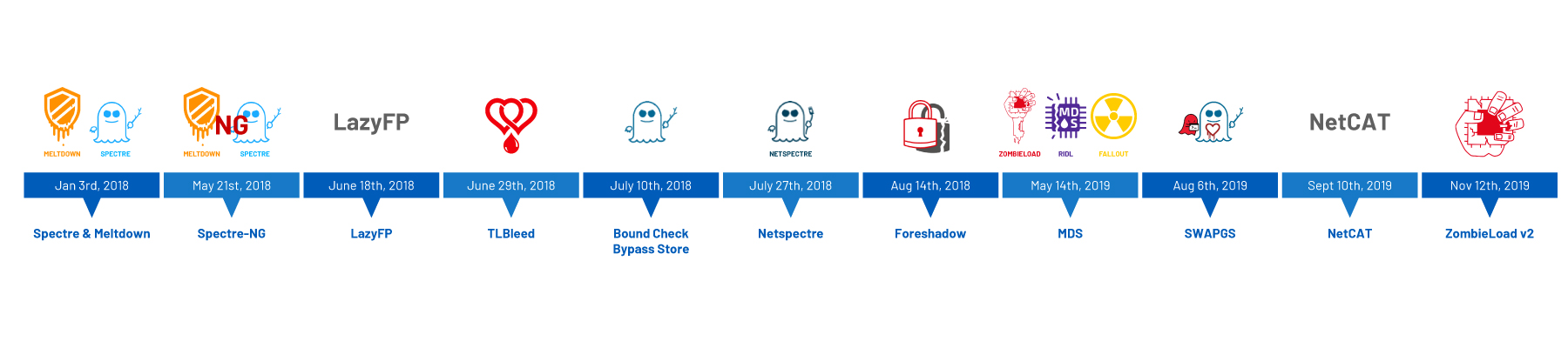
In January 2018, the first in a series of CPU side-channel attacks were announced with the disclosure of Meltdown and Spectre, a pair of critical side-channel vulnerabilities targeting the speculative execution technique in modern CPUs. In July 2019, Bounds Check Bypass Store, a sub-variant of Spectre was disclosed, followed by Netspectre, an implementation of one of the Spectre variants.
Microarchitectural data sampling: Just a taste of what was to come
Among the common cybersecurity predictions for 2019 was the expectation of “More Spectre-Like Flaws.” Just nine months after the Foreshadow vulnerability, this came to pass in May 2019 with the disclosure of a new family of CPU side-channel exploits, Microarchitectural Data Sampling (MDS). MDS included CVE-2018-12126 (microarchitectural store buffer data sampling), CVE-2018-12127 (microarchitectural load port data sampling), CVE-2018-12130 (microarchitectural fill buffer data sampling), and CVE-2019-11091 (microarchitectural data sampling uncacheable memory). While these are speculative execution side-channel vulnerabilities, they differed from Meltdown and Spectre, targeting CPU buffers rather than a CPU’s memory. These flaws were found to only affect Intel CPUs at the time this blog post was created.
The attack for CVE-2018-12127 and CVE-2019-11091 was dubbed RIDL, CVE-2018-12126 as Fallout and CVE-2018-12130 as ZombieLoad, probably three of the more relevant exploits this year. These flaws have been highlighted as being more critical than Meltdown and Spectre, accompanied by not just videos, but also PoC code for RIDL and ZombieLoad.
MDS, as the name would suggest, could result in the “sampling” of data from the previously highlighted buffers before they are written to memory or temporarily loaded into cache by inferring the date using complex side-channel analysis. Where it gets more interesting is, unlike Meltdown and Spectre, the user of the exploits has no direct control over the memory addresses they wish to siphon data from, but rather has to piece it together over time without any context on the collected data.
NetCAT declawed as Intel downplays new side-channel attack
Following MDS was the disclosure of CVE-2019-1125 in August 2019 from Bitdefender security researchers Andrei Lutas and Dan Lutas (no relation), which was also presented at Black Hat USA 2019 and named the “SWAPGS Attack.” What was interesting to see was the efforts continuing from 2018 into 2019 to highlight issues with modern processors. In this instance, 64-bit Intel processors from 2012 onward took advantage of the speculative execution of a specific CPU instruction, SWAPGS, to leak information much like Meltdown and Spectre.
A month later, CVE-2019-11184 was disclosed. Dubbed Network Cache Attack or NetCAT (not to be confused with the popular networking tool netcat), this attack targeted another CPU enhancement technology, Data-Direct I/O Technology (DDIO), which allows the reading and writing to and from fast (last-level) cache in Intel Xeon E5, E7 and SP server-grade processors.
The researchers from VUSec demonstrated in a PoC video that an attacker using this vulnerability could potentially capture keystrokes leaking from a victim’s SSH session. To exploit this flaw, an attacker would need authenticated access to the server and a direct network connection to the system. Intel further downplayed the vulnerability, stating, “In scenarios where Intel DDIO and RDMA are enabled, strong security controls on a secured network are required, as a malicious actor would need to have read/write RDMA access on a target machine using Intel DDIO to use this exploit.”
ZombieLoad v2: Should have gone for the head
At the time of writing this blog post, one more side-channel vulnerability had been made public in 2019 with the disclosure of CVE-2019-11135 in November. Dubbed Zombieload Variant 2 by the researchers, or Transactional Asynchronous Abort (TAA) vulnerability by Intel, this exploit takes advantage of Intel’s Transactional Synchronization Extensions (TSX) Asynchronous Abort operand by either creating a conflicting memory operand or exceeding the amount of read/write data above that of the LLC or L1 cache in a transaction forcing a rollback, leading to leaked data. The researchers updated their original ZombieLoad research paper to reflect this new variant, adding it “works on machines with hardware fixes for Meltdown, which we verified on an i9-9900K and Xeon Gold 5218.”
CPU vulnerabilities: Life finds a way
When it comes to the CPU side-channel vulnerabilities disclosed this year, despite there being PoC code freely available for some, there’s a lack of evidence pointing to exploits in the wild or a full virtual machine escape. CPU architectures are complex, as the attacks require a significant amount of time, skill and code running on the machine, which may also require privilege escalation to execute. One PoC demonstrates this perfectly. RIDL leaking root password hash in a lab environment shows the only user interaction repeatedly trying to authenticate a user with the root password – which took 24 hours to achieve. A CPU in a normal environment or cloud provider would have data moving or being cleared from these buffers and memory locations, making these attacks impractical.
Based on the research seen in 2019, we expect more side-channel CPU-based vulnerabilities to be identified in 2020. It is possible there are newly discovered flaws not yet released due to disclosure policies or embargos, as was the case with ZombieLoad v2. The patches and mitigations released to address these vulnerabilities were designed to reduce the attack surface rather than eliminate it completely. The VERW instruction set to mitigate MDS was an example of this. The release of new CPUs will surely see new improvements and security features. However, as the last two years have shown, these updates are not likely to be perfect as attackers have continued to identify new ways to exploit architectural features and vulnerability mitigations.
Authored by Rody Quinlan, Research Engineer
Ransomware everywhere

In 2019, it seemed as though every week brought new reports of ransomware infections around the world. Ransomware, a type of malicious software (or “malware”), is the most recent incarnation of a type of threat known as scareware. Historically, scareware was designed to trick users into believing their computers were infected with malware, and that they needed to purchase fraudulent security software to address it. Ransomware took scareware to a new, more nefarious level by encrypting files on an infected system and demanding a ransom payment to provide decryption tools. Ransomware has become a money-making success for cybercriminals, and it shows no signs of stopping.
What’s old is new
Ransomware isn’t a new phenomenon. The first recorded instance of ransomware happened in 1989 and was delivered via a floppy disk. However, ransomware has become a useful tool for cybercriminals over the last several years. In 2019, in particular, cybercriminals targeted a variety of industries, such as healthcare, oil and gas, local governments and educational institutions.

Ransomware infections take hold in many ways. In October 2019, the U.S. Federal Bureau of Investigation (FBI) published an alert on high-impact ransomware attacks threatening U.S. businesses and organizations highlighting these three common methods of delivery, which include secondary threats as part of malicious spam emails, targeting RDP flaws and software vulnerabilities, in general. This alert was published as a companion to an alert from three years prior that urged ransomware victims to inform law enforcement.
Zero day exploited in the wild to deliver ransomware
In April 2019, cybercriminals utilized CVE-2019-2725, a deserialization vulnerability in a WebLogic server that can be exploited by a remote, unauthenticated attacker to gain remote code execution. It was used by attackers to distribute ransomware named Sodinokibi. The flaw was fixed by Oracle as part of an out-of-band patch at the end of April, soon after it was publicly disclosed. In June 2019, Oracle released another out-of-band patch for CVE-2019-2729, another deserialization flaw in WebLogic, this time in the XMLDecoder. It appears this flaw was a bypass of CVE-2019-2725 and had also been observed being exploited in the wild.
Patched flaws: A valuable staple for cybercriminals
Not all ransomware attacks rely on zero-day vulnerabilities, although the lack of mitigation or fixes does make vulnerable targets highly useful to cybercriminals. However, patched vulnerabilities are also valuable. For instance, CVE-2019-3396, a path traversal vulnerability in Atlassian’s Confluence Server and Data Center Widget Connector, was used to distribute the GandCrab ransomware. GandCrab was a popular and lucrative ransomware family that shut down its operations in June 2019. So while much attention may be paid to the use of zero-day flaws in ransomware attacks, it’s the unpatched vulnerabilities that pose a greater threat to businesses and organizations around the world.
Ransomware: A neverending threat
In August 2019, Ars Technica reported on a “rash of ransomware” attacks, mostly affecting schools. The article quotes statistics from Armor, which said at the time that there were 149 publicly reported ransomware attacks. The key phrase there is the “publicly reported” part of the equation. While we do not know how many ransomware attacks have gone unreported, it is safe to say many of these attacks go unreported, so the true scope of these ransomware attacks is unknown.
Ransomware is a force to be reckoned with. We expect ransomware to maintain its stronghold as one of the major threats affecting organizations going into 2020, as cybercriminals continue to refine their methods, including equipping themselves with new software vulnerabilities to leverage in their attacks.
Authored by Satnam Narang, Senior Research Engineer
Conclusions
Among the hundreds of stories we’ve observed throughout the last year, our reflections led us to identify four areas of interest in the threat landscape. RDP-centric threats have always been important to monitor, but the revelation of BlueKeep added even more fuel to the fire, sounding an alarm bell on the importance of securing RDP.
While there are tens of thousands of vulnerabilities disclosed each year, a few notable, showstopper vulnerabilities emerged, primarily due to the sheer volume of devices left vulnerable in the case of URGENT/11 or the relative ease of identifying and exploiting flaws like the vBulletin RCE vulnerability.
Over a year after the discovery of Meltdown and Spectre, CPUs remain haunted by speculative execution vulnerabilities, as researchers are keen on discovering side-channel attacks, and in some cases, resurrecting previously disclosed side-channel attacks mere months after they were originally reported.
Finally, ransomware attacks have become more and more pervasive throughout the last year, as attackers continue to enjoy massive success targeting organizations of all shapes and sizes using a number of tactics. This success has emboldened cybercriminals as they look to refine their attacks, from zero-day vulnerabilities to patched flaws, malicious spam emails and weaknesses in Remote Desktop Protocol – and we expect this trend to remain prominent in the coming year.
Get more information
- May 2019 Patch Tuesday: BlueKeep
- August 2019 Patch Tuesday: DejaBlue
- Tenable blog post on URGENT/11
- Tenable blog post on CVE-2019-16759 (vBulletin Vulnerability)
- Tenable blog post on Microarchitectural Data Sampling (MDS) Flaws
- Information on ZombieLoad V2
- Information on the Architecture Affected by MDS
- Article on First Ransomware Event in 1989
- Oracle WebLogic Zero Day Exploited in Wild (CVE-2019-2725)
- Rash of Ransomware Attacks (13 New Victims, Mostly Schools)
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


