Cybersecurity Snapshot: 6 Things That Matter Right Now

Topics that are top of mind for the week ending Sept. 16 | How cybersecurity excellence boosts business | CISOs on a vendor-consolidation campaign | A quick check on converged OT/IT cybersecurity | Guides to help developers beef up on security | And much more!
1. Top-notch cybersecurity yields business gains
Companies that excel at cybersecurity, consumer data protection and AI-based services enjoy stronger customer loyalty and generate higher revenue and profits.
That’s a key finding from a global survey on digital trust of more than 1,300 business leaders and 3,000 consumers conducted by management consulting firm McKinsey & Co.
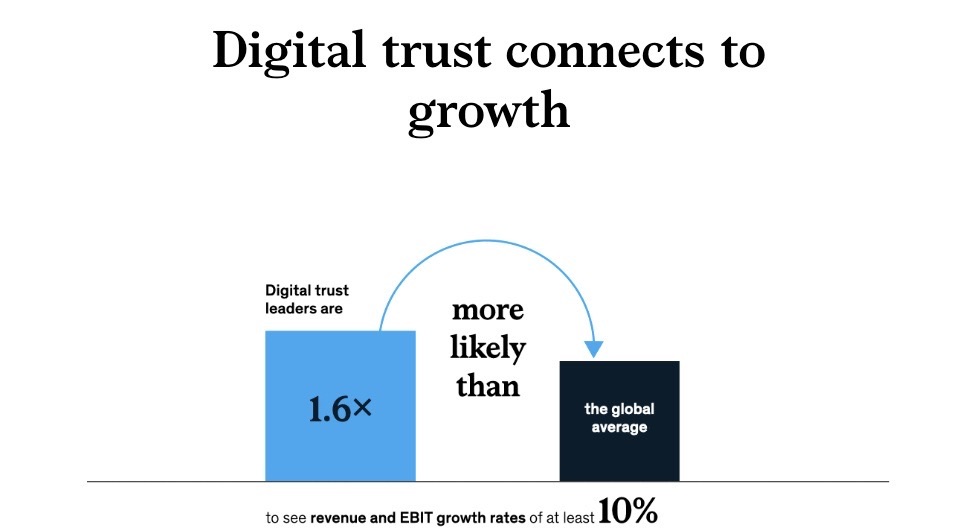
(Source: McKinsey Global Survey on Digital Trust, Sept. 2022)
So how can a company earn a reputation for being digitally trustworthy and ethical, and for having outstanding data-protection practices?
Here are recommendations for joining the exclusive club of digital-trust leaders:
- Set goals for digital-risk management, such as:
- Improving operational performance via use of most accurate AI models
- Gaining a competitive edge through fast recovery from industry disruptions
- Complying with regulations
- Actively mitigate digital risks in areas like:
- Cloud migration and configuration
- Data retention, privacy and quality
- AI modeling and transparency
- Cybersecurity
- Adopt best practices for data privacy, AI ethics and cybersecurity, including:
- Have data-storage and data-access policies
- Assess privacy risks when using external data
- Outline clear standards for AI risk
- Establish consistent processes to identify failures of AI models
- Use automated cybersecurity tools to boost prevention, response and efficiency
- Integrate security considerations when designing new technology
For more information, read the McKinsey & Co. article “Why digital trust truly matters” and view the accompanying infographic "Consumers value digital trust.”
2. Guides to help developers with cybersecurity
As security shifts left in the software development lifecycle, developers have become responsible for security tasks, checks and tests that traditionally fell outside their scope of work. As a result, many developers need security training and education.
Hot off the press come a pair of guides from the Open Source Security Foundation (OpenSSF) aimed at helping developers sharpen their security knowledge. Here’s a sampling of tips from each guide:
- Concise Guide for Developing More Secure Software
- To prevent attackers from hijacking developer accounts – including those with commit or accept privileges – require them to use multifactor authentication (MFA) tokens.
- Take advantage of free courses about secure software development.
- Use a combination of tools in your CI (continuous integration) pipeline for vulnerability detection.
- Before selecting software as a direct dependency, evaluate it, only add it if needed and make sure you retrieve it from the correct repository.
- Use package managers to automatically manage dependencies and enable rapid updates.
- Concise Guide for Evaluating Open Source Software
- Consider if you really need to add a new open source (OSS) dependency or if you can instead use an existing one.
- Ensure you’re evaluating the right version of the OSS component and not a fork created by an attacker.
- Check if the software is being actively maintained. If not, it’s likely to contain security issues.
- Investigate whether the software component was created using secure coding best practices.
- Find out if the software project provides instructions for reporting and disclosing vulnerabilities.
For more information:
- “OpenSSF director warns over secure development” (The Stack)
- “Can 'shift left' in DevOps pipelines go too far?” (TechTarget)
- “How Security Leaders Can Become Dev and Ops Whisperers” (Tenable)
- “How to Boost Shift-Left Security in the SDLC” (DarkReading)
- “Shift left: Still a work in progress” (Tenable)
3. A quick poll on converged IT/OT security
The cybersecurity of converged IT and OT systems used by critical infrastructure providers is very much in the spotlight, so we asked attendees at a recent Tenable webinar a couple of questions about this topic. Check out the responses to our admittedly unscientific poll.
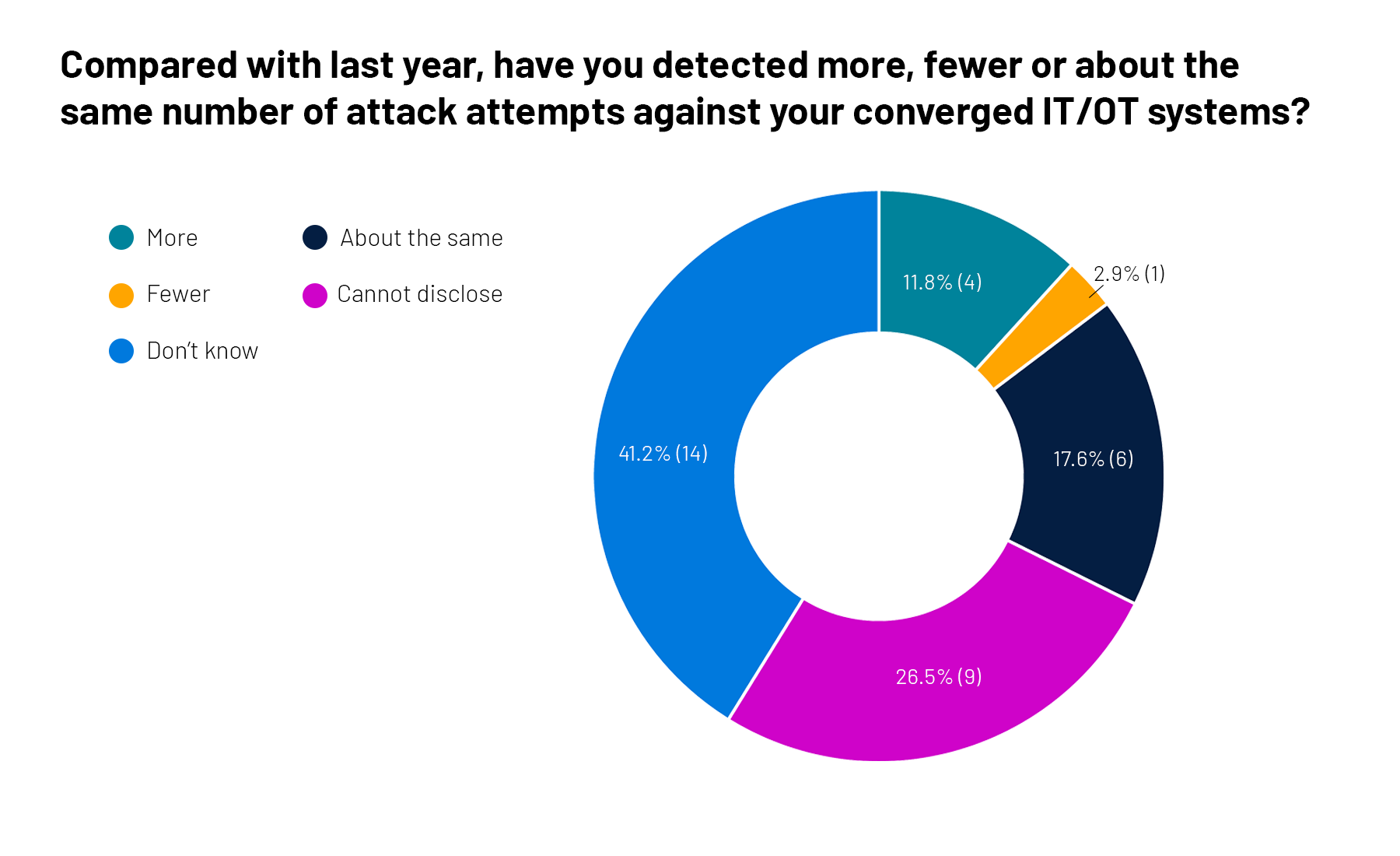
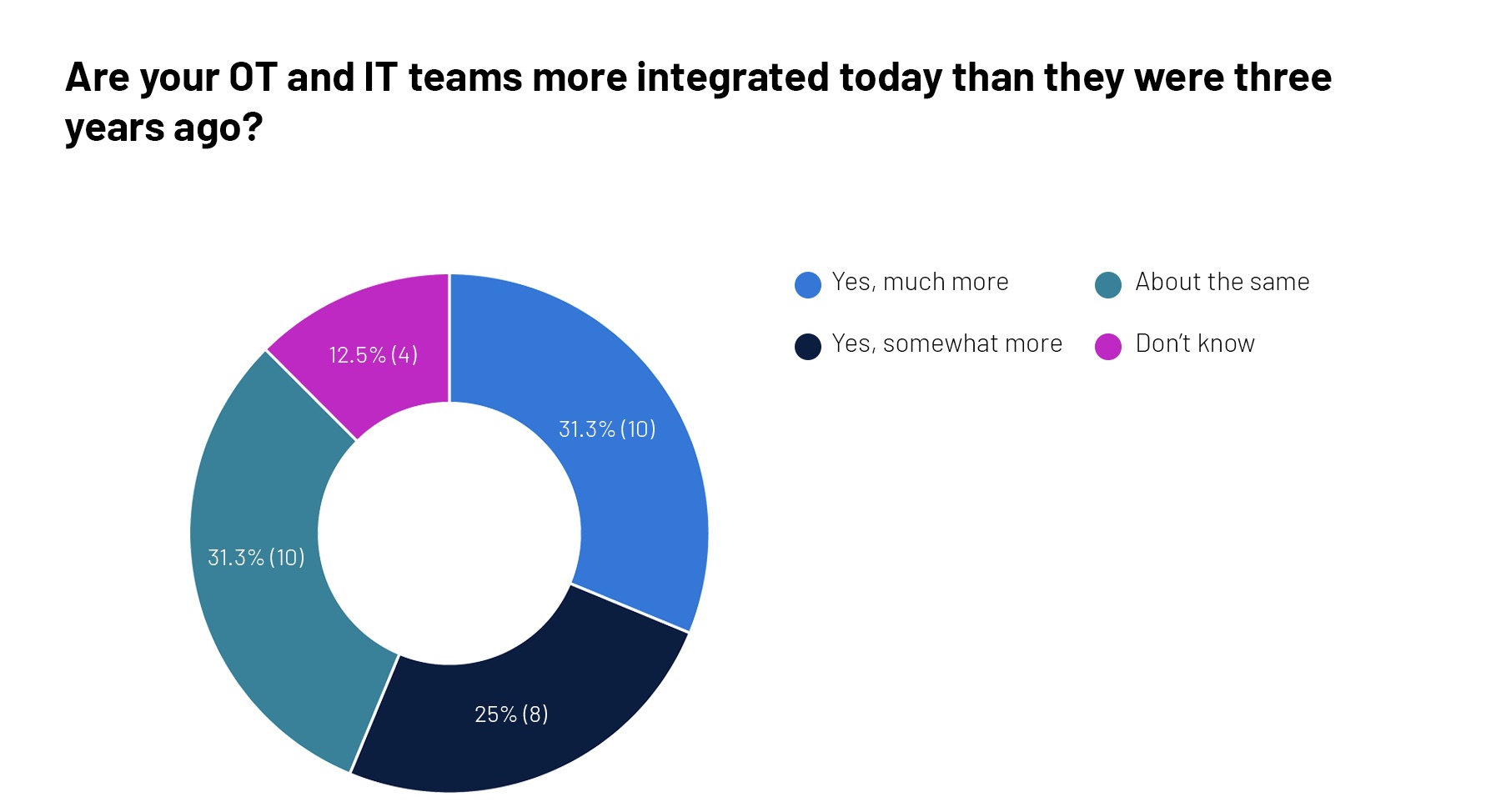
For more information, check out these Tenable resources:
- “IT/OT Convergence: Now Is the Time to Act” (blog)
- “Securing Critical Infrastructure: What We've Learned from Recent Incidents” (blog)
- “How Can We Strengthen the Cybersecurity of Critical Infrastructure?” (blog)
- “The State of OT Security, a Year Since Colonial Pipeline” (podcast)
- “What is operational technology?” (FAQ)
- “The Many Faces of OT Security” (webinar)
4. Survey: CISOs firmly in the business inner circle
After raising their profile by helping their organizations deal with pandemic challenges, such as securing remote work, CISOs have retained their prominence and influence among CxOs and board members.
So says ClubCISO, a non-commercial group of about 600 cybersecurity leaders, in its annual “Information Security Maturity Report” report, which was just released.
“CISOs are now being seen not just as a valuable asset, but as a business driver and solver of challenges,” wrote Stephen Khan, chairman of the ClubCISO Advisory Board.
Other good news for CISOs and their cybersecurity teams:
- Half of CISOs surveyed report their organizations now have a “no blame policy,” up from 27% in 2021 – meaning that cyber incidents are viewed as an organizational problem, not as the exclusive fault of security leaders.
- Two thirds of respondents reported that their budgets increased in 2022, with one-fifth saying it grew 50% or more compared with last year.
- The percentage of respondents reporting that “no material cyber incident occurred” rose to 54% from 28% in 2021.
- Faced with a tough recruitment environment, CISOs are casting a wider net to find good candidates outside of the traditional IT and cybersecurity fields, as this graphic shows:
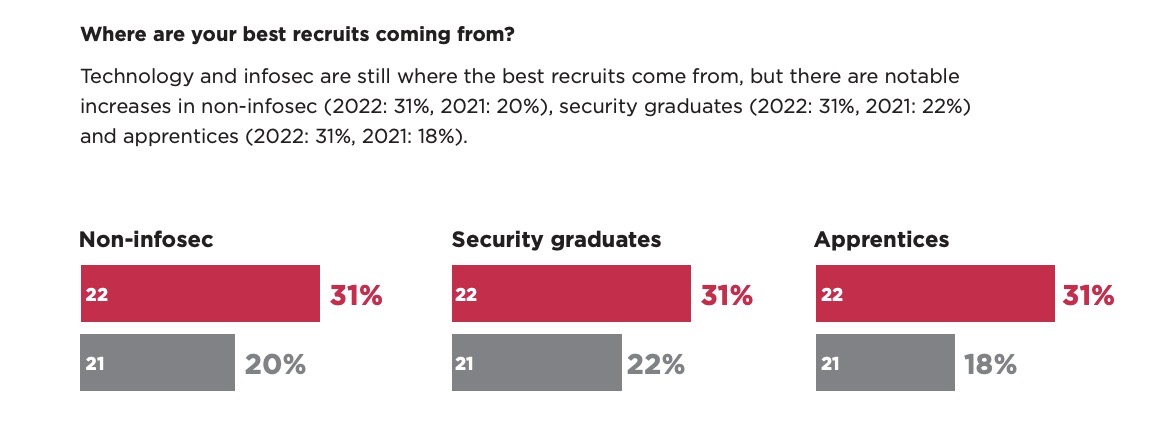
(Source: “Information Security Maturity Report 2022” from ClubCISO, Sept. 2022)
And here are some not-so-encouraging findings:
- 75% of respondents believe industry challenges remain daunting, and are compounded by insufficient staff and the fast pace of business change.
- Cloud security maturity continues to be a tough nut to crack.
- Stress remains a problem for CISOs and their teams – only 11% of respondents believe their organizations are taking effective actions to combat stress.
For more information:
- “Here are what CISOs named as their 20 critical priorities for 2022” (SC Media)
- “CISOs say stress and burnout are their top personal risks” (CNBC)
- “CXO of the Week: Robert Huber, Chief Security Officer, Tenable” (CIOL)
- “The evolving CISO role: What success looks like” (Korn Ferry)
5. Sharp increase in organizations pursuing security vendor consolidation
CISOs want to decrease the number of security vendors their organizations do business.
The percentage of organizations seeking to consolidate their security vendors has increased from 29% in 2020 to 75% this year, according to a Gartner® press release that cites results from a recent survey.
“Security and risk management leaders are increasingly dissatisfied with the operational inefficiencies and the lack of integration of a heterogenous security stack,” said John Watts, VP Analyst at Gartner. “As a result, they are consolidating the number of security vendors they use.”
“The survey was conducted online during March and April 2022 among 418 respondents from North America, Asia Pacific and EMEA. Its objective was to determine organizations’ security vendor consolidation efforts and priorities, and the drivers and benefits of consolidation endeavours.”
“The survey found that already 57% of organizations are working with fewer than 10 vendors for their security needs as they are looking to optimize to fewer vendors in key areas like secure access service edge (SASE) and extended detection and response (XDR) ... The survey found that organizations want to consolidate their security vendors to reduce complexity and improve risk posture, not to save on budget or to improve procurement.”
Gartner Press Release, Gartner Survey Shows 75% of Organizations Are Pursuing Security Vendor Consolidation in 2022
GARTNER is the registered trademark and service mark of Gartner Inc., and/or its affiliates in the U.S. and/or internationally and has been used herein with permission. All rights reserved.
For more information about cybersecurity vendor consolidation, Tenable recommends these resources:
- “Most enterprises looking to consolidate security vendors” (CSO Magazine)
- “Security leaders are increasingly consolidating vendors, says Gartner” (ITWorld Canada)
- “Analyst: CISOs shifting from ‘best of breed’ products to platforms” (Tenable)
- “Thanks to the economy, cybersecurity consolidation is coming” (Protocol)
6. Quick takes
Here’s a roundup of recent patches, incidents and trends to have on your radar screen.
- The White House this week released guidelines designed to ensure that U.S. government agencies use software that was built securely. As Federal Chief Information Security Officer Chris DeRusha said in a statement, the guidance “directs agencies to use only software that complies with secure software development standards, creates a self-attestation form for software producers and agencies, and will allow the federal government to quickly identify security gaps when new vulnerabilities are discovered.” More from TechTarget, FCW, FedScoop, Roll Call and Bloomberg.
- Microsoft addressed 62 CVEs in its September 2022 Patch Tuesday, including five critical flaws.
- Trend Micro patched six vulnerabilities in its Apex One on-prem and SaaS products, one of which has been exploited in the wild.
- A group of global cybersecurity agencies issued a joint advisory about Iranian-government sponsored threat actors that are exploiting vulnerabilities to enable ransomware attacks.
- Apple fixed multiple vulnerabilities in its products, including an actively-exploited zero day bug. More from TechCrunch, the Center for Internet Security, The Register and Help Net Security.
- Adobe patched a raft of vulnerabilities in products including Illustrator, Photoshop and InDesign.
- Spending in cybersecurity insurance is expected to hit $32.6 billion in 2028, representing a compound annual growth rate of almost 19% between 2019 and 2028, according to Research and Markets.
- The FBI is warning about the dangers of unpatched and outdated medical devices.
- Cloud
- Cybersecurity Snapshot
- OT Security
- Research Reports
- Vulnerability Management

