CVE-2021-22986: F5 Patches Several Critical Vulnerabilities in BIG-IP, BIG-IQ

F5 releases patches for multiple vulnerabilities in BIG-IP and BIG-IQ, including a critical remote command execution flaw that does not require authentication and is likely to attract exploits in the near future.
Background
On March 10, F5 published a security advisory for several critical vulnerabilities in BIG-IP and BIG-IQ, a family of hardware and software solutions for application delivery and centralized device management.
Analysis
CVE-2021-22986 is a remote command execution vulnerability in the BIG-IP and BIG-IQ iControl REST API. The API is accessible through the BIG-IP management interface and self IP addresses. An unauthenticated, remote attacker could exploit this vulnerability by sending a specially crafted request to the vulnerable REST interface. Successful exploitation would give an attacker the ability to achieve arbitrary code execution on the vulnerable system and, according to F5, “lead to complete system compromise.” We consider this the most severe of the vulnerabilities patched by F5 because it does not require authentication and its potential for successful exploitation is high.
Traffic Management User Interface (TMUI) related vulnerabilities
In addition to CVE-2021-22986, F5 patched four vulnerabilities within F5’s BIG-IP Traffic Management User Interface (TMUI), also known as the Configuration Utility.
All four vulnerabilities require an attacker to be authenticated to the vulnerable system in order to exploit these flaws. In some instances, specific configurations are required, such as the device running in Appliance mode and/or with the provisioning of the F5 Advanced Web Application Firewall (WAF) or Application Security Manager (ASM).
| CVE | Requirement |
|---|---|
| CVE-2021-22987 | Appliance Mode |
| CVE-2021-22988 | None |
| CVE-2021-22989 | Appliance Mode with Advanced WAF or ASM |
| CVE-2021-22990 | Advanced WAF or ASM |
CVE-2021-22988 is the same vulnerability as CVE-2021-22987, except an enabled Appliance mode is not a requirement for exploitation.
Buffer-overflow vulnerabilities in TMM and Advanced WAF/ASM
CVE-2021-22991 is a buffer-overflow vulnerability in the BIG-IP Traffic Management Microkernel (TMM) due to the improper handling of undisclosed requests with a destination of a virtual server. F5 lists certain configurations of BIG-IP as vulnerable, including:
- BIG-IP Access Policy Manager (APM)
- BIG-IP ASM Risk Engine
- BIG-IP Policy Enforcement Manager (PEM)
- BIG-IP APM Secure Web Gateway (SWG)
- BIG-IP SSL Orchestrator
- BIG-IP System
CVE-2021-22992 is a buffer-overflow vulnerability in the Advanced WAF or ASM virtual server due to the way the Login Page is configured. F5 says that in order for an attacker to exploit this vulnerability they would need to be able to either manipulate server-side HTTP responses or control the back-end web servers. At a minimum, the attacker would be able to cause a denial-of-service (DoS) against the vulnerable device. In some instances, the attacker could gain arbitrary code execution privileges.
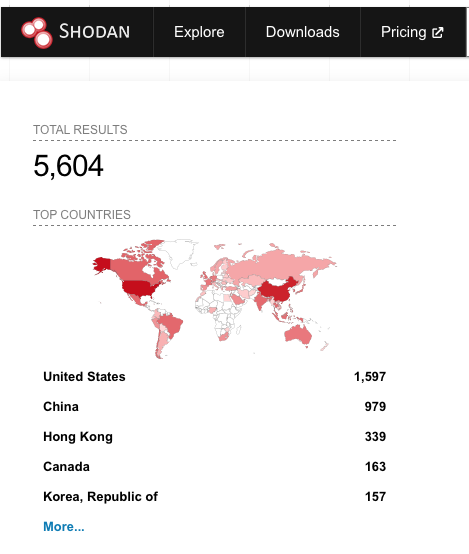
At the time this blog was published, a Shodan query shows that there are over 5,000 BIG-IP devices that are internet-facing, each of which could be potentially vulnerable:
The spectre of CVE-2020-5902 looms large
For practitioners, it's hard not to recall last summer’s F5 advisory for CVE-2020-5902, a critical remote code execution vulnerability in F5 BIG-IP’s TMUI that was quickly exploited in the wild after its disclosure. Because of its severity and overarching impact, CVE-2020-5902 was featured as one of the Top 5 Vulnerabilities in our 2020 Threat Landscape Retrospective report.
We anticipate that CVE-2021-22986 will follow in the footsteps of CVE-2020-5902, as attackers begin to actively scan for and attempt to exploit this flaw in the wild, with a proof-of-concept expected to become available in the near future. The seriousness of these vulnerabilities is further reinforced by the Cybersecurity and Infrastructure Agency’s (CISA) latest advisory encouraging users to apply patches as soon as possible.
Proof of concept
At the time this blog post was published, there were two proofs-of-concept available:
- CVE-2021-22991 (configuration dependent)
- CVE-2021-22992
Solution
F5 released patches to address all seven vulnerabilities. The following table contains the affected versions as well as the fixed versions of BIG-IP and BIG-IQ.
| Affected Versions | Fixed Versions | Products |
|---|---|---|
| 6.0 through 6.1.0 | Migrate to 7.x or 8.0.0 | BIG-IQ (CVE-2021-22986 ONLY) |
| 7.0.0 through 7.0.0.1 | 7.0.0.2 | BIG-IQ (CVE-2021-22986 ONLY) |
| 7.1.0 through 7.1.0.2 | 7.1.0.3 | BIG-IQ (CVE-2021-22986 ONLY) |
| 11.6.1 through 11.6.5.2 | 11.6.5.3 | BIG-IP, BIG-IP Advanced WAF/ASM |
| 12.1.0 through 12.1.5.2 | 12.1.5.3 | BIG-IP, BIG-IP Advanced WAF/ASM |
| 13.1.0 through 13.1.3.5 | 13.1.3.6 | BIG-IP, BIG-IP Advanced WAF/ASM |
| 14.1.0 through 14.1.3.1 | 14.1.4 | BIG-IP, BIG-IP Advanced WAF/ASM |
| 15.1.0 through 15.1.2 | 15.1.2.1 | BIG-IP, BIG-IP Advanced WAF/ASM |
| 16.0.0 through 16.0.1 | 16.0.1.1 | BIG-IP, BIG-IP Advanced WAF/ASM |
All customers of BIG-IP and BIG-IQ are strongly advised to apply these patches as soon as possible.
If applying the patches for CVE-2021-22986 is currently not feasible, F5 has provided temporary mitigations that can be applied to restrict access to the iControl REST interface either via blocking access through self IP addresses or blocking access through the management interface. Please note these mitigations should only be used temporarily until you can apply the provided patches.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities can be found here. To scan for vulnerable devices, users are required to enable the “Show potential false alarms” setting, also known as “paranoid mode,” in their scan policy.
We also recommend enabling only these specific plugins in a paranoid scan. Scan policies configured to have all plugins enabled will see an increase in the number of triggers, as it will include all paranoid plugins during the scan.
Enabling Paranoid Mode
To enable this setting for Nessus or Tenable.io users:
- Click Assessment > General > Accuracy
- Enable the “Show potential false alarms” option
To enable this setting for Tenable.sc users:
- Click Assessment > Accuracy
- Click the drop-down box and select “Paranoid (more false alarms)”
Get more information
- F5 Security Advisory for Critical Vulnerabilities in BIG-IP and BIG-IQ (March 2021)
- F5 Security Advisory for CVE-2021-22986
- Tenable Blog Post for CVE-2020-5902 (July 2020)
- Shodan Query for F5 BIG-IP Devices
- CISA F5 Security Advisory
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management

