Exposure Management Vs. Siloed Security Tools: 4 Ways to Supercharge Your Strategy — and Your Career

Adding more tools to your vulnerability management program only adds noise and expense without solving your biggest challenges. With an exposure management platform, you can address your current needs without straining your budget — and boost your career by demonstrating your skills in the process.
Key takeaways:
- Not every organization has a top-down exposure management initiative, but you can still take practical steps on your journey and help your career in the process by prioritizing four strategic challenges most vulnerability management programs face today: tool sprawl, external blind spots, risk from rapid tech adoption, and alert fatigue.
- Exposure management platforms address all four of these challenges in a more cost-effective and scalable way than point solutions, while also supporting longer-term strategic objectives. Any one of these is a good place to start, allowing you to demonstrate your skills in the process.
- By conducting a proof-of-value (PoV) that aligns with your priorities, you’ll demonstrate how an exposure management platform unifies data and context across security silos for more effective prioritization, mobilization, and reporting, without the sprawl and limitations of point tools.
Budget constraints may keep you stuck in a cycle of purchasing point tools to solve your vulnerability management challenges. But adding more siloed tools just adds more noise without giving you the context you need to proactively reduce risk.
Moving to an exposure management platform to meet your vulnerability management needs solves the challenges you face today while also achieving cost efficiencies. Not only will you avoid adding new lines to your vulnerability management budget, you’ll be able to accomplish things that are simply impossible to achieve with siloed tools.

In a previous Exposure Management Academy blog, we explored how transitioning from traditional vulnerability management to modern exposure management can advance your security program and boost your career. Now let’s talk about how to make that shift real.
Every organization is different, and there’s no one-size-fits-all approach to moving from siloed tools to an exposure management platform. Broadly speaking, we see two types of organizations: those whose leadership fully embraces proactive cybersecurity and the move to exposure management; and those whose leadership is focused on other priorities, leaving you on your own to improve your vulnerability management practice.
Take the path that’s right for you
Here’s some practical guidance depending on which organizational category you find yourself:
- Top-down: If exposure management is already on your leadership’s radar, our Exposure Management Resource Center provides everything you need to support conversations with leaders, including analyst research, expert guidance, and real-world customer examples. In this blog, you’ll find additional ideas to demonstrate the value of exposure management.
- Ground-up: If your organization’s leadership has other near-term priorities, you can still make meaningful progress toward exposure management by aligning your efforts to the challenges your team is already trying to solve. The four challenges discussed in this blog offer opportunities for you to try out exposure management and demonstrate its value in addressing the struggles you and your colleagues face.
Tip: Instead of continuing to throw more point tools at siloed problems, you can use a holistic exposure management platform to reach your objectives faster. An exposure management platform delivers shared visibility and context across domains earlier in the maturity journey — streamlining communication, processes, and decision-making as your program grows.
Exposure management isn’t a rip-and-replace of your vulnerability management program. It’s a natural and necessary evolution.
In guiding vulnerability management clients through their exposure management journey, we consistently see four major challenges rise to the top:
- Conquering tool, data, and vendor sprawl
- Eliminating external attack surface blind spots
- Managing growing risk from rapid tech adoption
- Reducing alert fatigue that leads to staff churn
Let’s explore each of these challenges and how an exposure management platform helps you solve them with greater speed, clarity, and confidence. We offer four steps for conducting a proof-of-value (PoV) to address these challenges. If budget is a concern, keep in mind that an exposure management platform, such as Tenable One, can save up to 50% in licensing costs compared with an array of siloed security tools, freeing funds to focus on other priorities.
Challenge: Conquering tool, data, and vendor sprawl
A decade ago, vulnerabilities were managed exclusively within vulnerability management tools. Today, it’s not uncommon for cloud-native application protection platforms (CNAPPs), container security, operational technology (OT), and Internet of Things (IoT) security to also detect and manage CVEs for their respective environments. In larger organizations, there may be multiple vulnerability management teams, each with its own set of tools and vendors, which can compound the tool sprawl.
With assets and findings spread across so many tools, it can be difficult and time-consuming for vulnerability management teams to aggregate the data, deduplicate it, and align it to business units or specific regulatory requirements for reporting. Vulnerability analysts can spend several days a month doing this work manually, consuming valuable time.
Unite your visibility
Exposure management platforms provide connectors to common tools and vendors. These platforms aggregate, deduplicate, and normalize asset and CVE data from your existing tools in a single unified data store.
With a unified inventory and visualization of findings, you’ll be able to do more with that data, including leveraging consistent scoring and prioritization of findings, tracking remediation, and holistic reporting. With just a click of a button, you’ll be able to generate cohesive reporting for business lines, leadership, and regulators — eliminating time spent in spreadsheets.

Challenge: Eliminating external attack surface blind spots
Traditional vulnerability management is limited by what it can see — typically, known assets inside the organization. The problem is, attackers don’t work that way. They think outside-in, looking for the low-hanging fruit on your external attack surface, such as exposed devices, unpatched web apps, and misconfigurations you didn’t even know existed.
Gain the attacker's perspective
Unlike standalone external attack surface management (EASM) or web application scanning tools you’d purchase from individual vendors to gain an outside-in perspective, exposure management platforms offer outside-in visibility more cost-effectively, with added benefits. Platform sensors detect and integrate data into a common data model, along with asset relationships that let you visualize all your assets and findings together.
More importantly, with such mapping you can identify toxic risk combinations across silos. For example, you might identify an open port on an external-facing asset that exposes a lower-priority vulnerability on a critical internal system, like a mail server. This external exposure, when combined with an unpatched CVE, creates an entry point attackers could exploit. You can now justify patching that specific vulnerability — not because of its CVSS score, but because it poses real business exposure.

Challenge: Managing growing risk from rapid tech adoption
Emerging technologies like cloud, containers, OT, IoT, and AI have dramatically expanded the attack surface. Traditional vulnerability management tools weren’t designed to protect these dynamic, interconnected environments. As a result, vulnerability management teams struggle with blind spots — such as shadow IT from multi-cloud sprawl, insecure devices resulting from IT/OT convergence, or misconfigured AI deployments that expose sensitive information. Managing this risk requires new levels of visibility, specialized tooling, and cross-domain context that traditional vulnerability management simply can’t deliver.
Embrace innovation, securely
Exposure management platforms let you incrementally extend visibility into emerging technologies, with purpose-built sensors, without disrupting your workflows. For example, you can identify vulnerabilities across mixed cloud environments and in containers. As you evolve your program over time, you’ll be able to detect other classes of risk beyond CVEs, such as cloud misconfigurations. Your business will benefit by embracing new technologies at speed, with license savings and process efficiencies.

Challenge: Reducing alert fatigue that leads to staff churn
Accelerated growth in the attack surface and new CVEs means that even with advanced scoring, like Tenable's Vulnerability Priority Rating (VPR) or the Exploit Prediction Scoring System (EPSS), teams can be overwhelmed by the sheer volume of alerts. Alert fatigue inevitably leads to burnout and turnover. This is where identity context can play a critical role. Identity permissions, whether human or machine, enable attackers to move laterally and achieve their goals. Traditional vulnerability management lacks an understanding of asset, identity, and risk relationships needed for more effective prioritization.
Prioritize findings with rich identity and business context
Exposure management platforms detect human and machine identities and permissions and incorporate this context in a single data model. This context enables advanced exposure analysis:
- Highly privileged identities — human or machine — can be classified as crown jewels, receiving a high asset criticality score. This means a vulnerability on a highly privileged machine will have a higher asset exposure score than a less critical asset, allowing prioritized remediation.
- Policies can look for toxic risk combinations, such as known exploited vulnerabilities (KEV) on devices that also have an administrator account logged in. If exploited, this vulnerability can compromise the administrator account.
- Mapping of asset, identity, and risk relationships allows visualization of attack paths leading to the crown jewel assets that business units care about. Choke point identification specifies which finding to address first, along with step-by-step guidance for remediation.
These powerful use cases allow you to build rapport with business units by focusing on clear, business-impacting issues. This single step transforms your role from a vulnerability analyst to a strategic business partner. It’s also at the core of the career boost we discussed last time.

4 steps to build a strategic PoV for exposure management: Think beyond silo features
Even without a top-down exposure management mandate, you can begin shifting from vulnerability management to exposure management by running a focused PoV. The goal is simple: show that an exposure management platform solves today’s vulnerability management problems faster, with richer context, and at lower cost than continuing to buy siloed point tools.
1. Prioritize the four biggest challenges
Start with the outcomes you want. Rank the four key vulnerability management challenges — tool sprawl, external blind spots, rapid tech adoption, and alert fatigue — based on urgency and alignment to your organization’s priorities. This gives you a clear starting point and a defensible “why now” narrative. Define realistic timelines for each milestone. Factor in budget availability to help justify platform decisions over incremental point products.
2. Define the PoV scope
Create a short list of vendors that can support your priority use case. Document the capabilities required to solve your top challenge, and include value-add exposure management capabilities that strengthen the outcome. For example, if you need cloud visibility, start with cloud-specific requirements but extend the scope to include strategic, longer-term requirements a platform can offer (see visual below).
3. Compare point tools vs. platform side-by-side
Run PoVs with your top vendor candidates. For each requirement, evaluate how their point products perform versus how the exposure management platform performs. Keep the comparison practical, focusing on speed, context, completeness, usability, and cost.
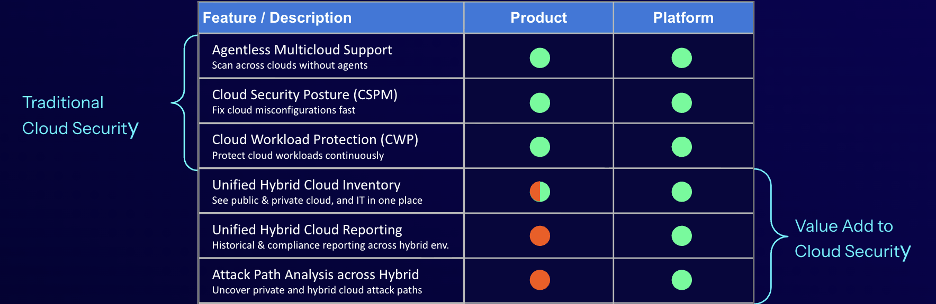
4. Think beyond security tool features: Consider total value and cost benefits
When weighing a point security product against an exposure management platform, consider how the choice aligns with broader organizational priorities. These factors often create leverage:
- Return on existing tool investments: Large organizations often have cloud, external attack surface management (EASM), or identity tools already deployed outside the vulnerability management team. A platform can unify and reuse those investments rather than duplicate them, and at a fraction of the cost of a new tool.
- Volume-based pricing advantages: Standalone tools are typically more expensive on a per-asset basis. For example, Tenable One platform customers often realize lower per-asset costs by extending existing vulnerability management coverage with attack surface and other domain coverage through the platform.
- Vendor consolidation: Many CISOs are driving efforts to consolidate vendors. If existing point tools are underperforming or overlap in terms of asset coverage and costs, a platform can replace them, eliminate costly overlap, and greatly simplify procurement with consistent pricing and fewer vendors. Tenable customers often see up to 50% license savings by selectively consolidating competitive point tools.
- Time to value: Platform pricing and shared capabilities may allow you to accelerate work on multiple challenges using the same budget. For instance, instead of only addressing the external attack surface, you may also bring web application scanning into scope without increasing spend.
Start your exposure management evolution today
Exposure management isn’t a rip-and-replace of your vulnerability management program. It’s a natural and necessary evolution. More importantly, it will deliver more value to you and your organization by:
- Unifying visibility, insight, and action for improved efficiency
- Improving your return on existing tools and staff
- Selectively consolidating expensive, redundant tools for lower costs
- Achieving organizational and personal goals faster
By adopting an exposure management platform rather than adding more siloed tools, you can chart a clear roadmap to overcome your critical challenges today while building a holistic exposure management program that supports tomorrow’s requirements.
Learn more
- Evolve now. Build a unified exposure management program that reduces real risk and demonstrates clear value. See how.
- Exposure Management



