by David Schwalenberg
May 16, 2017
Managing inventory and monitoring changes are necessary tasks for securing a network. Without proper management, transient assets such as laptops, mobile phones and virtualized systems could be missed. Unauthorized software and rogue devices could be allowed to infiltrate the network, bringing new vulnerabilities and increasing the risk of dangerous network attacks and compromise of sensitive data. The financial industry is highly targeted by cyber attacks, emphasizing the urgent need for robust cyber security and increased network resilience.
In 2016, due to the increasing use of information technology by banks and their customers, and the increase in cyber attacks against the financial sector, the Reserve Bank of India (RBI) provided guidelines in the area of cyber security to banks. The guidelines document, Cyber Security Framework in Banks, includes an Annex detailing minimum baseline requirements for network security and resilience. These requirements cover such areas as inventory management, secure configuration, patch management, access control and advanced real-time threat defense.
Tenable's Tenable.sc Continuous View® (Tenable.sc CV™) offers several specialized dashboards that can help banks comply with the requirements specified in the RBI document. This dashboard assists in the area of inventory management, and aligns with baseline controls 1 (Inventory Management) and 2 (Prevent Execution of Unauthorised Software) in Annex 1, as well as aspects of other baseline controls that mention identifying mobile devices and controlling software installation.
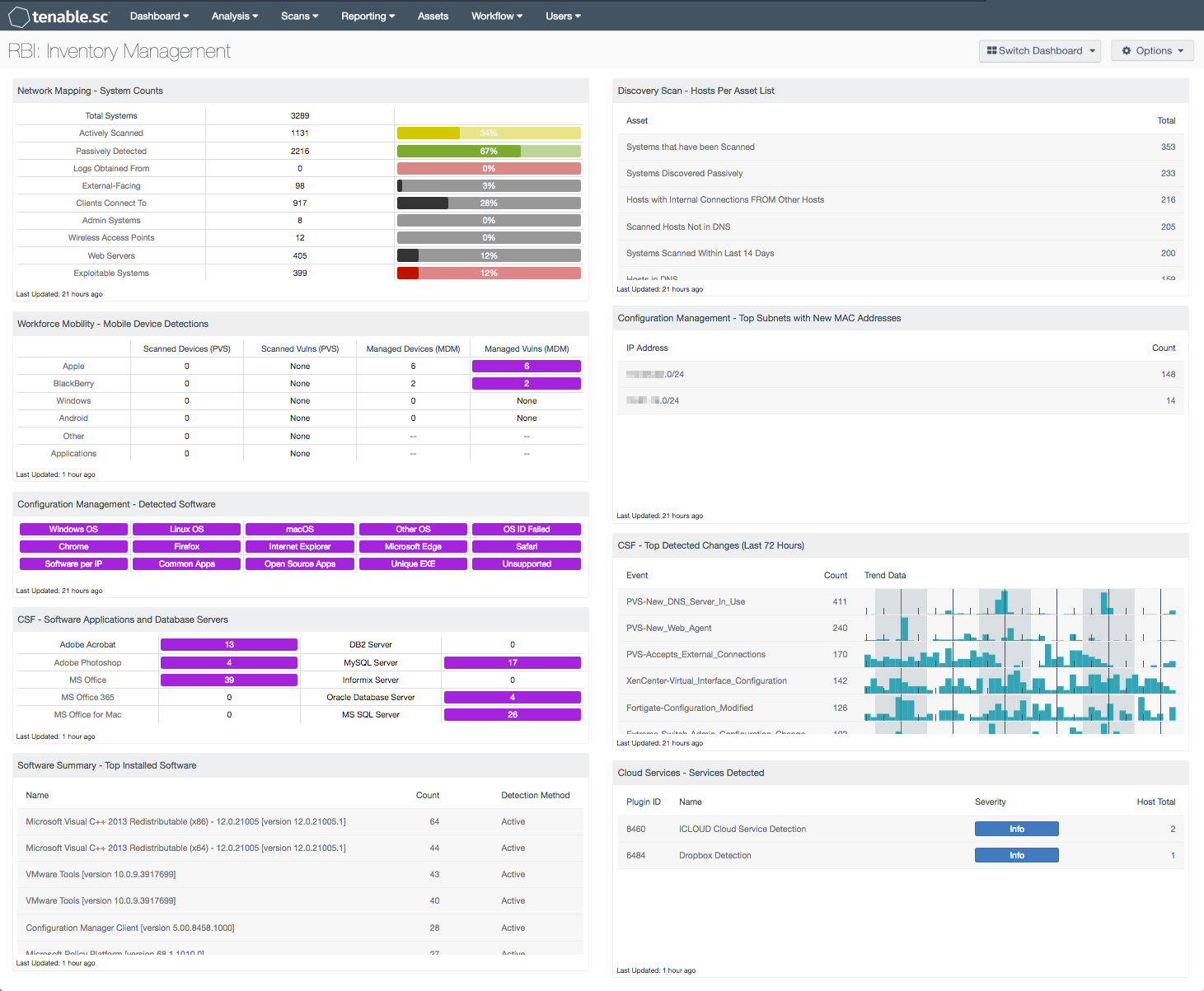
This dashboard provides an overview of system counts, mobile devices, new MAC addresses, installed software, cloud service use and changes detected throughout the network. Having an accurate and up-to-date count of existing assets on the network will assist analysts in preventing unauthorized devices from connecting to the network. Monitoring asset changes will also help security teams identify blind spots that may have been previously overlooked.
Organizations will also be able to keep track of operating system and software deployments using this dashboard. This information will enable organizations to gain control over software licenses and reduce unnecessary costs. Information on software installations can highlight unauthorized and unsupported software running on network assets. Monitoring changes across devices and software can help to identify and prevent unauthorized modifications that could negatively impact critical systems. Having accurate inventory information assists an organization in securing the network and complying with the RBI requirements.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.4.5
- Nessus 8.5.0
- LCE 6.0.0
- NNM 5.9.0
- Mobile data
Tenable's Tenable.sc CV is the market-defining continuous network monitoring solution, and can assist in securing an organization’s internal network. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities and new regulatory compliance data. Active scanning periodically examines systems to determine vulnerabilities and compliance concerns. Agent scanning enables scanning and detection of transient and isolated devices. Passive listening provides real-time discovery of devices, operating systems, browsers and desktop applications. Host data and data from other security products is analyzed to monitor the network for changes to devices and software. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to secure and protect assets within the network.
The following components are included in this dashboard:
- Network Mapping - System Counts: This component presents the counts of systems detected on the network in various categories.
- Workforce Mobility - Mobile Device Detections: This component presents counts of mobile devices and associated vulnerabilities detected passively by the Tenable Nessus Network Monitor (NNM) and via Mobile Device Management (MDM) systems.
- Configuration Management - Detected Software: This matrix presents indicators that detect operating systems, browsers, unsupported and other software installations on systems within a network.
- CSF - Software Applications and Database Servers: This component displays a matrix of detected software programs and database servers that are commonly used within organizations.
- Software Summary - Top Installed Software: This table displays a list of the software currently discovered on the network.
- Discovery Scan - Hosts Per Asset List: This table displays counts of live hosts within defined Tenable.sc asset lists.
- Configuration Management - Top Subnets With New MAC Addresses: This component presents a summary of newly detected MAC addresses per subnet over the last 72 hours.
- CSF - Top Detected Changes (Last 72 Hours): This table displays the top change events detected on the network in the last 72 hours.
- Cloud Services - Services Detected: This table presents a list of passive detections of network interactions with cloud services.