by Stephanie Dunn
May 2, 2017
Maintaining data privacy and security is a critical aspect of any comprehensive security program. Some organizations may not be completely aware of the types of data stored on the network and who may have access. Additionally, some may not have adequate encryption mechanisms in place to protect and ensure data integrity. Failure to detect any unknown or unauthorized changes made on the network can result in misconfigurations of critical systems, data leakage and compromised assets.
The Data Privacy Act of 2012 was published by the Republic of Philippines to assist government and private sector organizations with monitoring data and ensuring compliance with international standards on data protection. Integrating these controls will assist organizations in safeguarding their computer networks, and aid in maintaining the availability, integrity and confidentiality of data. Data presented within this dashboard aligns with Rule VI and Rule VII of the Data Privacy Act, which supports data privacy and security, and provides guidelines for technical security measures. This dashboard aligns with the following controls:
- Section 25 advises on maintaining the availability, integrity and confidentiality of personal data, and protecting data against any accidental or unlawful destruction, alteration, disclosure or other unlawful processing.
- Section 28(B) recommends implementing safeguards to protect computers against accidental or unauthorized usage, and anything that will affect data integrity, system availability and unauthorized access on a network.
- Section 28(D) focuses on continuous monitoring to detect data breaches, and taking corrective action to mitigate vulnerabilities that can lead to a data breach.• Section 28(G) advises ensuring that data remains encrypted while in-transit, at-rest and implementing other security measures to control and limit access.
- Section 31A(3) recommends implementing sufficient physical and technical security measures that will protect sensitive data in accordance with data privacy practices and standards recognized by the information technology industry.
This dashboard will assist organizations in highlighting network changes, file integrity or data leakage issues, and monitoring encrypted network traffic. Monitoring changes on infrastructure devices, user changes, software installations and new logins can assist analysts in detecting misconfigurations and/or potentially unauthorized activity. Information collected from Tenable.sc highlights systems with file integrity and cryptographic issues that need to be addressed by security teams. Systems using weak encryption algorithms and vulnerabilities that could result in data leakage are also presented. Attackers often use well-known ports to disguise malicious activity within encrypted traffic. Data presented within this dashboard will highlight both inbound, internal and outbound encrypted network sessions, as well as malicious traffic, encrypted attachments and intrusion attempts from devices and services on the network.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Tenable.sc 5.4.5
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
- Compliance Data
Tenable's Tenable.sc Continuous View (Tenable.sc CV) provides continuous network monitoring, vulnerability identification, risk reduction and compliance monitoring. Tenable.sc is continuously updated with information about advanced threats and zero-day vulnerabilities and new types of regulatory compliance configuration audits. Active scanning periodically examines devices to determine vulnerabilities and compliance concerns. Passive listening collects data to continuously detect devices and monitor network connections and activity. Host data and data from other security investments is analyzed to monitor encrypted network traffic. Tenable.sc CV provides an organization with the most comprehensive view of the network, and the intelligence needed to protect and ensure overall data integrity.
The following components are included within this dashboard:
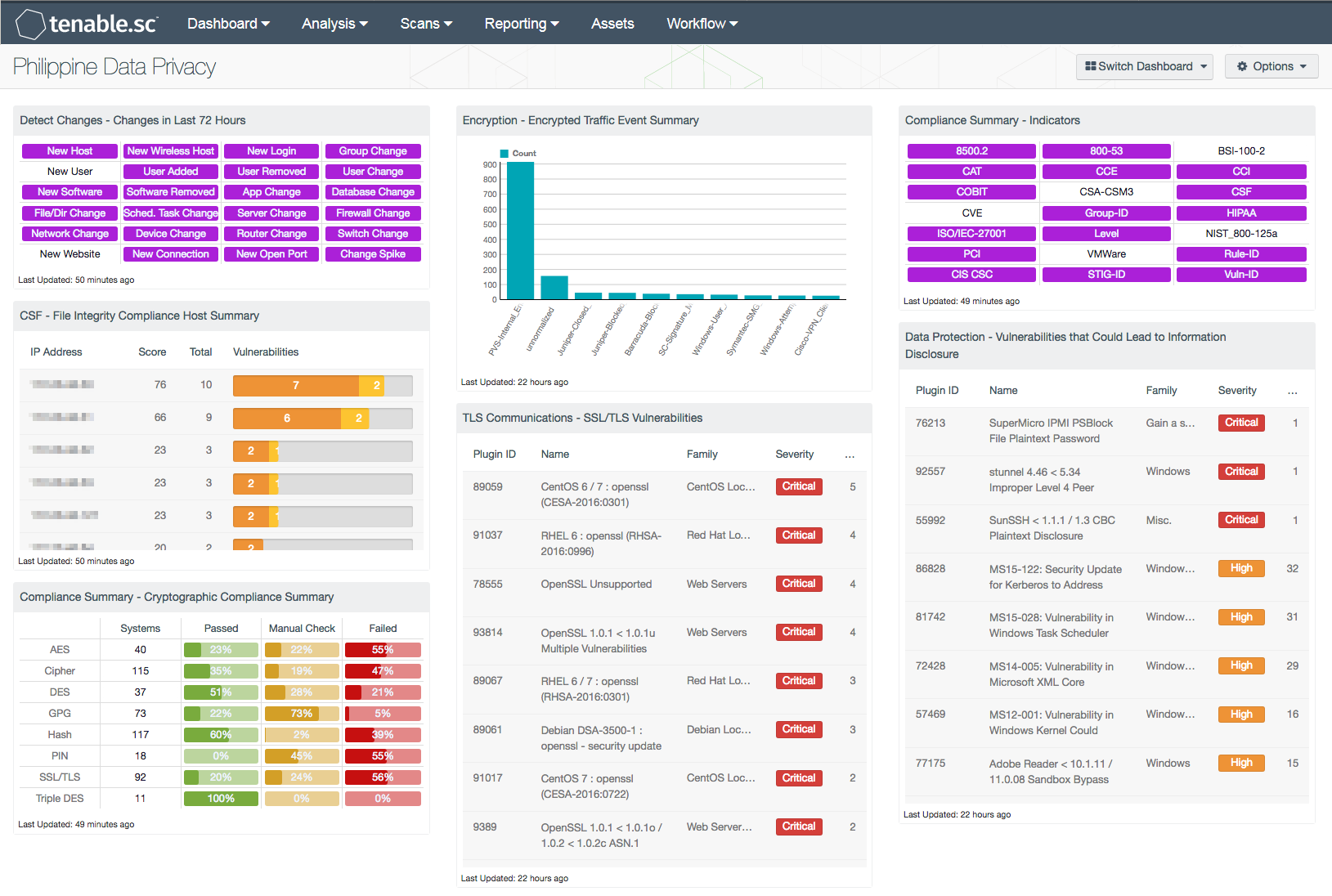
- Detect Changes – Changes in Last 72 Hours: This component assists in maintaining up-to-date inventories and detecting changes. The matrix presents indicators for network changes detected in the last 72 hours. Each indicator is based on one or more Tenable Log Correlation Engine (LCE) events; the indicator is highlighted purple if the event occurred in the last 72 hours.
- CSF - File Integrity Compliance Host Summary: This table presents a list of top hosts for which File Integrity compliance checks have been detected. Many organizations are required to follow compliance regulations such as PCI DSS and HIPAA, which require file integrity monitoring as a part of compliance objectives. This table uses the “File Integrity” plugin name and “Compliance” plugin type to perform file integrity compliance checks. Data within this table is sorted by the highest total of hosts at the top, and includes the IP address, score, total number of checks detected and a vulnerability bar for each host. By changing the tool to Vulnerability Summary, the analysts can obtain additional information on the detected vulnerability.
- Compliance Summary - Cryptographic Compliance Summary: This matrix displays a summary of cryptographic-based compliance issues discovered within the organization. For each cryptographic keyword presented, a count of systems affected by the compliance issue, and the ratio of identified to total vulnerabilities are included. High severity denotes checks that have failed to meet the compliance threshold. Medium severity shows checks that need to be manually reviewed to assess their compliance state. Informational severity status is used for checks that have passed the compliance check. Information presented within this component can be modified to include specific or additional cryptographic-based compliance issues per organizational requirements.
- Encryption – Encrypted Traffic Event Summary: The Encrypted Traffic Events chart presents an overview of encrypted session activity within the 72 hours. Encrypted events and activity within the syslog will highlight devices or applications processing encrypted traffic. Information presented within this component can alert the analyst to encrypted network traffic, encrypted email attachments, anti-virus events, and more. This component can be modified to include additional or specific events based on organizational requirements.
- TLS Communications – SSL/TLS Vulnerabilities: The SSL/TLS Vulnerabilities component displays a list of SSL and TLS-based vulnerabilities on the network. The table is filtered by SSL and TLS-based plugin names, and is sorted by severity. Both Nessus and NNM will scan systems that are vulnerable to DROWN, POODLE, Logjam, and Heartbleed attacks that exploit weaknesses in older SSL versions. This will allow for both analysts and security teams to identify web applications and enterprise software with SSL/TLS vulnerabilities, expired certificates, self-signed certificates, and more.
- Compliance Summary - Indicators: This component provides an indicator for the supported compliance standards. Each indicator will provide an easy mechanism to see a list of hosts applicable to each standard. This component will return a list of hosts regardless of whether or not the audit check passed or failed. The indicator will turn purple when a match is found.
- Data Protection - Vulnerabilities that Could Lead to Information Disclosure: This component presents a list of actively and passively detected vulnerabilities that could lead to data disclosure. Vulnerabilities at all severity levels except Informational are included. The keywords cover disclosures, cryptographic issues, man-in-the-middle vulnerabilities, and weak authentication concerns. Clicking on the Browse Component Data icon will bring up the vulnerability analysis screen to allow further investigation of the vulnerabilities. In the analysis screen, setting the tool to IP Summary will display the systems on which the vulnerabilities are present. This component is used to strengthen security controls and better protect data.