CVE-2020-6925, CVE-2020-6926, CVE-2020-6927: Multiple Vulnerabilities in HP Device Manager

Vulnerabilities in HP Device Manager could be chained to achieve unauthenticated remote command execution.
Background
On September 25, HP published a security bulletin to address multiple vulnerabilities in HP Device Manager, software that’s used to remotely manage HP Thin Clients. The vulnerabilities were disclosed to HP by security researcher Nick Bloor. As part of a Twitter thread, Bloor warned that a combination of these vulnerabilities would result in “unauthenticated remote command execution as SYSTEM.” On October 5, Bloor published a blog post detailing his findings.
Hey @TheRegister, a HP developer put a backdoor database user account in HP Device Manager which is used to manage HP thin clients. Combined with some other vulnerabilities this leads to unauthenticated remote command execution as SYSTEM.
— Nicky Bloor (@nickstadb) September 29, 2020
There were three vulnerabilities in HP’s security bulletin and the table below lists the assigned CVE identifiers and CVSSv3 scores:
| CVE Identifier | CVSSv3 |
|---|---|
| CVE-2020-6925 | 7.0 |
| CVE-2020-6926 | 9.9 |
| CVE-2020-6927 | 8.0 |
Analysis
CVE-2020-6925 is a weak cipher implementation vulnerability, which means dictionary attacks may be possible against locally managed accounts in the HP Device Manager. HP notes that this vulnerability is mitigated by the use of Active Directory authenticated accounts.
According to Bloor’s research, the HP Device Manager server’s Remote Method Invocation (RMI) service method, ServGetUsers(), will return a list of accounts and their associated hashed passwords (using MD5 hashing algorithm). Bloor states that these password hashes were “salted using a static hard-coded salt.”
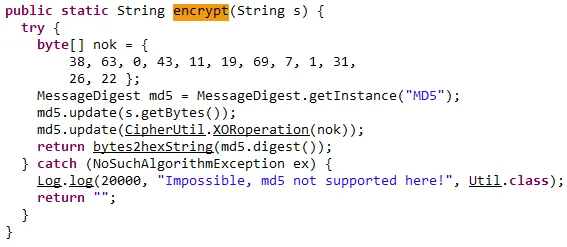
Example of the weak cipher implementation using MD5 encryption and static salt Image Source: Nick Bloor’s blog post
MD5 hashes have been deemed unsuitable for years. Since 2009, the CERT Coordination Center has advised against the use of MD5, saying it “should be considered cryptographically broken and unsuitable for further use.”
CVE-2020-6926 is an RMI vulnerability that would allow a remote, unauthenticated attacker to gain access to resources in the HP Device Manager. This vulnerability received a CVSSv3 score of 9.9, the highest of the three vulnerabilities disclosed.
Bloor found that he could inject database queries into the RMI service. Specifically, he identified that the HP Device Manager uses Hibernate, one of several object-relational mapping frameworks. Hibernate offers its own query language, known as HQL. Bloor managed to smuggle Postgres injection payloads through HQL in order to overwrite the Postgres host-based authentication configuration file (pg_hba.conf) to enable remote authentication. By default, remote authentication is disabled.
CVE-2020-6927 is an elevation of privilege vulnerability in HP Device Manager. According to HP, this vulnerability is mitigated when the integrated Postgres service has not been installed and with the use of an external database, such as Microsoft SQL Server.
During his research, Bloor discovered in the HP Device Manager database (hpdmdb) the presence of a backdoor user account, dm_postgres, which has superuser privileges.
PSA: Do you or your clients use HP thin clients and manage them with HP Device Manager? I strongly advise you, firstly, to log on to all servers running HP Device Manager and set a strong password for the "dm_postgres" user of the "hpdmdb" Postgres database on TCP port 40006 1/4
— Nicky Bloor (@nickstadb) September 29, 2020
He was able to crack the password for the dm_postgres user account, which turned out to be a single space (“ “) character.
Chaining vulnerabilities to achieve remote command execution as SYSTEM
For full exploitation, an attacker would need to chain both CVE-2020-6926 and CVE-2020-6927 together.
Utilizing CVE-2020-6926, an attacker can enable remote authentication on the vulnerable HP Device Manager. With CVE-2020-6927, knowing that the dm_postgres user exists within the default installation of Postgres on HP Device Manager, an attacker could authenticate to the database using this account to elevate privileges and execute commands as SYSTEM. Bloor was able to showcase this in the example below by creating a table in the Postgres database to store command outputs that would be executed using a specially crafted query in the context of the Postgres database (SYSTEM). The output from the query results would be written back to the table which could then be retrieved with an additional query.
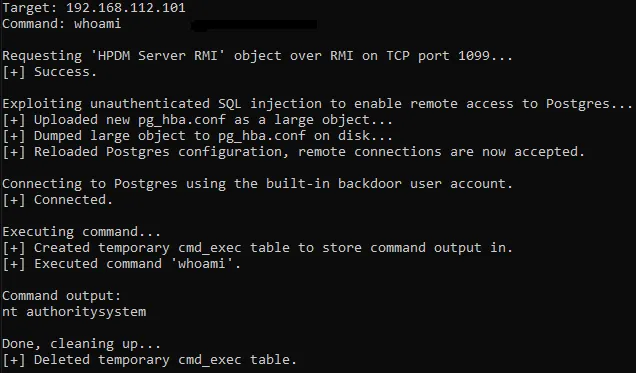
Example of chaining together two vulnerabilities to gain command execution as SYSTEM Image Source: Nick Bloor’s blog post
Proof of concept
At the time this blog post was published, no proof-of-concept (PoC) was available for any of these vulnerabilities. However, Bloor published a blog post containing details about his findings along with a list of steps required in order to exploit the flaw.
The gory details of the HP Device Manager vulnerabilities: https://t.co/UjaVRxu5Og
— Nicky Bloor (@nickstadb) October 5, 2020
Solution
According to HP, two of the three vulnerabilities (CVE-2020-6925, CVE-2020-6926) affect all versions of HP Device Manager.
HP released a fix for the HP Device Manager 5.0.x branch release.
| Affected Versions | Fixed Versions |
|---|---|
| HP Device Manager 4.7 Service Pack 12 and below | To be released in HP Device Manager 4.7 Service Pack 13 |
| HP Device Manager 5.0.0 through 5.0.3 | HP Device Manager 5.0.4 |
While a fix has not been made available for the HP Device Manager 4.7.x release branch, HP anticipates that the fix will arrive in HP Device Manager 4.7 Service Pack 13. We will update this blog once this version becomes available.
If upgrading is not yet feasible at this time, HP suggests applying the following partial mitigations:
- Restrict access to port 1099, 40002 to trusted hosts or localhost
- Change the password for the “dm_postgres” account through the Configuration Manager
- Limit access to port 40006 (Postgres) to localhost only through the Windows Firewall
- Alternatively, remove the “dm_postgres” account from the database altogether
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released.
The Security Response Team would like to thank Nick Bloor for sharing details with us regarding his findings so that we could develop additional plugins to better protect our customers.
Get more information
- HP Security Bulletin for Device Manager Vulnerabilities
- Nick Bloor's Blog Post for HP Device Manager Vulnerabilities
- Twitter Thread from Researcher Nick Bloor on HP Device Manager Vulnerabilities
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management



