Conozca dónde está expuesto y cierre su riesgo crítico
Presentamos Vulnerability Intelligence and Exposure Response (Inteligencia de vulnerabilidades y Respuesta a la exposición), la solución de principio a fin de Tenable para gestionar las exposiciones de vulnerabilidades.
Estas capacidades innovadoras trabajan en conjunto para ayudarle a contextualizar vulnerabilidades, priorizar las acciones que importan y comunicar el progreso al negocio. Permiten a las organizaciones tomar decisiones fundamentadas y basadas en datos con rapidez, movilizar la corrección con tickets bidireccionales y alinear los esfuerzos de seguridad con los objetivos de negocios.
Comience con Tenable
Disfrute el acceso completo a una plataforma moderna para la gestión de vulnerabilidades en la nube, que le permite ver y rastrear todos sus activos con una precisión inigualable. Regístrese ahora.
Gestione las exposiciones de vulnerabilidades con la
solución de gestión de vulnerabilidades n.º 1 del mundo

Tenable Vulnerability Management
Haga surgir las exposiciones clave, enfóquese en las acciones correctas y comunique el progreso con Vulnerability Intelligence and Exposure Response.
Haga surgir las exposiciones clave
Encuentre vulnerabilidades de forma proactiva por nombre o número de CVE, filtrando por grupos de amenazas clave. La búsqueda en lenguaje natural o las consultas complejas descubren rápidamente exposiciones relevantes. La base de datos seleccionada optimiza los procesos, proporcionando visibilidad y contexto de amenazas.
Enfóquese en las acciones que importan
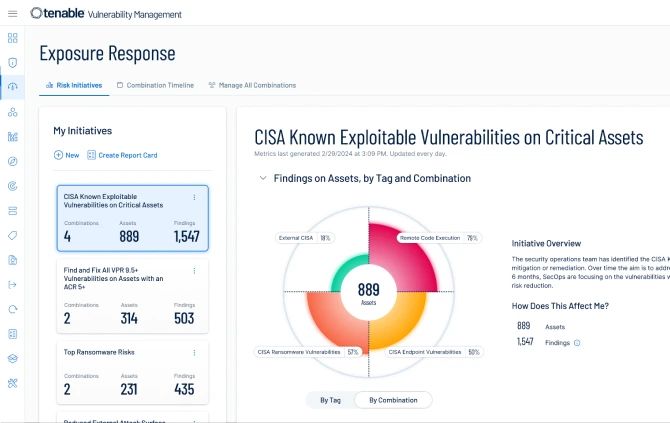
Los detalles de vulnerabilidades, incluyendo puntuaciones, líneas de tiempo y métricas, proporcionan un contexto profundo, empoderándole para priorizar y responder de manera efectiva. Genere iniciativas enfocadas para asegurarse de que se enfoca en las exposiciones que realmente importan.
Comunique el progreso
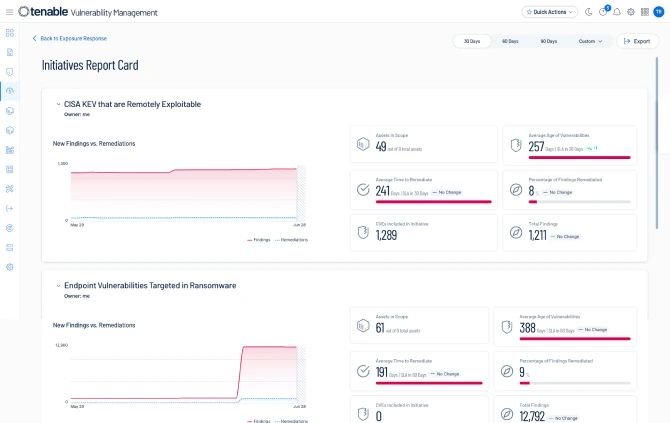
Los informes basados en SLA hacen el seguimiento de la eficacia de los esfuerzos de mitigación, identifican cuellos de botella, ayudan con la asignación de recursos y facilitan las decisiones basadas en datos. Esto garantiza visibilidad y transparencia de cómo las iniciativas de seguridad se alinean con los objetivos generales del negocio.
Identifique las exposiciones, haga el seguimiento del rendimiento y emprenda acción
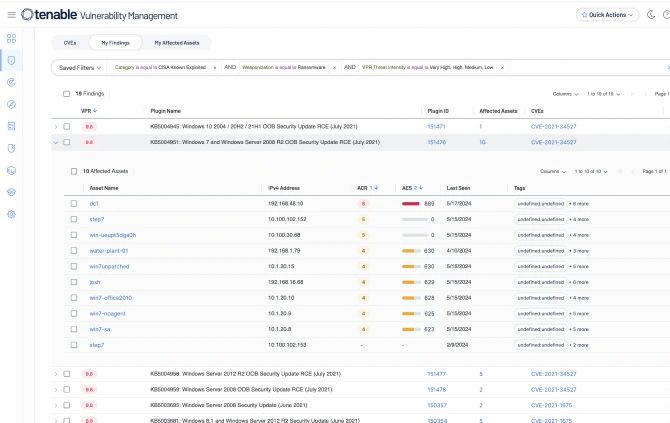
Encuentre fácilmente las vulnerabilidades por nombre o número de CVE, filtre por categorías clave y utilice el lenguaje natural o consultas complejas. La base de datos seleccionada de Vulnerability Intelligence optimiza la visibilidad y el contexto de las amenazas.
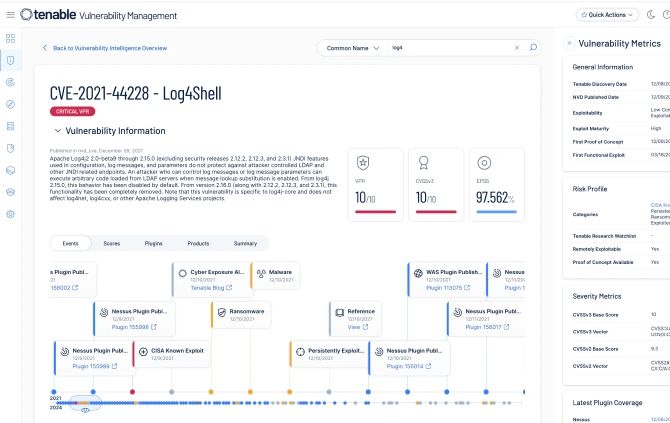
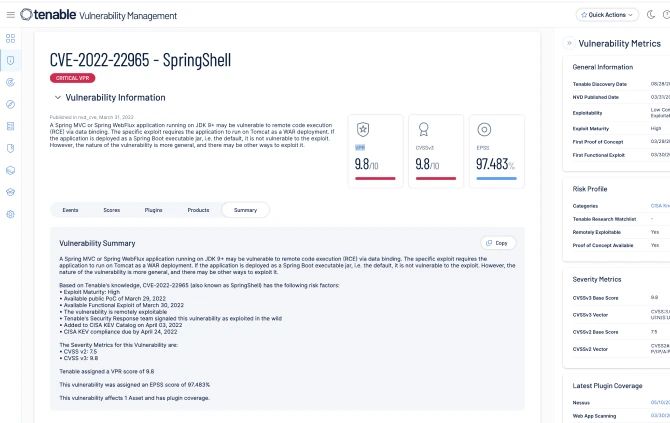
Contextualice las amenazas y los riesgos para priorizar vulnerabilidades críticas. Obtenga información sobre las amenazas emergentes y las vulnerabilidades explotadas con frecuencia. Las páginas de vulnerabilidades detalladas incluyen puntuaciones, plazos y métricas para una priorización y respuesta efectivas.
Priorice con confianza las vulnerabilidades por riesgo. Vea cómo los activos se ven afectados por las CVE e impulse la seguridad proactiva movilizando la corrección directamente hacia sus herramientas ITSM. La información de vulnerabilidades críticas permite tomar decisiones rápidas y fundamentadas, acelerando la respuesta.
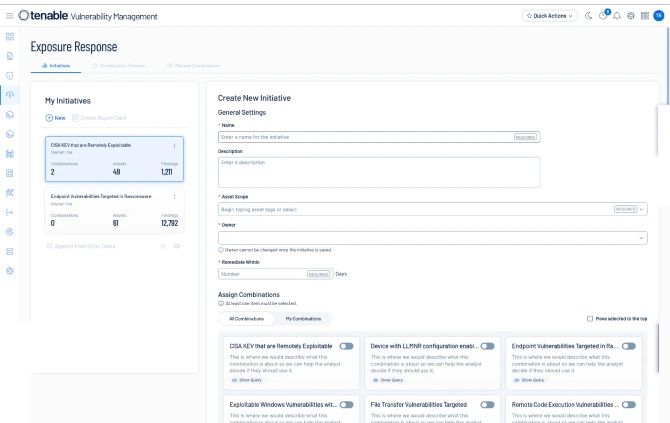
Cree campañas enfocadas, como "Reparar todas las vulnerabilidades externas de ejecución de código remoto", para asegurarse de abordar las exposiciones realmente importantes.
Implemente métricas que pueda lograr y seguir. La visibilidad del rendimiento del equipo frente a las campañas permite a los líderes operacionalizar las prácticas eficazmente y motivar al equipo mediante la automatización de tickets de corrección para plataformas como Jira y ServiceNow ITSM.
Los informes basados en SLA garantizan un seguimiento eficaz de la mitigación, identifican cuellos de botella, ayudan a la asignación de recursos y apoyan las decisiones basadas en datos para iniciativas de seguridad y objetivos de negocios alineados.
Exposición de vulnerabilidades
Exponga y cierre sus debilidades cibernéticas con la solución de gestión de vulnerabilidades n.º 1 en el mundo.





