Martes de parches de Microsoft de septiembre de 2019: Resumen de Tenable

Microsoft’s September 2019 Security Updates address 79 vulnerabilities, 17 of which are rated critical.
Microsoft’s September 2019 Patch Tuesday release contains updates for 79 CVEs, 17 of which are rated critical. In the wake of BlueKeep in May, and the four additional CVEs for Remote Desktop Services in August (DejaBlue), Microsoft has addressed four new CVEs for Remote Desktop Client. Additionally, Microsoft patched two elevation of privilege bugs which have been exploited in the wild this month. The following is a breakdown of the most important CVEs from this month’s release.
CVE-2019-0787, CVE-2019-0788, CVE-2019-1290 and CVE-2019-1291
Remote Desktop Client Remote Code Execution Vulnerability
This month, Microsoft appears to be proactively addressing flaws in Remote Desktop yet again. With four new critical remote code execution (RCE) flaws all attributed to Microsoft it’s clear they are committed to closing holes in the popular service. In the case of each of these CVEs, an attacker who is able to convince a user to connect to an attacker-controlled server can exploit the vulnerability to execute arbitrary code on the machine of the connecting client. While the attacker would have no way to force a user to connect to their malicious server, common techniques such as social engineering, DNS poisoning, or Man in the Middle (MITM) attacks could be used. Currently, Microsoft does not acknowledge any workarounds and notes that the update corrects how the Windows Remote Desktop Client handles connection requests.
CVE-2019-1214
Windows Common Log File System Driver Elevation of Privilege Vulnerability
CVE-2019-1214 is an elevation of privilege vulnerability in the Windows Common Log File System (CLFS) driver. The flaw is caused by an improper handling of objects in memory and, when exploited, could allow an attacker to run a process as a more privileged user. It is important to note that Microsoft cautions that an attacker would first have to log onto the system and execute a specially crafted application in order to take control of an affected system. This vulnerability has reportedly been exploited in the wild and exploitation is more likely with older software releases. Microsoft has released patches for Windows 7 / 2008 R2 including and up to Windows 10 and Server 2016 / 2019.
CVE-2019-1215
Windows Elevation of Privilege Vulnerability
Another elevation of privilege bug that has been exploited in the wild, CVE-2019-1215, is a flaw in how the Winsock IFS Driver (ws2ifsl.sys) handles objects in memory. While an attacker would have to be locally authenticated in order to exploit this, successful exploitation would allow the attack to execute code with elevated privileges.
CVE-2019-1257, CVE-2019-1295 and CVE-2019-1296
Microsoft SharePoint Remote Code Execution Vulnerability
This month brings three RCE vulnerabilities in Microsoft SharePoint. CVE-2019-1257 is a flaw in how SharePoint checks the source markup of an application language. Exploiting this would require the attacker to upload a crafted SharePoint application package to a vulnerable version of SharePoint. Patches were released for SharePoint Foundation 2010 Service Pack 2, 2013 Service Pack 1, SharePoint Enterprise Server 2016 and SharePoint Server 2019.
CVE-2019-1295 and CVE-2019-1296 are both vulnerabilities in SharePoint application programming interfaces (APIs) not properly protected from unsafe user-supplied input. In order to exploit these vulnerabilities, an attacker would have to have access to a susceptible API on an affected version of SharePoint with specially formatted input. An attacker who successfully exploits one of these flaws would be able to execute arbitrary code. While Microsoft notes that exploitation is more likely, exploits for these flaws have not been publicly disclosed.
Additionally, Microsoft also patched several other vulnerabilities in SharePoint:
- CVE-2019-1259 Microsoft SharePoint Spoofing Vulnerability
- CVE-2019-1260 Microsoft SharePoint Elevation of Privilege Vulnerability
- CVE-2019-1261 Microsoft SharePoint Spoofing Vulnerability
- CVE-2019-1262 Microsoft Office SharePoint XSS Vulnerability
CVE-2019-1235
Windows Text Service Framework Elevation of Privilege Vulnerability
Microsoft released a patch for “another class of vulnerabilities” in the Windows Text Service Framework (TSF) that was publicly disclosed by Tavis Ormandy of the Google Project Zero research team in August. CVE-2019-1235 is an elevation of privilege vulnerability due to a lack of validation of inputs and commands sent to the TSF server process. Exploitation requires an attacker to have already logged onto a system before they can deploy a specially crafted application to take control of the system.
CVE-2019-1253
Windows Elevation of Privilege Vulnerability
CVE-2019-1253 is an elevation of privilege vulnerability due to an improper handling of junctions by the Windows AppX Deployment Server. Exploitation requires an attacker to gain the ability to execute an application on a vulnerable system first in order to run a crafted application to elevate privileges. This flaw was publicly disclosed, but, according to Microsoft, exploitation of this flaw is less likely and, given the attacker would need to gain access to a victim’s system first, it is unlikely to be widely exploited.
CVE-2019-1294
Windows Secure Boot Security Feature Bypass Vulnerability
CVE-2019-1294 is another publicly disclosed vulnerability which requires physical access to a system. A security feature bypass exists when Windows Secure Boot fails to properly restrict access to debugging functionality. By exploiting this flaw, an attacker could disclose protected kernel memory. While this exploit does require physical access and most readers might dismiss the flaw over this constraint, this highlights an often overlooked aspect of your organization's security plan: physical security. Proper patch management and regular scanning are every bit as important as making sure physical security controls are in place.
Soluciones Tenable
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name Contains September 2019.
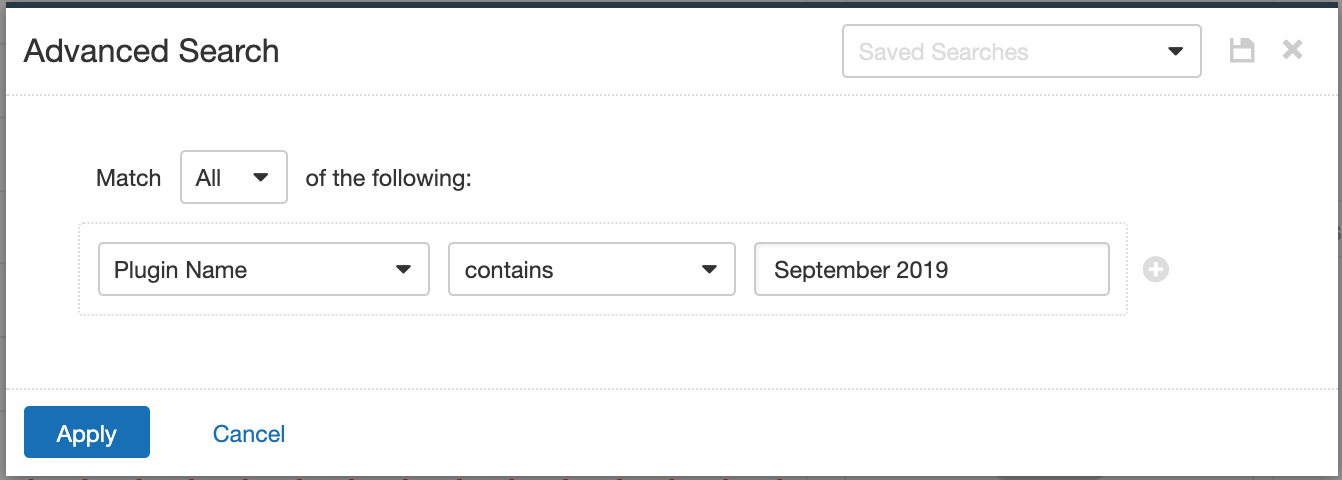
With that filter set, click on the plugin families to the left, and enable each plugin that appears on the right side. Note that if your families on the left say Enabled then that means all of the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
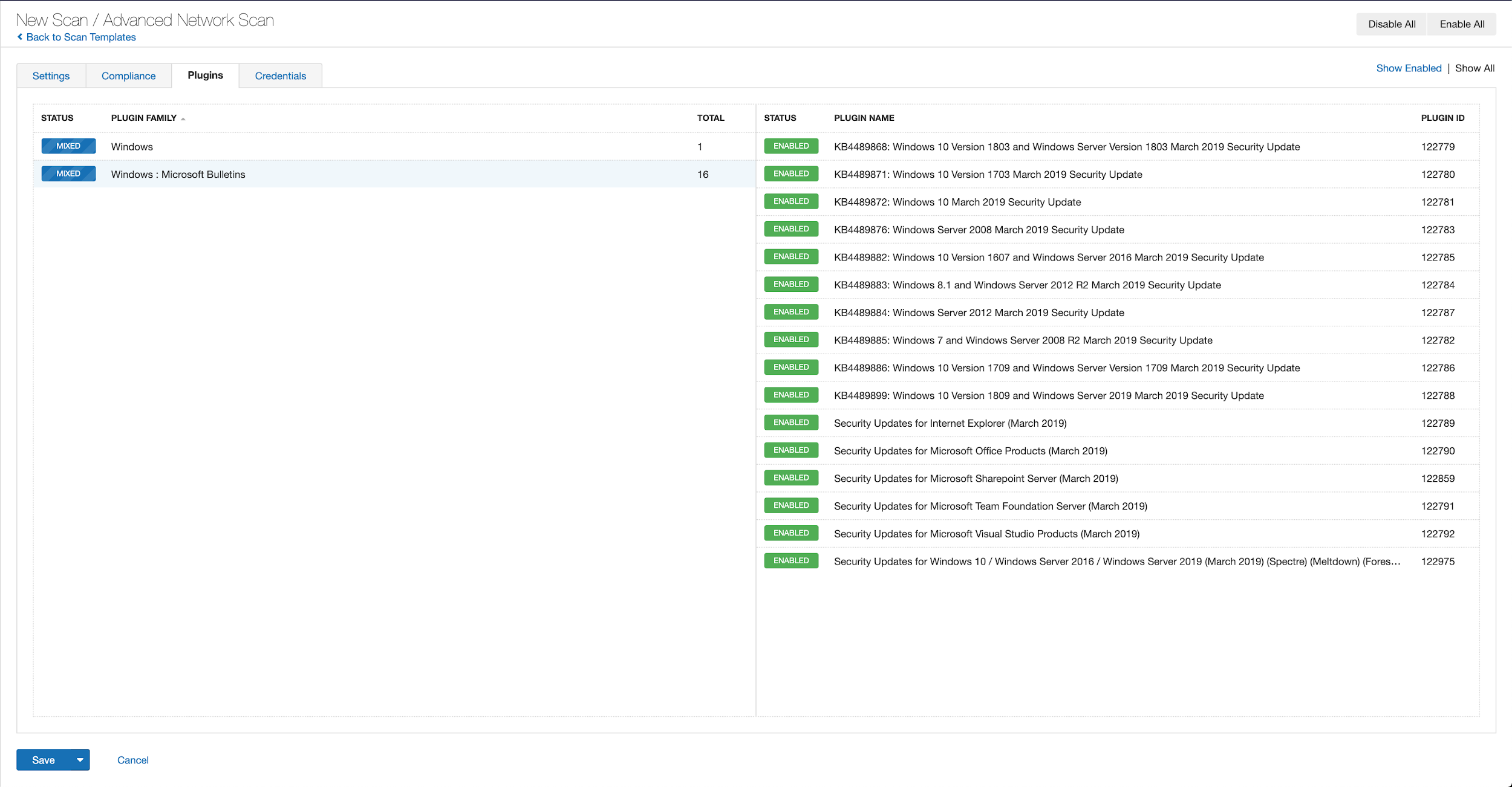
A list of all of the plugins released for Tenable’s September 2019 Patch Tuesday update can be found here. As always we recommend patching systems as soon as possible and regular scanning of your environment to identify those systems that are yet to be patched.
As a reminder, Windows 7 support will be discontinued on January 14, 2020, so we strongly recommend reviewing what hosts remain and any action plans for migration. Plugin ID 11936 (OS Identification) can be useful for identifying hosts that are still running on Windows 7.
Obtenga más información
- Microsoft’s September 2019 Security Updates
- Tenable plugins for Microsoft September 2019 Patch Tuesday Security Updates
Únase al Equipo de respuesta de seguridad de Tenable en Tenable Community.
Obtenga más información sobre Tenable, la primera plataforma de Cyber Exposure para el control integral de la superficie de ataque moderna.
Get a free 60-day trial of Tenable.io Vulnerability Management.
Artículos relacionados
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning






