Martes de parches de Microsoft de octubre de 2019: Resumen de Tenable

Administrators rejoice: only nine of the 59 vulnerabilities in Microsoft's October 2019 Security Update are rated critical.
Microsoft’s October 2019 Patch Tuesday contains updates for 59 CVEs, nine of which are rated critical. Administrators may rejoice this month with a smaller than usual Patch Tuesday. The following is a breakdown of the most important CVEs from this month’s release.
CVE-2019-1333 | Remote Desktop Client Remote Code Execution Vulnerability
CVE-2019-1333 is a remote code execution vulnerability in the Windows Remote Desktop Client. In order to exploit the vulnerability, an attacker would need to entice a user to connect to an attacker-controlled server. While an attacker cannot influence a user to connect to their malicious server, common techniques such as social engineering, DNS poisoning, or Man in the Middle (MiTM) techniques may be used.
CVE-2019-1372 | Azure Stack Remote Code Execution Vulnerability
CVE-2019-1372 is a remote code execution vulnerability in Azure Stack. This is due to not checking the length of a buffer prior to copying the buffer into memory. An attacker could exploit this vulnerability to allow an unprivileged function to execute code outside the sandbox with NT AUTHORITY\system privileges. The security update addresses this flaw by adding additional sanitization to user-supplied inputs.
CVE-2019-1060 | MS XML Remote Code Execution Vulnerability
CVE-2019-1060 is a remote code execution vulnerability in MS XML. The flaw exists when the Microsoft XML Core Services MSXML parser improperly processes user-supplied input. A remote attacker could exploit the vulnerability by enticing a user to browse to a crafted webpage, designed to invoke MSXML in order to run malicious code and take control of the user’s system.
CVE-2019-1238 & CVE-2019-1239 | VBScript Remote Code Execution Vulnerability
CVE-2019-1238 and CVE-2019-1239 are both remote code execution vulnerabilities in the way the VBScript engine handles objects in memory. The vulnerability could corrupt memory in such a way that an attacker could execute arbitrary code in the context of the current user. In order to exploit the issue, an attacker would need to entice a user to visit a specially crafted website in Internet Explorer. The attacker could also host the content on an already compromised website, including websites that host user-provided advertisements. Alternatively, an attacker could embed an ActiveX control in an Office document in order to attempt to exploit these vulnerabilities. While Microsoft says exploitation is less likely, both flaws are rated critical.
Windows 10 1703 End of Life
This month marks the end of life for Windows 10, version 1703 for Enterprise and Education editions. Microsoft’s Windows Lifecycle Fact Sheet notes that support for Home, Pro and Pro for Workstations support ended a year ago on October 9, 2018. However Enterprise and Education editions are now marked as end of service as of today. Plugin ID 118716 can be used to identify the unsupported operating system in your environment.
Soluciones Tenable
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name Contains October 2019.
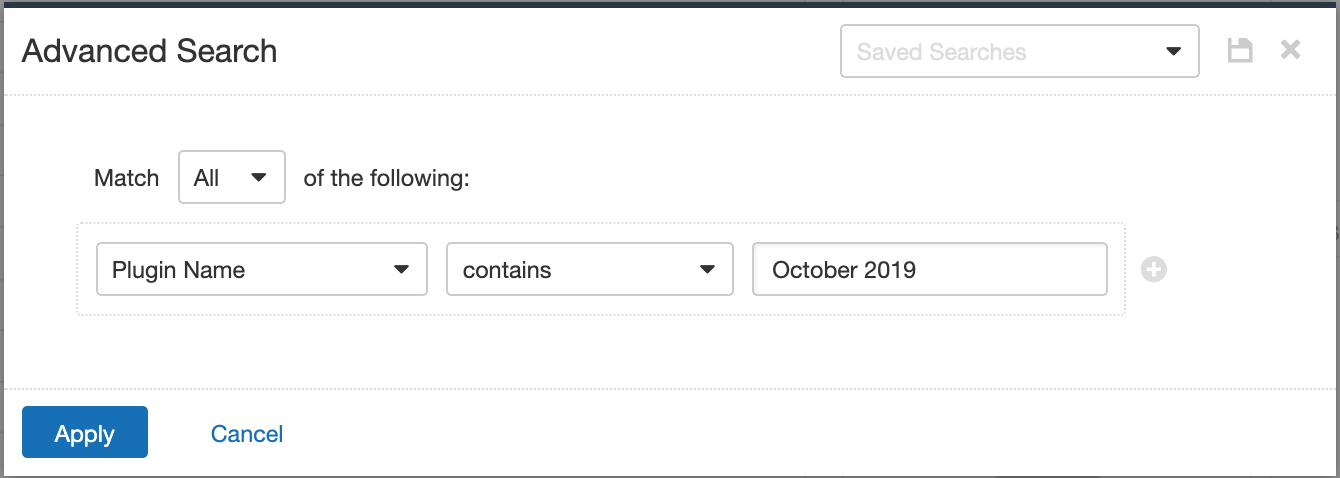
With that filter set, click on the plugin families to the left, and enable each plugin that appears on the right side. Note that if your families on the left say Enabled then that means all of the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable.io:
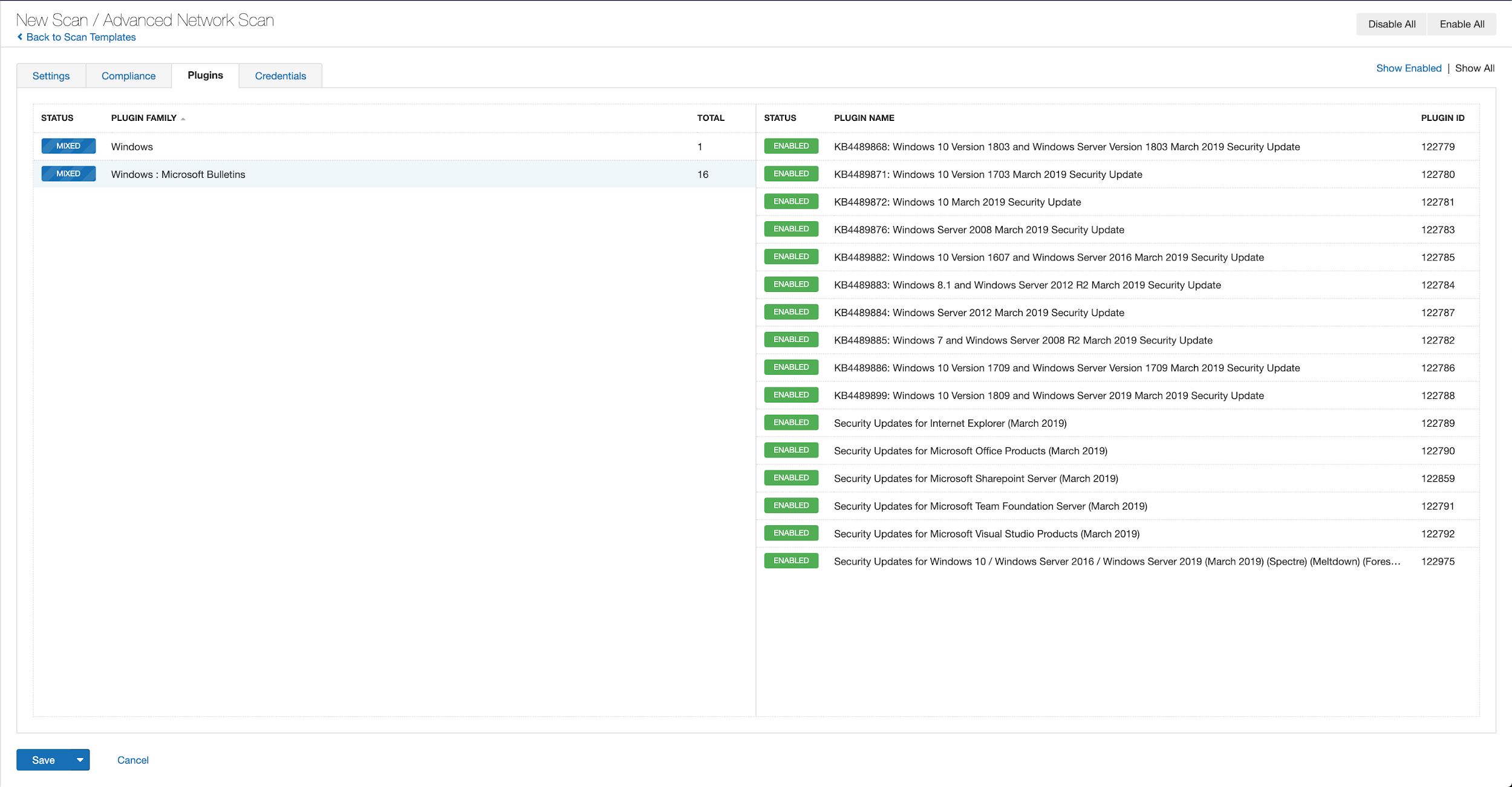
A list of all of the plugins released for Tenable’s October 2019 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems that are yet to be patched.
As a reminder, Windows 7 support will be discontinued on January 14, 2020, so we strongly recommend reviewing what hosts remain and any action plans for migration. Plugin ID 11936 (OS Identification) can be useful for identifying hosts that are still running on Windows 7.
Obtenga más información
- Microsoft’s October 2019 Security Updates
- Tenable plugins for Microsoft October 2019 Patch Tuesday Security Updates
Únase al Equipo de respuesta de seguridad de Tenable en Tenable Community.
Obtenga más información sobre Tenable, la primera plataforma de Cyber Exposure para el control integral de la superficie de ataque moderna.
Get a free 60-day trial of Tenable.io Vulnerability Management.
Artículos relacionados
- Threat Intelligence
- Threat Management
- Vulnerability Management
- Vulnerability Scanning






