by Josef Weiss
November 14, 2016
Monitoring security controls, defences, ongoing compliance, and their effectiveness within a network can be overwhelming for any organisation to manage effectively. Unknown threats and malicious activity could potentially lead to data leakage, vulnerabilities, and damage to critical systems. The Australian Prudential Regulation Authority (APRA) and the associated Prudential Practice Guides (PPG) aims to assist regulated institutions by outlining prudent practices that can aid in managing security risks within specific elements of their business. This dashboard covers key concepts within the PPG CPG 234 guide on overarching framework, addressing topics such as security controls, defence in depth, ongoing compliance, and assessment of effectiveness.
The APRA developed a series of PPGs specifically designed to address specific compliance requirements for regulated institutions. The PPG targets areas where APRA continues to identify weaknesses as part of its ongoing supervisory activities. The PPG does not seek to provide an all-encompassing framework, or to replace or endorse existing industry standards and guidelines. Subject to meeting APRA’s prudential requirements, regulated institutions have the flexibility to manage security risk in IT in a manner best suited to achieving their business objectives. Not all of the practices outlined in this prudential practice guide will be relevant for every regulated institution and some aspects may vary depending upon the size, complexity, and risk profile of the institution. The CPG 234 - Management of Security Risk in Information and Information Technology PPG guide was developed to provide guidance for management and IT security specialists in identifying, targeting, and managing IT security risks.
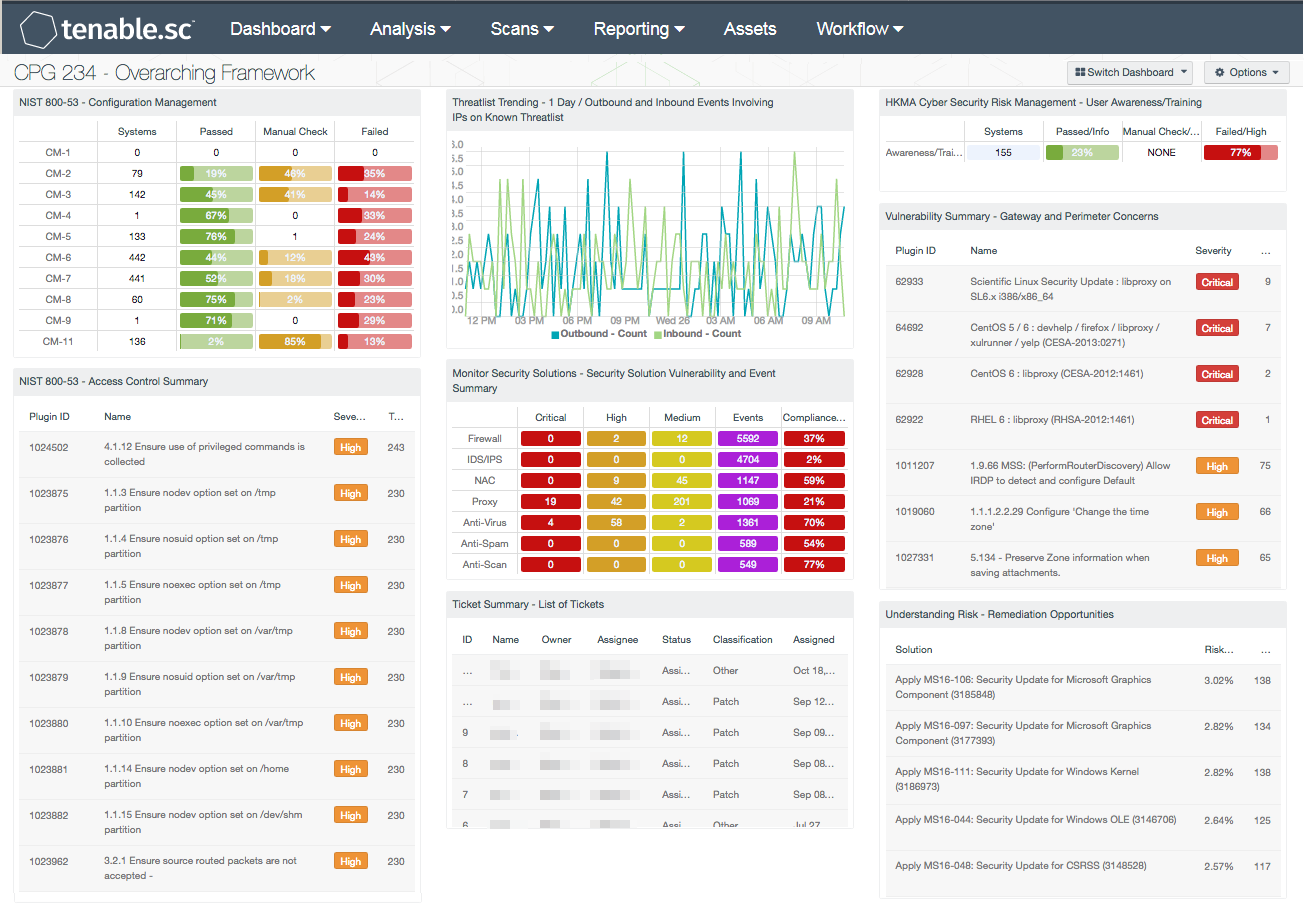
This dashboard covers key concepts within the CPG 234 guide on an overarching framework. The overarching framework addresses topics such as security controls, defence in depth, ongoing compliance, and assessment of effectiveness. These concepts directly align with 21 mitigation strategies from the Australian Signals Directorate (ASD) Top 35 mitigation strategies framework. Included are components that assist the analyst in identifying vulnerability and compliance concerns related to applications and hardening of applications, admin privileges, host and network based ids/ips systems, and workstation and server configuration. The data presented further allows organisations to take a systematic and formalized approach to data risk management.
Additionally, these concepts also align with 21 mitigation strategies from the Australian Signals Directorate (ASD) Top 35 mitigation strategies framework that address patch management vulnerabilities, suspicious behaviour, encryption concerns, and effectiveness of existing controls. Components will alert institutions to gateway and perimeter concerns, inbound and outbound threats, account and access control concerns, and remediation opportunities.
This dashboard is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessment. The dashboard requirements are:
- Nessus 8.5.1
- LCE 6.0.0
- NNM 5.9.0
Tenable Network Security transforms security technology for the business needs of tomorrow through comprehensive solutions that provide continuous visibility and critical context, enabling decisive actions to protect the organisation. Tenable.sc is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audit files. Active scanning examines running systems and services, detects vulnerable software applications, and analyses configuration settings. Passive listening collects data to continuously monitor traffic, collect information about user privilege changes, and administrative activity, along with the discovery of additional vulnerabilities. Monitoring the network to ensure that all systems are secured against vulnerabilities is essential to ongoing security efforts. Tenable enables powerful, yet non-disruptive, continuous monitoring that will enable organisations with the information needed to proactively respond to threats within the enterprise.
The dashboard contains the following components:
- NIST 800-53 - Configuration Management - The Configuration Management family focuses on establishing baselines and identifying the minimum software installations.
- NIST 800-53 - Access Control Summary - The NIST 800-53 Access Control family is a series of controls that determine the settings used for limiting access to systems and information stored on the systems. This component provides a list of the top 10 compliance failures for the Account Management (AC) NIST 800-53 controls.
- Threatlist Trending - 1 Day / Outbound and Inbound Events Involving IPs on Known Threatlist - This component displays line graphs of outbound and inbound events from the “threatlist” event type over the last 24 hours.
- Monitor Security Solutions - Security Solution Vulnerability and Event Summary - This component assists in monitoring security solutions. The matrix presents activity indicators for various security solutions: Firewall, IDS, Anti-virus, Anti-spam, and Anti-scanning.
- Ticket Summary - List of Tickets - This table presents a status summary of tickets issued within the Tenable.sc Ticketing and Alert System. Tickets are a means by which tasks are assigned to users to perform important actions such as vulnerability remediation or incident response.
- HKMA Cyber Security Risk Management - User Awareness/Training - This component helps analysts to measure IT awareness/training and effectiveness, and maps to the HKMA control "(k) User education and awareness".
- Vulnerability Summary - Gateway and Perimeter Concerns - This component presents detected vulnerabilities and compliance concerns pertaining to the network perimeter. These concerns include issues with perimeter devices such as proxy servers, gateway devices, and VPN solutions, as well as DMZ and other perimeter concerns.
- Understanding Risk - Remediation Opportunities - This table displays the top remediations for the network. For each remediation, the risk reduction for the network if the remediation is implemented is shown, along with the number of hosts affected.